E-mail safety greatest practices have not modified a lot through the years: Use sturdy passwords, block spam, do not belief presents that appear too good to be true and confirm requests — even from identified entities.
These longstanding practices, nevertheless, haven’t stopped e mail from being a big safety vulnerability. CISA reported that greater than 90% of profitable cyberattacks start with a phishing e mail, making it one of many riskiest instruments utilized by enterprises at present. The problem has been compounded by a 131% year-over-year enhance in emails containing malware, in keeping with a 2026 Hornetsecurity report, with phishing remaining the main an infection vector at 46%, adopted by compromised credentials at 25%.
To stop these dangers, organizations should comply with a powerful set of e mail safety greatest practices. Organizations ought to share the next steering with their workers and implement applicable controls and applied sciences to guard this very important technique of communication.
Create sturdy passwords
One of the necessary e mail safety greatest practices is to make use of sturdy passwords. Password safety recommendation has modified lately. Earlier pondering was that advanced equaled sturdy. However forcing workers to create advanced passwords, resembling }m}{4p#P@R9w, normally ends with customers writing their passwords on a sticky notice or saving them in an insecure file on their desktops.
NIST maintains that password size, not complexity, is the important thing to password power. Utilizing passphrases — the stringing collectively of some phrases, resembling kittEnsarEadorablE — is one technique to create longer, easy-to-remember but difficult-to-guess passwords that assist defend towards attackers who use dictionary assaults to focus on weak passwords.
Should you plug these two examples into Safety.org’s How Safe Is My Password? software, you will discover that }m}{4p#P@R9w would take 400,000 years for a pc to crack, whereas kittEnsarEadorablE would take 6 trillion years.
Stronger passphrases embrace strings of unrelated phrases. For instance, per Safety.org’s calculator, the passphrase authoRbeacHkeyboarD would take 300 trillion years for a pc to guess.
Advocate workers use passphrases and, as a corporation, create a firm password coverage that communicates password necessities and expectations.
Do not reuse passwords throughout accounts
Password reuse is a serious safety menace. Malicious actors know that making an attempt a reused password on a breached system typically unlocks different accounts. Subsequently, if an attacker compromises an account that makes use of the identical credentials as others, the attacker can simply achieve entry to these different accounts. Password reuse is particularly harmful when workers use the identical passwords for company and private accounts.
Encourage workers to comply with password hygiene greatest practices, together with creating sturdy, distinctive passwords or passphrases for every account. This can be a ache level for a lot of customers, particularly these with dozens or a whole lot of logins to recollect. Use single sign-on or a password supervisor to assist alleviate the problem.
Contemplate altering passwords usually — or not
The frequency of password adjustments has been a subject of debate over the previous decade. Altering passwords each 90 days was once the norm. The belief was that frequent password adjustments assist preserve techniques safe, however in actuality, they typically result in person frustration and using much less safe passwords. Most of the time, Password1 turns into Password2 after 90 days.
NIST has now advisable towards forcing periodic password adjustments except a corporation has purpose to suspect a compromise or information breach. Be aware, nevertheless, that some compliance laws, resembling PCI DSS, require frequent password adjustments.
Corporations should weigh the advantages of standard password adjustments towards workers’ tendency to make use of weaker passwords which are simpler to recollect and, due to this fact, simpler for attackers to take advantage of.
Use MFA
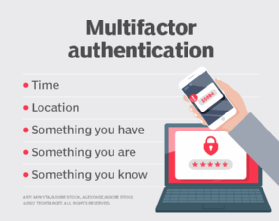
MFA entails utilizing a couple of technique to authenticate a person’s id. For instance, a username and password together with a one-time password or fingerprint biometric. Including a second — or third, or extra — issue to the authentication course of provides a layer of protection and helps mitigate frequent e mail threats, resembling brute-force assaults and password cracking. Microsoft reported that utilizing MFA can assist forestall 99% of credential-based assaults.
Mandate using MFA and advocate that workers shield their private accounts with MFA wherever accessible. Contemplate adopting phishing-resistant MFA. This method makes use of strategies which are proof against MFA bypass assaults, resembling push bombing and SIM swapping.
Discover ways to spot phishing scams
Whereas e mail safety merchandise filter many spam emails, a big quantity nonetheless attain workers’ inboxes. These undesirable messages can comprise more and more subtle phishing, spear phishing or whaling assaults.
The most effective methods for workers to maintain their e mail safe is to know how phishing works. Train workers the next telltale indicators of phishing scams throughout safety consciousness coaching:
- Typos. Many phishing emails comprise grammatical errors or misspelled phrases.
- Sender e mail handle. Phishing emails typically come from spoofed or incorrect e mail addresses.
- Generic greetings. Be cautious of emails to “Expensive” or “Buyer,” or that lack a salutation altogether.
- Requests for information. By no means belief an unsolicited e mail that requests private, company or monetary information.
- Impersonators. Phishing scams have developed into assaults that impersonate identified customers and workers. At all times confirm sender legitimacy.
Inform workers to make use of warning when opening probably malicious emails and to by no means reply to, click on hyperlinks in or open attachments from emails that seem suspicious.
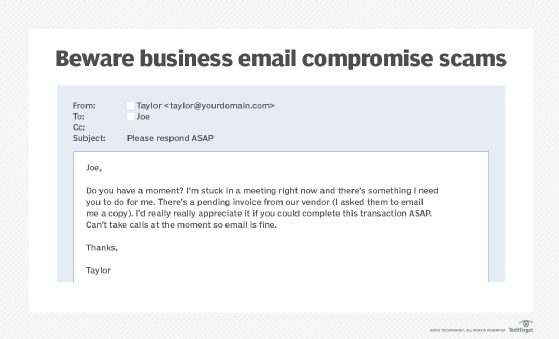
Be looking out for impersonators
Enterprise e mail compromise (BEC) is an more and more standard tactic that malicious actors use to take advantage of organizations. These extremely focused campaigns contain attackers impersonating C-level executives or trusted companions to trick workers into performing actions resembling transferring cash or sharing delicate information.
Train workers learn how to spot BEC scams. For instance, instruct customers to be looking out for emails that convey a way of urgency, ask for uncommon transactions or comprise different phishing traits. Advise workers to double-check the legitimacy of a request at any time when doubtful.
Be cautious of e mail attachments
Many e mail assaults depend on the flexibility to ship and obtain attachments that comprise malicious executable code. E-mail safety gateways and antimalware software program detect malicious sources and block most malicious attachments. These attachments, nevertheless, may also come from trusted sources whose credentials have been exploited by attackers.
Workers ought to be cautious of attachments, even when the group makes use of email-scanning and malware-blocking software program. Inform them to make use of additional vigilance earlier than opening an attachment that has an extension related to an executable program, resembling EXE (executable file), JAR (Java software file) or MSI (Home windows Installer). Information resembling Phrase paperwork, spreadsheets and PDFs may also carry malicious code, so advise customers to train warning when dealing with any kind of connected file. Scan information with an antimalware program or keep away from opening them altogether. If workers are uncertain if an attachment is reputable, advise them to contact their supervisor and the IT division.
Do not click on e mail hyperlinks
Hyperlinks in emails can hook up with an internet area completely different from the one they seem to characterize. Some hyperlinks may show a recognizable area identify — resembling www.techtarget.com — however, in reality, direct the person to a special, malicious area. Attackers additionally use worldwide character units or misspellings to create malicious domains that seem like these of well-known manufacturers.
Advise workers to all the time evaluate hyperlink contents by hovering the mouse pointer over the hyperlink to see if the precise hyperlink is completely different from the displayed hyperlink. Be aware that even this may be spoofed — although most trendy e mail applications ought to catch such hyperlinks. When doubtful, customers ought to kind domains immediately into the browsers to keep away from clicking hyperlinks in emails.
Do not use enterprise e mail for private use and vice versa
Whereas it may be tempting and handy for workers to make use of their company e mail account for private issues, an enterprise e mail safety greatest follow is to ban this. Likewise, do not ship work-related emails from private accounts. Mixing enterprise and private accounts can expose them to threats resembling spear phishing. Define acceptable e mail use insurance policies and restrictions in a company e mail coverage.
Solely use company e mail on accepted gadgets
Customers can entry e mail from virtually wherever and on any internet-connected system. Whereas handy for workers, this might turn into a safety catastrophe for a corporation. If firm e mail is opened on gadgets that do not have the right safety controls, attackers may exfiltrate customers’ credentials, e mail and information. Require workers to entry e mail solely on company-approved and trusted gadgets.
Encrypt e mail, communications and attachments
An e mail is sort of a postcard: Each individual and system that it comes into contact with can see its message. E-mail encryption solves this drawback, making certain that anybody who intercepts the e-mail can’t learn its contents. This helps forestall many e mail safety points, resembling man-in-the-middle and BEC assaults. Most main e mail companies supply encryption capabilities.
Encrypting the message is not sufficient, nevertheless. Additionally encrypt communications between the group and the e-mail supplier. Encrypt attachments as properly, even when the e-mail they’re connected to is encrypted.
Again up e mail
Advocate that workers again up necessary emails to a safe location. This ensures important e mail communications stay accessible within the occasion of a safety incident, resembling a ransomware assault.
Keep away from public Wi-Fi
Workers may see public Wi-Fi as a blessing, however they need to be reminded that these connections are weak to assaults. If workers log into company e mail on public Wi-Fi, anybody on that community may additionally entry their e mail. Malicious actors can use open supply packet sniffers, resembling Wireshark, to observe and achieve entry to private data over e mail. Even when customers do not actively test e mail on public Wi-Fi, nearly each system is ready to robotically replace inboxes when a tool connects to a community. If customers are on Wi-Fi, so is their e mail, placing account credentials in danger.
Instruct workers to solely hook up with safe, identified Wi-Fi networks.
Use e mail safety protocols
The next three e mail safety requirements are key to filtering spam messages:
- DomainKeys Recognized Mail. The DKIM normal makes use of uneven cryptography to forestall e mail spoofing. A digital signature added to an e mail verifies the message was not altered after it was despatched. If the signature would not match the e-mail area’s public key, it’s blocked. If it does match, it’s delivered.
- Sender Coverage Framework. SPF verifies that an e mail got here from its supply and is allowed to ship an e mail from that area. If verified, the e-mail will get delivered. If not, the e-mail is blocked.
- Area-based Message Authentication, Reporting and Conformance. The DMARC protocol extends DKIM and SPF. Utilizing DMARC, area homeowners can publish their DKIM and SPF necessities, in addition to specify what occurs when an e mail fails to fulfill these necessities, resembling reporting again to the sending area.
Whereas these technical controls forestall spoofed emails, they don’t cease all undesirable messages.
Implement the precept of least privilege
Whereas circuitously associated to solely e mail safety, organizations ought to undertake POLP to restrict workers’ entry rights to solely these required to do their jobs. If an worker’s credentials are compromised, POLP can assist forestall attackers from gaining full entry to all the firm’s sources.
Use e mail safety instruments
Past implementing the right protocols, organizations ought to create a layered e mail safety technique that features a number of instruments. For instance, think about adopting antimalware, antispam, antivirus, e mail filtering, e mail safety gateways, firewalls, cell system administration, information loss prevention and endpoint safety instruments, resembling endpoint safety platforms, endpoint detection and response, and prolonged detection and response.
Moreover, use e mail monitoring techniques to detect potential insider threats and compromised accounts. These instruments alert safety groups to the next:
- Out-of-the-ordinary person behaviors, resembling logging in from uncommon areas or exterior of standard enterprise hours.
- Suspicious e mail patterns, resembling adjustments in show names, message tone or requests for delicate information.
- E-mail content material, resembling malicious hyperlinks or attachments containing delicate information.
- Different menace indicators, resembling giant numbers of attachments being despatched, which could point out information exfiltration, or suspect URLs and IP addresses, which could point out communication with an attacker’s area or command-and-control server.
Lock gadgets and sign off of e mail
Advise workers to lock their gadgets when not in use. Leaving e mail open on gadgets which are accessible to others is a safety danger. Additionally, urge workers to sign off of their e mail when it is not in use and after they have completed work for the day.
Educate and prepare workers
Final however actually not least, spend money on a company cybersecurity consciousness coaching program. Maintain usually scheduled trainings to coach workers on safety greatest practices, preserve customers updated with company safety insurance policies, clarify workers’ roles in maintaining the corporate protected and educate customers about safety threats.
E-mail safety is a vital matter in these trainings. Clarify the corporate’s e mail safety coverage, frequent e mail safety threats and advisable e mail safety greatest practices.
Sharon Shea is govt editor of TechTarget Safety.










