The Iranian menace group Educated Manticore, additionally tracked as APT35, APT42, Charming Kitten, or Mint Sandstorm, has intensified its cyber-espionage operations focusing on Israeli cybersecurity specialists, laptop science professors, and journalists.
Related to the Islamic Revolutionary Guard Corps’ Intelligence Group (IRGC-IO), this superior persistent menace (APT) group has been beneath scrutiny by Test Level Analysis for a number of years.
Spear-Phishing Campaigns
Since mid-June 2025, the group has launched refined spear-phishing campaigns, impersonating fictitious staff of cybersecurity companies to deceive high-profile people from main Israeli universities.
These assaults typically start with polished emails or WhatsApp messages that leverage AI-assisted writing for credibility, although delicate discrepancies, akin to mismatched sender names, have often uncovered their fraudulent nature.

Educated Manticore’s techniques rely closely on customized phishing kits designed to imitate authentic authentication flows for providers like Google, Outlook, and Yahoo.
These kits, constructed as React-based Single Web page Purposes (SPAs), use obfuscated code and dynamic routing to render authentication steps with out web page reloads, enhancing their misleading look.
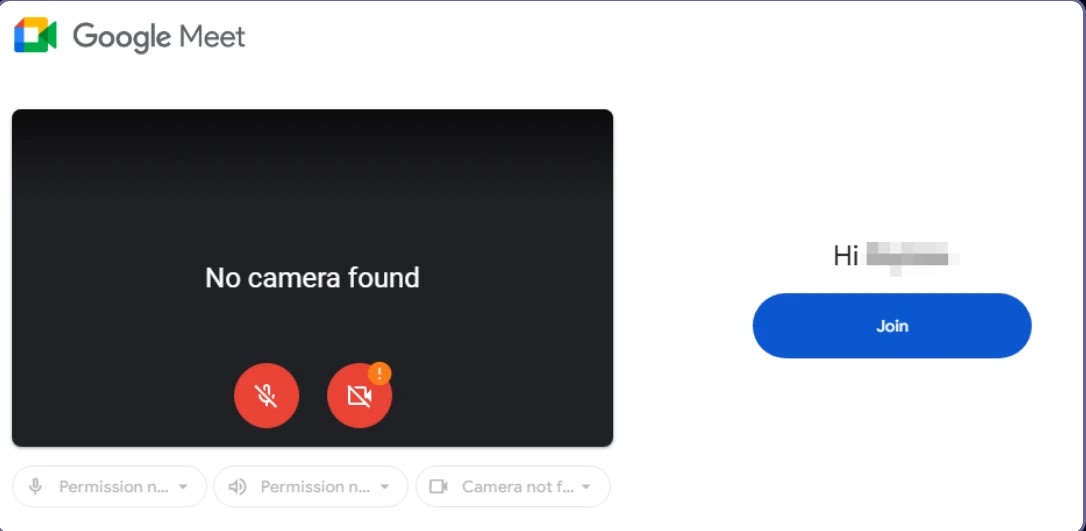
Victims are lured to faux Gmail login pages or Google Meet invites after preliminary contact, the place their electronic mail addresses are pre-filled to spice up belief.
Superior Phishing Kits
The phishing infrastructure helps complicated authentication mechanisms, together with two-factor authentication (2FA) relay assaults, capturing passwords, SMS codes, and even keystrokes by way of a real-time WebSocket keylogger.
Since January 2025, over 130 distinctive domains and quite a few subdomains, principally registered via NameCheap, have been linked to this marketing campaign, resolving to a dozen IP addresses. A few of these align with the GreenCharlie sub-cluster, indicating a broader community of malicious infrastructure.
The group’s use of Google Websites to host multi-stage phishing pages additional provides legitimacy by exploiting the trusted Google area.
In keeping with the Report, As soon as victims work together with faux assembly invites, they’re redirected to attacker-controlled servers internet hosting credential-harvesting pages.
This persistent and agile operation, characterised by fast area setup and takedowns, continues to pose a major menace, particularly in the course of the ongoing Iran-Israel battle.
Educated Manticore’s concentrate on delicate targets in trust-based environments suggests a strategic intent to steal identities and credentials aligned with Iranian regime pursuits, making their campaigns a essential concern for cybersecurity defenders.
Indicators of Compromise (IOC)
| Indicator Kind | Particulars |
|---|---|
| IPs | 185.130.226.71, 45.12.2.158, 45.143.166.230, 91.222.173.141, 194.11.226.9 |
| Domains | conn-ectionor.cfd, optio-nalynk.on-line, ques-tion-ing.xyz, sendly-ink.store, idea-home.on-line |
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, and X to Get On the spot Replace
.png
)