On this weblog put up, we offer extra technical particulars associated to our earlier DynoWiper publication.
Key factors of the report:
- ESET researchers recognized new data-wiping malware that now we have named DynoWiper, used towards an vitality firm in Poland.
- The ways, strategies, and procedures (TTPs) noticed throughout the DynoWiper incident intently resemble these seen earlier this yr in an incident involving the ZOV wiper in Ukraine: Z, O, and V are Russian army symbols.
- We attribute DynoWiper to Sandworm with medium confidence, in distinction to the ZOV wiper, which we attribute to Sandworm with excessive confidence.
Sandworm profile
Sandworm is a Russia-aligned menace group that performs damaging assaults. It’s largely recognized for its assaults towards Ukrainian vitality corporations in 2015-12 and 2016-12, which resulted in energy outages. In 2017-06 Sandworm launched the NotPetya data-wiping assault that used a supply-chain vector by compromising the Ukrainian accounting software program M.E.Doc. In 2018-02, Sandworm launched the Olympic Destroyer data-wiping assault towards organizers of the 2018 Winter Olympics in Pyeongchang.
The Sandworm group makes use of such superior malware as Industroyer, which is ready to talk with tools at vitality corporations through industrial management protocols. In 2022-04, CERT-UA thwarted an assault towards an vitality firm in Ukraine the place the Sandworm group tried to deploy a brand new variant of this malware, Industroyer2.
In 2020-10, the US Division of Justice printed an indictment towards six Russian pc hackers that it alleges ready and carried out varied Sandworm assaults. The group is often attributed to Unit 74455 of the Russian Essential Intelligence Directorate (GRU).
Historical past of Sandworm’s damaging operations
Sandworm is a menace actor recognized for conducting damaging cyberattacks, focusing on a variety of entities together with authorities companies, logistics corporations, transportation companies, vitality suppliers, media organizations, grain sector corporations, and telecommunications corporations. These assaults sometimes contain the deployment of wiper malware – malicious software program designed to delete information, erase knowledge, and render programs unbootable.
Its operators have a protracted historical past of conducting such cyberattacks, and now we have documented their exercise extensively. On this blogpost, we concentrate on their latest operations involving data-wiping malware.
To evade detections by safety merchandise, Sandworm usually modifies the damaging malware it deploys – typically by introducing minor adjustments or by producing newly compiled variants from the unique supply code, and different occasions by abandoning a specific wiper altogether and switching to a completely new malware household for its operations. We not often see Sandworm try to deploy a damaging malware pattern that was utilized in an earlier assault (for instance, one with a recognized hash) or one that’s already detected on the time of deployment.
Since February 2022, now we have been totally monitoring incidents involving damaging malware and have publicly documented our findings in stories akin to A yr of wiper assaults in Ukraine. Over time, Sandworm has deployed a variety of damaging malware households, together with, in roughly chronological order, HermeticWiper, HermeticRansom, CaddyWiper, DoubleZero, ARGUEPATCH, ORCSHRED, SOLOSHRED, AWFULSHRED, Status ransomware, RansomBoggs ransomware, SDelete-based wipers, BidSwipe, ROARBAT, SwiftSlicer, NikoWiper, SharpNikoWiper, ZEROLOT, Sting wiper, and ZOV wiper. It ought to be famous that a few of these malware households had been deployed a number of occasions throughout quite a lot of incidents. In 2025, ESET investigated greater than 10 incidents involving damaging malware attributed to Sandworm, virtually all of them occurring in Ukraine.
We repeatedly improve our merchandise to enhance early detection of Sandworm operations – ideally figuring out exercise earlier than damaging wipers are deployed, and at any time when potential stopping harm even when beforehand unknown damaging malware is executed. As a result of nearly all of Sandworm’s cyberattacks at the moment goal Ukraine, we collaborate intently with our Ukrainian companions, together with the Laptop Emergency Response Staff of Ukraine (CERT-UA), to assist each prevention and remediation efforts.
Moreover Ukraine, Sandworm has a decade-long historical past of focusing on corporations in Poland, together with these within the vitality sector. Usually, these operations have been carried out covertly for cyberespionage functions, as seen within the BlackEnergy and GreyEnergy circumstances. Notably, we detected the primary deployment of GreyEnergy malware at a Polish vitality firm again in 2015.
Nevertheless, because the begin of Russia’s full-scale invasion of Ukraine, Sandworm has modified its ways relating to targets in Poland. Particularly, in October 2022, it carried out a damaging assault towards logistics corporations in each Ukraine and Poland, disguising the operation as a Status ransomware incident. Microsoft Menace Intelligence reported on the Status ransomware incidents, which they attributed to Seashell Blizzard (aka Sandworm). At ESET, we detected the Status ransomware household and publicly attributed this exercise to Sandworm.
In December 2025, we detected the deployment of a damaging malware pattern, which we named DynoWiper, at an vitality firm in Poland. The put in EDR/XDR product, ESET PROTECT, blocked execution of the wiper, considerably limiting its influence within the setting. On this blogpost, we reveal further particulars about this exercise and description our attribution course of.
CERT Polska did a wonderful job investigating the incident and printed an in depth evaluation in a report obtainable on its web site.
DynoWiper
On December 29th, 2025, DynoWiper samples had been deployed to the C:inetpubpub listing, which is probably going a shared listing within the sufferer’s area, with the next filenames: schtask.exe, schtask2.exe, and
The attackers initially deployed
DynoWiper’s workflow may be divided into three distinct phases, that are described later within the textual content. The schtask*.exe samples embody solely the primary two phases and introduce a five-second delay between them. In distinction,
The wiper overwrites information utilizing a 16-byte buffer that accommodates random knowledge generated as soon as at the beginning of the wiper’s execution. Recordsdata of measurement 16 bytes or fewer are absolutely overwritten, with smaller information being prolonged to 16 bytes. To hurry up the destruction course of, different information (bigger than 16 bytes) have just some elements of their contents overwritten.
Through the first part, the malware recursively wipes information on all detachable and glued drives, excluding particular directories (utilizing case-insensitive comparability):
- system32
- home windows
- program information
- program information(x86) (an area is lacking earlier than the open bracket)
- temp
- recycle.bin
- $recycle.bin
- boot
- perflogs
- appdata
- paperwork and settings
For
The third part forces the system to reboot, finishing the destruction of the system.
In contrast to Industroyer and Industroyer2, the found DynoWiper samples focus solely on the IT setting, with no noticed performance focusing on OT (operational expertise) industrial parts. Nevertheless, this doesn’t exclude the chance that such capabilities had been current elsewhere within the assault chain.
Different instruments deployed
We recognized further instruments used inside the identical community previous to deployment of the wiper.
In early levels of the assault, attackers tried to obtain the publicly obtainable Rubeus software. The next path was used: c:customers
In early December 2025, attackers tried to dump the LSASS course of utilizing Home windows Activity Supervisor. Moreover, they tried to obtain and launch a publicly obtainable SOCKS5 proxy software known as rsocx. The attackers tried to execute this proxy in reverse-connect mode utilizing the command line C:Customers
ZOV wiper
We recognized a number of similarities to beforehand recognized damaging malware, particularly to the wiper now we have named ZOV, which we attribute to Sandworm with excessive confidence. DynoWiper operates in a broadly related vogue to the ZOV wiper. Notably, the exclusion of sure directories and particularly the clear separate logic current within the code for wiping smaller and bigger information may also be discovered within the ZOV wiper.
ZOV is damaging malware that we detected being deployed towards a monetary establishment in Ukraine in November 2025.
As soon as executed, the ZOV wiper iterates over information on all fastened drives and wipes them by overwriting their contents. It skips information in these directories:
- $Recycle.Bin
- AppData
- Utility Knowledge
- Program Recordsdata
- Program Recordsdata (x86)
- Temp
- Home windows
- Home windows.previous
How a file is wiped relies on its measurement. To destroy knowledge as shortly as potential, information smaller than 4,098 bytes have their complete contents overwritten; bigger information have just some elements of their contents overwritten. The buffer, which is repeatedly written to information, is of measurement 4,098 bytes, and begins with the string ZOV (referring to the Russian army symbols) adopted by null bytes.
After finishing this fast wipe, it prints what number of directories and information had been wiped, and runs the shell command time /t & ver & rmdir C: /s /q && dir && shutdown /r (print present native time and Home windows model, erase the contents of the C: drive, checklist the present working listing, and initiates a system reboot).
Proper earlier than exiting, the wiper drops a picture from its assets to %appdatapercentLocWall.jpg and units it because the desktop background. As proven in Determine 1, the wallpaper additionally has the ZOV image.

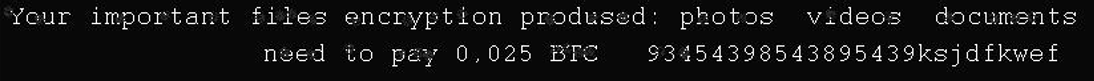
There was one other ZOV wiper case at an vitality firm in Ukraine, the place the attackers deployed the wiper on January 25th, 2024. Within the noticed pattern, the buffer that’s written to information doesn’t include the ZOV image. As an alternative, it accommodates the only character P adopted by null bytes. Additionally, the textual content within the dropped picture (see Determine 2) resembles a ransom observe however refers to a nonexistent Bitcoin deal with.
Harmful malware deployment strategies
Sandworm sometimes abuses Energetic Listing Group Coverage to deploy its data-wiping malware throughout all machines inside a compromised community. Group-wide GPO deployment usually requires Area Admin privileges and is commonly staged from a website controller. This exercise underscores Sandworm’s sophistication and its confirmed means to acquire high-privilege Energetic Listing entry throughout many intrusions.
Through the incident response to the Industroyer2 assault in April 2022, CERT‑UA found a PowerShell script they named POWERGAP. Sandworm had been utilizing this script incessantly to deploy varied data-wiping malware throughout a number of organizations. Later, in November 2022, ESET researchers discovered that the identical script had been used to distribute the RansomBoggs ransomware in Ukraine. Nevertheless, in some unspecified time in the future Sandworm stopped utilizing this deployment script, but continued deploying damaging malware through Energetic Listing Group Coverage.
Curiously, throughout the evaluation of the ZOV wiper incident, we recognized a more recent PowerShell script used to deploy the ZOV wiper. This script accommodates hardcoded variables particular to the sufferer’s setting, together with the area controller identify, area identify, Group Coverage Object (GPO) identify, deployed filename, file path, GPO hyperlink string, and scheduled process identify. As soon as executed, the script performs all crucial actions to distribute the malicious binary to customers and computer systems throughout all the area.
Extra considerably, a deployment script with very related performance, however with out robust code similarity, was found getting used to deploy the DynoWiper malware in a Polish vitality firm. In that case, nonetheless, the malicious binary was not distributed to particular person computer systems however was as an alternative executed immediately from a shared community listing.
As talked about above, operations of this data-wiping nature generally require a menace actor to own Area Admin privileges. As soon as a menace actor reaches this degree of entry, defending the setting turns into extraordinarily troublesome, as they’ll carry out practically any motion inside the area. Some organizations, notably within the vitality sector, additionally deliberately section or isolate elements of their IT/OT environments to fulfill operational and security necessities. Whereas this isolation may be an applicable risk-management selection, it sometimes reduces defender visibility and might sluggish proof assortment and response workflows, which in flip can complicate incident investigation and lead to lower-confidence attribution.
Attribution
We attribute DynoWiper to Sandworm with medium confidence. The next elements assist our evaluation:
- There’s a robust overlap between the TTPs noticed on this exercise and people sometimes related to Sandworm operations. Particularly, using data-wiping malware and its deployment through Energetic Listing Group Coverage are each strategies generally employed by Sandworm. As described above, we recognized similarities in each the wipers used and the Group Coverage deployment script when evaluating this case to earlier Sandworm exercise.
- The focused trade aligns with Sandworm’s typical pursuits. This group incessantly targets vitality corporations and has a confirmed monitor document of attacking OT environments.
- Traditionally, Sandworm has focused Polish vitality corporations for cyberespionage functions, utilizing the BlackEnergy and GreyEnergy malware households.
- We’re not conscious of another not too long ago energetic menace actors which have used data-wiping malware of their operations towards targets in European Union international locations.
The next elements contradict a Sandworm attribution:
Though Sandworm has beforehand focused corporations in Poland, it sometimes did so covertly – both for cyberespionage functions solely or by disguising its data-wiping exercise as a ransomware assault, akin to within the Status ransomware incidents. It’s price noting that we solely attribute the data-wiping element of this exercise to Sandworm with medium confidence. We shouldn’t have visibility into the preliminary entry technique used on this incident and subsequently can’t assess how or by whom the primary steps had been carried out. Particularly, the preparatory levels main as much as the damaging exercise might have been carried out by one other menace actor group collaborating with Sandworm. Notably, in 2025 we noticed and confirmed that the UAC‑0099 group carried out preliminary entry operations towards targets in Ukraine and subsequently handed off validated targets to Sandworm for follow-up exercise.
Conclusion
This incident represents a uncommon and beforehand unseen case during which a Russia-aligned menace actor deployed damaging, data-wiping malware towards an vitality firm in Poland.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis gives personal APT intelligence stories and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
| SHA-1 | Filename | Detection | Description |
| 472CA448F82A7FF6F373 |
TMP_Backup.tmp.exe | Win32/KillFiles.NMJ | ZOV wiper. |
| 4F8E9336A784A1963530 |
TS_5WB.tmp.exe | Win32/KillFiles.NMJ | ZOV wiper. |
| 4EC3C90846AF6B79EE1A |
Win32/KillFiles.NMO | DynoWiper. | |
| 86596A5C5B05A8BFBD14 |
schtask.exe | Win32/KillFiles.NMO | DynoWiper. |
| 69EDE7E341FD26FA0577 |
schtask2.exe | Win32/KillFiles.NMO | DynoWiper. |
| 9EC4C38394EA2048CA81 |
rsocx.exe | Win64/HackTool.Rsocx.A | rsocx SOCKS5 proxy software. |
| 410C8A57FE6E09EDBFEB |
Rubeus.exe | MSIL/Riskware.Rubeus.A | Rubeus toolset for Kerberos assaults. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 31.172.71[.]5 | N/A | Fornex Internet hosting S.L. | 2024-10-27 | SOCKS5 server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 18 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Useful resource Improvement | T1584.004 | Compromise Infrastructure: Server | A probable compromised server was used to host a SOCKS5 server. |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell | Sandworm used PowerShell scripts for deployment within the goal organizations. |
| T1059.003 | Command and Scripting Interpreter: Home windows Command Shell | The ZOV wiper runs a shell command through cmd.exe to assemble info, take away information and directories, and schedule a system reboot. | |
| T1053.005 | Scheduled Activity/Job: Scheduled Activity | The ZOV wiper and DynoWiper are executed utilizing Home windows scheduled duties. | |
| Credential Entry | T1003.001 | OS Credential Dumping: LSASS Reminiscence | The attackers tried to dump LSASS course of reminiscence utilizing Home windows Activity Supervisor. |
| Discovery | T1083 | File and Listing Discovery | The ZOV wiper and DynoWiper seek for information and directories with the intention to wipe them. |
| T1680 | Native Storage Discovery | The ZOV wiper and DynoWiper determine further disks current on the system to subsequently wipe knowledge on them. | |
| T1082 | System Info Discovery | The ZOV wiper prints the Home windows model of the operating system. | |
| T1124 | System Time Discovery | The ZOV wiper prints present native time. | |
| Command and Management | T1105 | Ingress Software Switch | The attackers tried to obtain Rubeus and rsocx within the goal group. |
| T1090.002 | Proxy: Exterior Proxy | The attackers tried to create a reference to an exterior proxy utilizing rsocx. | |
| Impression | T1561.001 | Disk Wipe: Disk Content material Wipe | The ZOV wiper and DynoWiper overwrite contents of information. |
| T1529 | System Shutdown/Reboot | The ZOV wiper and DynoWiper reboot the system after the wiping course of is full. |











