Is your cellphone all of the sudden flooded with aggressive advertisements, slowing down efficiency or resulting in uncommon app habits? Right here’s what to do.
08 Aug 2025
•
,
5 min. learn

There are numerous unhealthy issues that might find yourself in your smartphone. Spyware and adware designed to show your cellphone right into a secret surveillance machine. Trojans that might harvest your banking logins or bank card information, probably by way of a novel methodology that relays NFC information from victims’ cost playing cards. And even ransomware designed to lock you out of your machine fully till a ransom is paid.
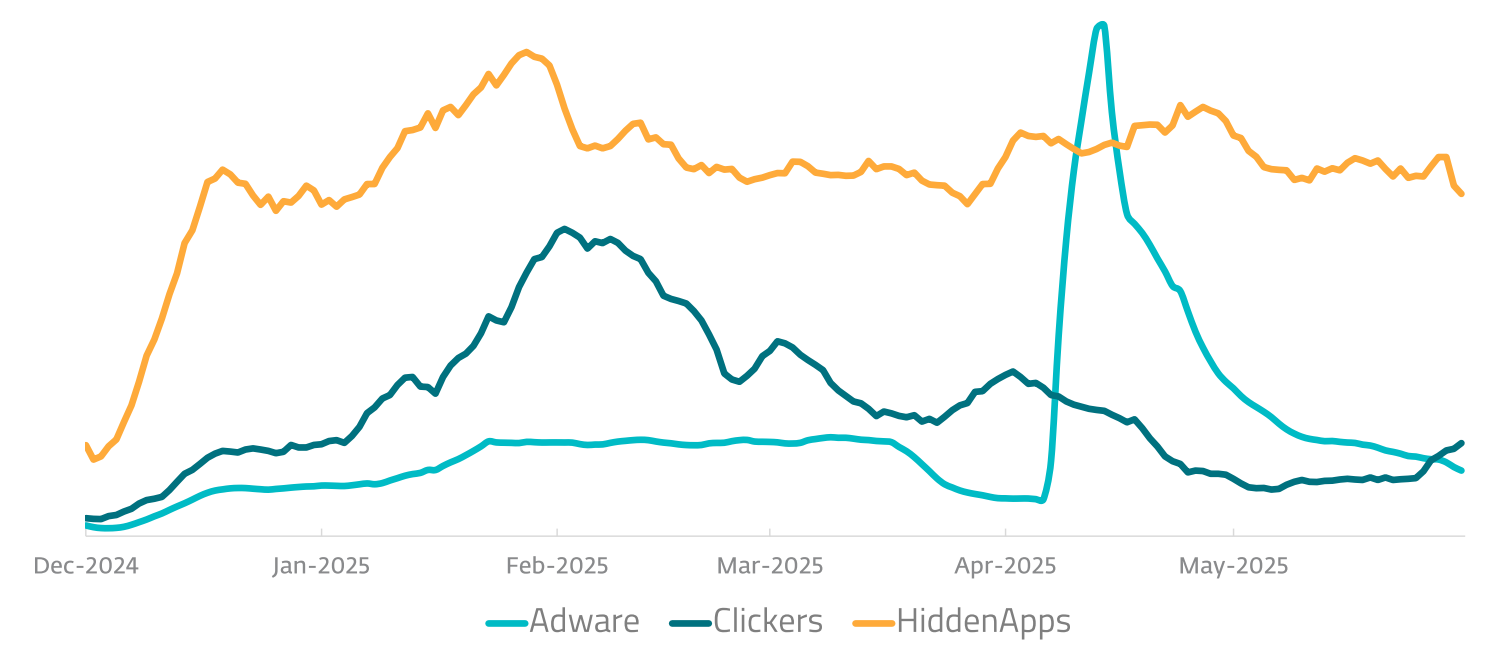
On this context, adware, which shows undesirable ads, might sound fairly innocuous. However in actuality, it’s not one thing that must be dismissed, both. Adware detections surged by 160% within the first half of 2025, in keeping with ESET’s newest menace report. Learn on to be taught extra about how adware works, and how one can hold your Android machine adware-free.
What’s adware and the way does it work?
Adware occupies one thing of a gray space within the menace panorama. At one finish of the spectrum is reliable free software program which will include advertisements that are onerous to modify off. Annoying, however not malicious. Subsequent come doubtlessly undesirable purposes/packages (PUAs/PUPs), which show intrusive advertisements and modify your machine settings. A extra dangerous kind of PUP/PUA might do that in addition to different nefarious actions, reminiscent of stealing some private information.
Typically, “adware” refers to any undesirable or doubtlessly malicious software program that shows intrusive advertisements in your machine with out your consent. These may very well be pop-ups, in-browser advertisements, banner advertisements, push notifications, and even full-screen content material, together with movies. The tip objective for the developer is often to generate income by tricking you into putting in the adware, and viewing or clicking on these advertisements.
As well as, these sorts of threats may additionally:
- observe your on-line exercise to personalize promoting
- harvest private data to promote to 3rd events
- mechanically click on on advertisements with out your data in click on fraud schemes (a class we name “Clickers”)
- disguise itself after set up to forestall you eradicating it (what we name “Hidden Apps”)
- burn up your information allowance
- decelerate the efficiency of your machine
- open the door to malware
How does it get in your machine?
Adware builders have devised varied methods to trick you into putting in adware. These embody:
- disguising it as a reliable app
- bundling it with a chunk of freeware
- exploiting vulnerabilities in your machine software program or OS by way of a drive-by-download
- tricking you into clicking on a deceptive or malicious advert
- pretend pop-ups (e.g., which falsely declare your machine is compromised with malware)
- phishing hyperlinks, both despatched by way of e-mail, textual content or social media messages
Evasion methods
Adware builders additionally go to some lengths to evade detection by unsuspecting cell customers and safety instruments. As talked about, they might disguise the adware in “reliable” free software program, or disguise it as a legit app. They might additionally disguise it as a pretend replace on your cellphone.
The code itself could also be encrypted to forestall primary AV instruments from scanning and blocking it. Or it may very well be usually up to date utilizing polymorphic methods, which make it tough for some instruments to detect. Builders might even use anti-analysis methods, which make it more durable for safety researchers to find out how their adware variant works.
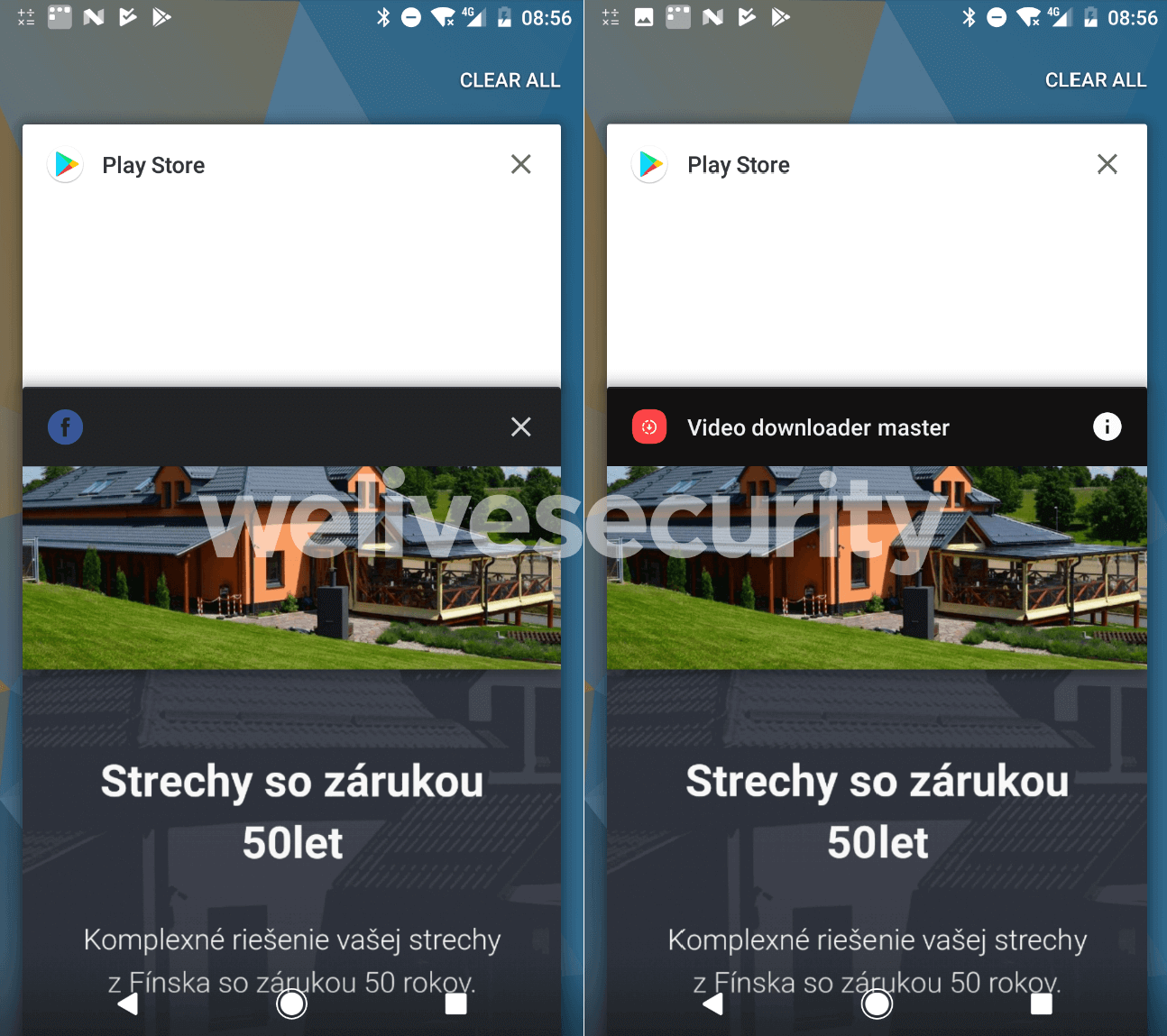
Introducing Kaleidoscope
One notably subtle adware variant found not too long ago by ESET has been dubbed Kaleidoscope. This Android-based advert fraud marketing campaign makes use of an “evil twin” tactic whereby its builders create two equivalent variations of the identical app. One benign model is circulated on the official app retailer, whereas a malicious twin model is distributed on unofficial third-party shops. They use misleading advertisements to direct victims to the latter.
Crucially, each variations have the identical app title and distinctive identifier (app ID). Which means the fraudulent advert impressions generated by the “evil” model are judged by advertisers to be reliable. It helps the builders to maintain the income rolling in, whereas victims are bombarded by advertisements which decelerate their machine. The adware accounted for over 1 / 4 (28%) of detections throughout the Android adware class in H1 2025.
Do I’ve adware on my machine?
To search out out in case your Android machine could also be compromised, test for the next warning sigs:
- Gradual efficiency and system crashes
- The looks of recent extensions and toolbars
- Net pages that don’t show correctly
- Undesirable software program in your machine
- Extreme and intrusive advertisements
- Your browser homepage altering with out your permission
- Fast battery drain
- Excessive and unexplained information utilization
Find out how to head off adware
Fortuitously, there are numerous methods to mitigate the dangers posed by adware. The best route is to forestall it from putting in within the first place. Contemplate the next:
- Solely obtain apps from respected builders – all the time test their score and opinions.
- Test app opinions earlier than downloading.
- All the time keep on with the Google Play retailer, avoiding downloads from any third-party app shops the place malware is extra prevalent.
- Keep away from clicking on advertisements or pop- ups, in case they’re malicious.
- Apply common updates to your OS and browser, to make sure there are not any vulnerabilities that may very well be exploited to put in adware in your machine.
- Be alert to the specter of phishing: by no means click on on hyperlinks in unsolicited emails/texts/social messages.
- Set up safety software program from a trusted vendor, hold it up to date and, the place relevant, ensure that PUA detections are enabled.
If you happen to suppose your machine might have already been compromised with adware, disconnect your machine from Wi-Fi and cell information. Reboot it in Secure Mode (this may range from machine to machine), then go to Settings > Apps and notifications > See all apps and uninstall something that appears suspicious. It could even be essential to clear your browser cache and cookies.
Alternatively, run a scan with respected safety software program like ESET Cell Safety, which, so long as you observe the advice to allow PUA detections, will go a good distance towards serving to you avoid adware.