Jérôme Segura, cybercriminals are exploiting search parameter vulnerabilities to inject pretend cellphone numbers into the reliable web sites of main manufacturers like Apple, Financial institution of America, Fb, HP, Microsoft, Netflix, and PayPal.
This refined assault, technically termed a “search parameter injection assault,” manipulates the search performance of those trusted platforms, deceiving customers into contacting scammers underneath the guise of official buyer assist.
Cybercriminals Exploit Search Parameter Vulnerabilities
By leveraging sponsored search adverts on Google, attackers information unsuspecting victims to genuine web sites, the place malicious URL parameters overlay fraudulent contact particulars, making a seamless phantasm of legitimacy.
The mechanics of this rip-off are as insidious as they’re intelligent. Cybercriminals craft URLs that exploit mirrored enter vulnerabilities in an internet site’s search performance, embedding pretend cellphone numbers straight into the displayed search outcomes.
As an illustration, on Netflix’s real assist web page, customers see the reliable URL of their browser’s tackle bar, and the location’s format seems genuine.
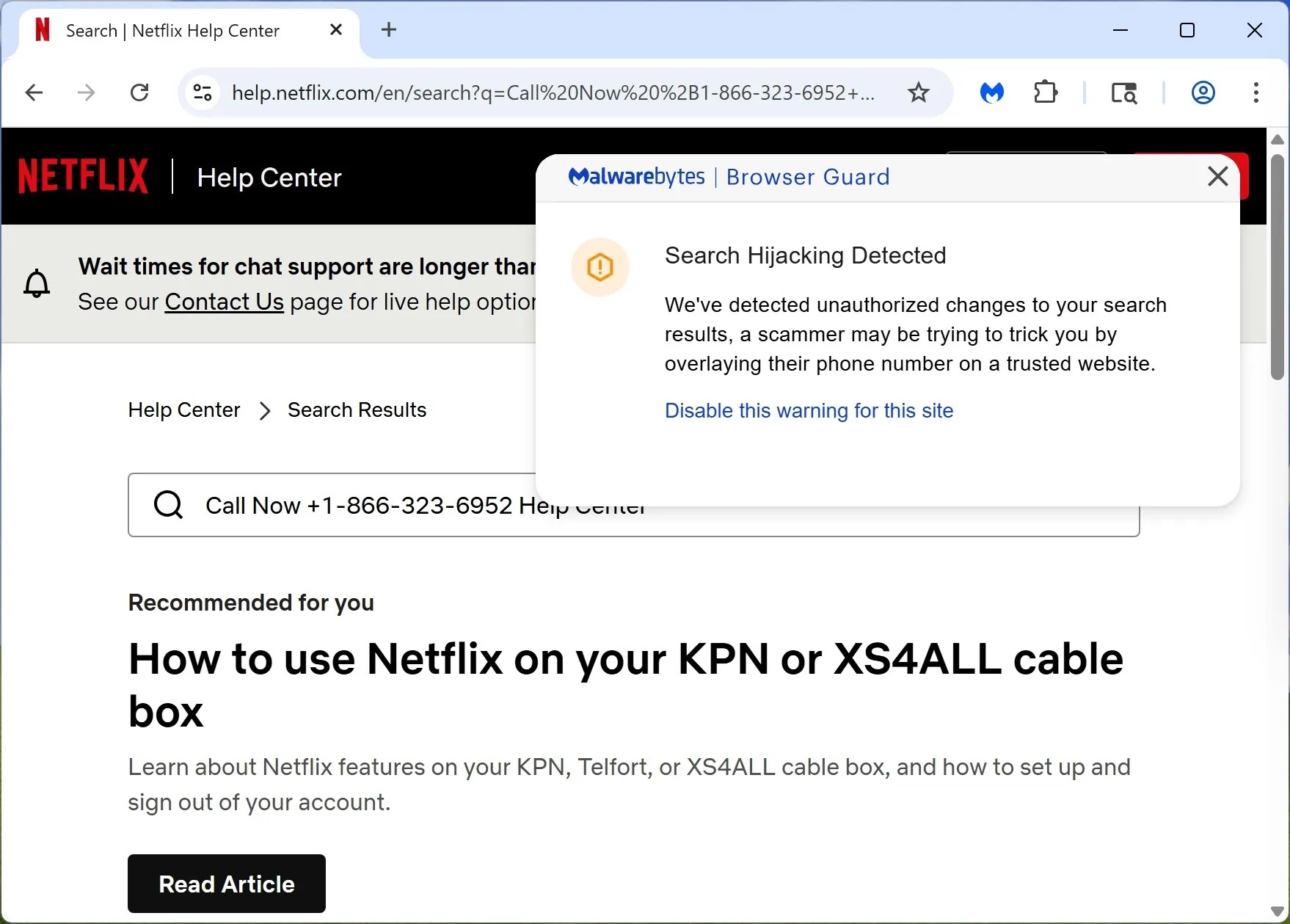
Nonetheless, the search outcome prominently shows a scammer’s cellphone quantity, masquerading as an official contact.
This exploit thrives on the dearth of correct sanitization or validation of person enter within the search question parameter, permitting attackers to poison the data customers depend on.
A Misleading Entice with Actual-World Penalties
As soon as victims dial the quantity, they’re linked to fraudsters impersonating model representatives, who then try and extract delicate private information, monetary particulars, and even distant entry to the sufferer’s machine.
In circumstances involving monetary establishments like Financial institution of America or PayPal, the last word purpose is commonly to empty the sufferer’s accounts.
The affect of those assaults is amplified by their subtlety. On platforms like HP, small discrepancies such because the phrase “4 Outcomes for” previous the scammer’s textual content may trace at foul play, however most customers, trusting the legitimacy of the web site, overlook these clues.
Apple’s case is especially misleading, with the manipulated web page suggesting no search outcomes had been discovered, nudging customers to name the displayed fraudulent quantity for help.
This psychological manipulation, paired with the technical exploitation of trusted domains, makes these scams terribly efficient.
Fortuitously, instruments like Malwarebytes Browser Guard have begun to detect such manipulations, issuing warnings about “Search Hijacking Detected” to alert customers of unauthorized alterations to go looking outcomes.
In line with the Report, This wave of assaults underscores a crucial vulnerability in how main manufacturers deal with search parameters on their web sites, exposing a niche in net safety that cybercriminals are fast to use.
The belief customers place in acquainted URLs and sponsored Google adverts turns into a weapon in opposition to them, as attackers mix authenticity with deception to devastating impact.
As this rip-off continues to focus on high-profile corporations, it serves as a stark reminder for each customers and firms to prioritize sturdy enter validation and heightened vigilance.
With out swift motion to sanitize search functionalities and educate the general public, these search parameter injection assaults threat eroding client confidence in even probably the most respected digital platforms, turning a routine seek for assist right into a gateway for fraud.
Discover this Information Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Immediate Updates
.png
)










