An summary of the actions of chosen APT teams investigated and analyzed by ESET Analysis in Q2 2025 and Q3 2025
06 Nov 2025
•
,
4 min. learn

ESET APT Exercise Report Q2 2025–Q3 2025 summarizes notable actions of chosen superior persistent risk (APT) teams that have been documented by ESET researchers from April by way of September 2025. The highlighted operations are consultant of the broader panorama of threats we investigated throughout this era. They illustrate the important thing traits and developments and comprise solely a small fraction of the cybersecurity intelligence knowledge offered to clients of ESET APT reviews.
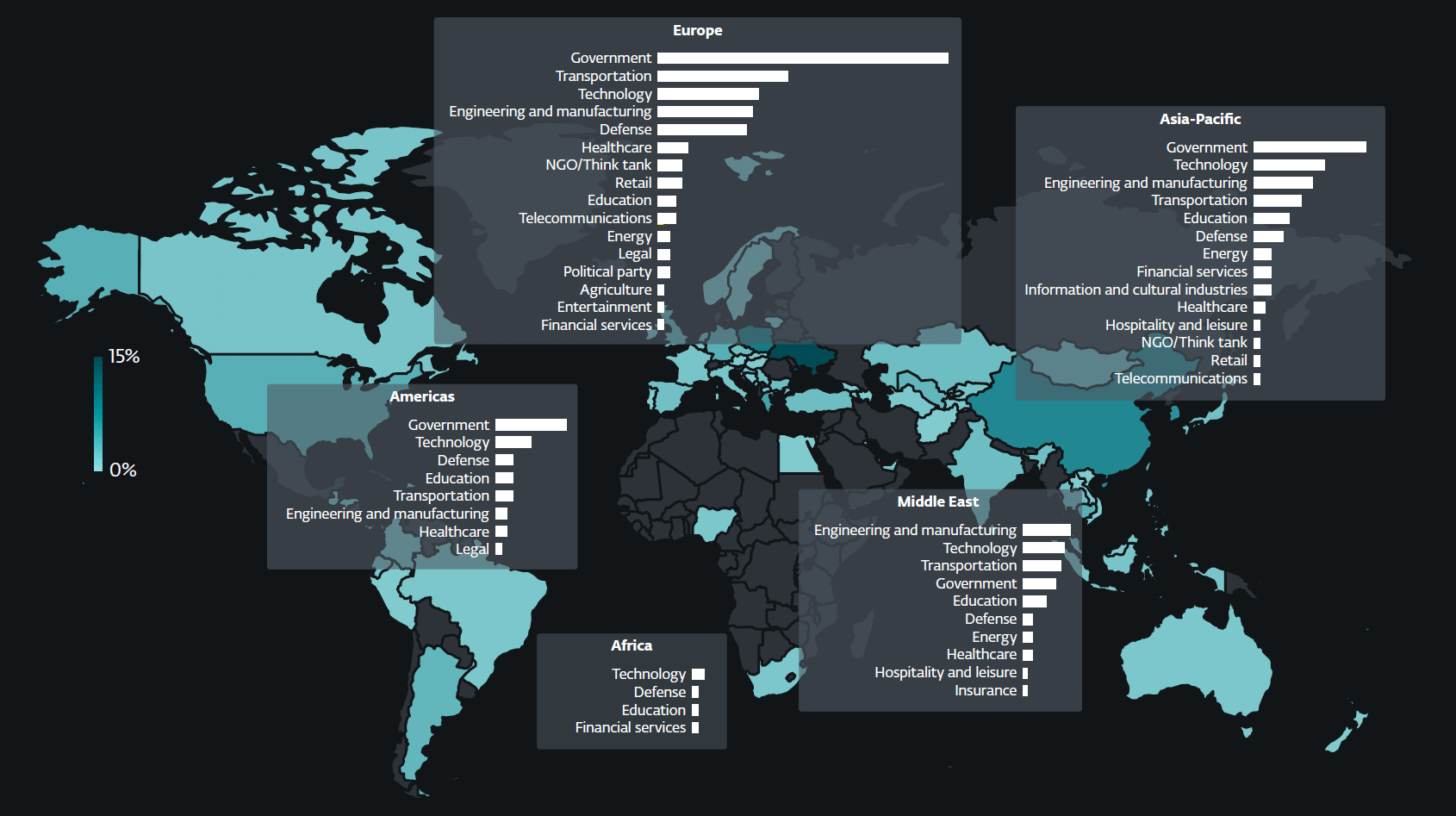
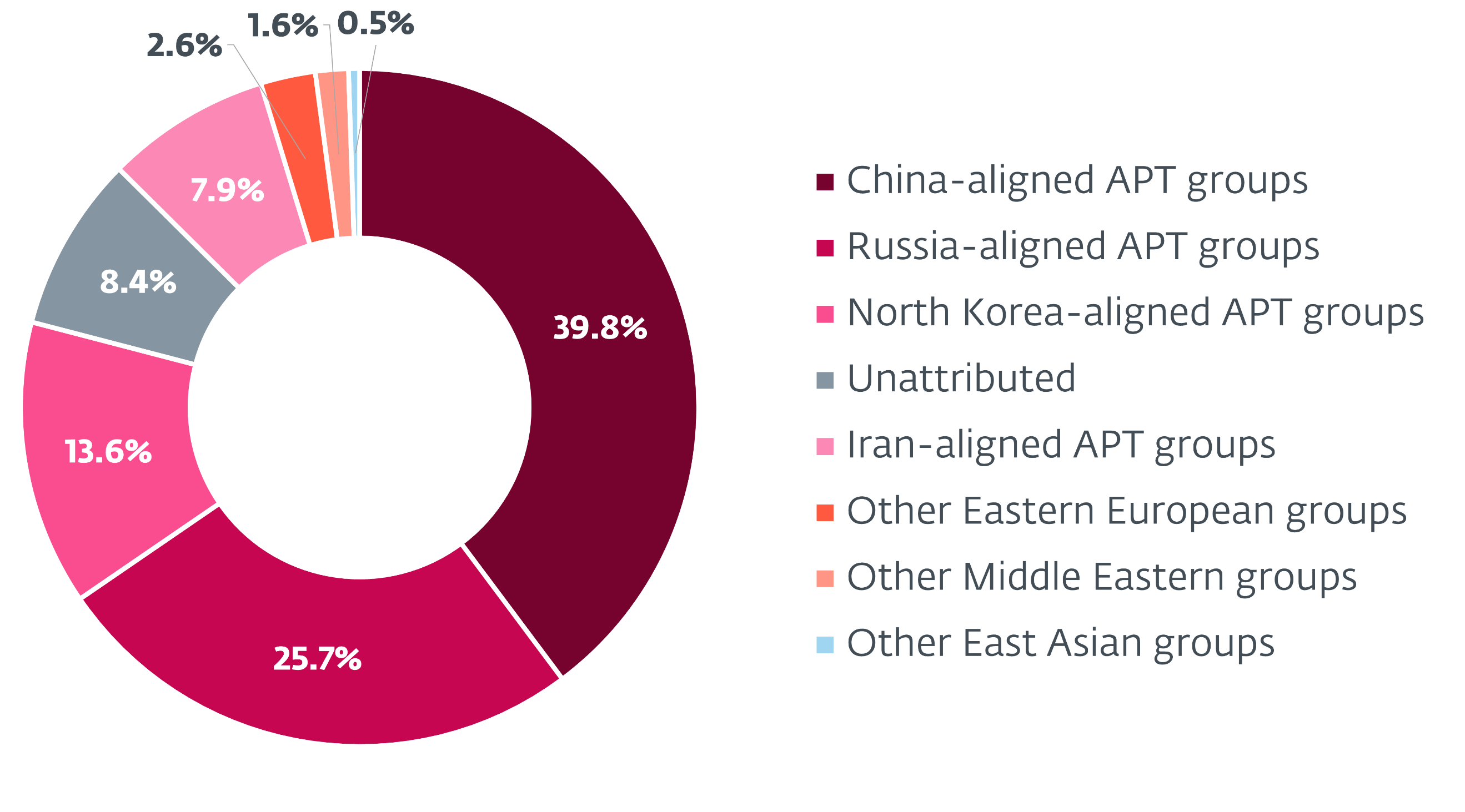
Through the monitored interval, China-aligned APT teams continued to advance Beijing’s geopolitical goals. We noticed an rising use of the adversary-in-the-middle method for each preliminary entry and lateral motion, employed by teams resembling PlushDaemon, SinisterEye, Evasive Panda, and TheWizards. In what seems to be a response to the Trump administration’s strategic curiosity in Latin America, and probably additionally influenced by the continuing US‑China energy battle, FamousSparrow launched into a tour of Latin America, focusing on a number of governmental entities within the area. Mustang Panda remained extremely energetic in Southeast Asia, america, and Europe, specializing in the governmental, engineering, and maritime transport sectors. Flax Hurricane focused the healthcare sector in Taiwan by exploiting public-facing net servers and deploying webshells to compromise its victims. The group ceaselessly maintains its SoftEther VPN infrastructure, and it additionally began utilizing an open-source proxy, BUUT. In the meantime, Speccom focused the power sector in Central Asia with the presumed intention of gaining better visibility into Chinese language-funded operations and decreasing China’s dependency on maritime imports. One of many backdoors within the group’s toolset, BLOODALCHEMY, seems to be favored by a number of China-aligned risk actors.
We noticed a continued improve in spearphishing actions of the Iran-aligned MuddyWater. The group adopted the strategy of sending spearphishing emails internally – from compromised inboxes inside the goal group – with a notably excessive success fee. Different Iran-aligned teams remained energetic: BladedFeline adopted new infrastructure, whereas GalaxyGato deployed an improved C5 backdoor. GalaxyGato additionally launched an fascinating twist to its marketing campaign by leveraging DLL-search-order hijacking to steal credentials.
North Korea-aligned risk actors focused the cryptocurrency sector and, notably, expanded their operations to Uzbekistan – a rustic not beforehand noticed of their scope. In latest months, we’ve got documented a number of new campaigns carried out by DeceptiveDevelopment, Lazarus, Kimsuky, and Konni, with the intention of espionage, advancing Pyongyang’s geopolitical priorities, and producing income for the regime. Kimsuky experimented with the ClickFix method to focus on diplomatic entities, and South Korean suppose tanks and academia, whereas Konni used social engineering with an uncommon deal with macOS programs.
Russia-aligned teams maintained their deal with Ukraine and nations with strategic ties to Ukraine, whereas additionally increasing their operations to European entities. Spearphishing remained their main technique of compromise. Notably, RomCom exploited a zero-day vulnerability in WinRAR to deploy malicious DLLs and ship a wide range of backdoors. We reported this vulnerability to WinRAR, which promptly patched it. The group’s exercise was largely targeted on the monetary, manufacturing, protection, and logistics sectors within the EU and Canada. Gamaredon remained probably the most energetic APT group focusing on Ukraine, with a noticeable improve in depth and frequency of its operations. This surge in exercise coincided with a uncommon occasion of cooperation between Russia-aligned APT teams, as Gamaredon selectively deployed one among Turla’s backdoors. Gamaredon’s toolset, probably additionally spurred by the collaboration, continued to evolve, for instance, by way of the incorporation of recent file stealers or tunneling companies.
Sandworm, just like Gamaredon, targeted on Ukraine – albeit with motives of destruction fairly than cyberespionage. The group deployed knowledge wipers (ZEROLOT, Sting) in opposition to governmental entities, corporations within the power and logistics sectors, and, extra notably, in opposition to the grain sector – the seemingly goal being the weakening of the Ukrainian financial system. One other Russia-aligned risk actor, InedibleOchotense, carried out a spearphishing marketing campaign impersonating ESET. This marketing campaign concerned emails and Sign messages delivering a trojanized ESET installer that results in the obtain of a respectable ESET product together with the Kalambur backdoor.
Lastly, notable actions by lesser-known teams included FrostyNeighbor exploiting an XSS vulnerability in Roundcube. Polish and Lithuanian corporations have been focused by spearphishing emails that impersonated Polish companies. The emails contained a particular use and mixture of bullet factors and emojis, a construction harking back to AI-generated content material, suggesting potential use of AI within the marketing campaign. Delivered payloads included a credential stealer and an electronic mail message stealer. We additionally recognized a beforehand unknown Android spy ware household in Iraq, which we named Wibag. Masquerading because the YouTube app, Wibag targets messaging platforms resembling Telegram and WhatsApp, in addition to Instagram, Fb, and Snapchat. Its capabilities embody keylogging and the exfiltration of SMS messages, name logs, location knowledge, contacts, display recordings, and recordings of WhatsApp calls and common cellphone calls. Apparently, the login web page for the spy ware’s admin panel shows the brand of the Iraqi Nationwide Safety Service.
Malicious actions described in ESET APT Exercise Report Q2 2025–Q3 2025 are detected by ESET merchandise; shared intelligence is primarily based on proprietary ESET telemetry knowledge and has been verified by ESET researchers.
ESET APT Exercise Experiences comprise solely a fraction of the cybersecurity intelligence knowledge offered in ESET Risk Intelligence APT Experiences. For extra info, go to the ESET Risk Intelligence web site.











