Axis Communications, a number one supplier of community video and surveillance options, has confirmed a crucial vulnerability in its Autodesk® Revit® plugin that uncovered Azure Storage Account credentials inside signed DLLs.
Found in July 2024 by Pattern Micro’s Zero Day Initiative™ (ZDI), the vulnerability allowed attackers to entry and manipulate cloud property belonging to Axis and its clients.
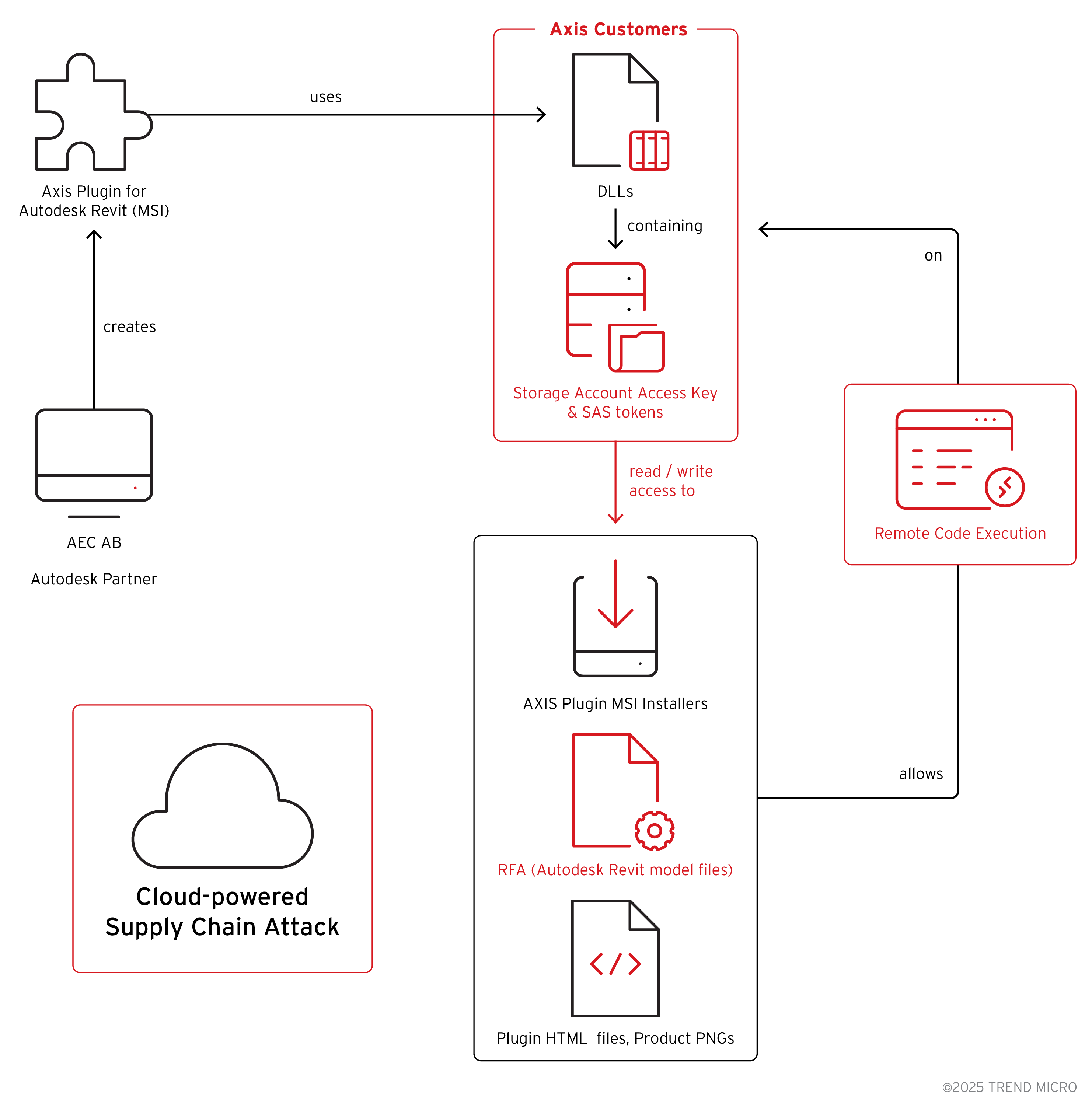
On July 8, 2024, ZDI researchers recognized a digitally signed DLL, AzureBlobRestAPI.dll, bundled throughout the AXIS Plugin for Autodesk Revit.
This DLL, signed by AEC Superior Engineering Computation AB—an Axis accomplice—contained cleartext Azure Shared Entry Signature (SAS) tokens and entry key pairs for 2 storage accounts named “axisfiles” and “axiscontentfiles.”

Embedding legitimate credentials in a non-public technique of the DLL’s code allowed any consumer with the plugin put in to manage these accounts, together with studying, writing, and modifying saved sources.
Investigation revealed that each storage accounts hosted MSI installers for the Revit plugin and proprietary RFA mannequin recordsdata for Axis merchandise comparable to IP cameras and radars.

As a result of these installers and RFA recordsdata have been distributed by way of the uncovered storage accounts, any attacker might obtain the installers or tamper with mannequin recordsdata utilized by architects and engineers in constructing data modelling workflows.
Vendor Response and Patch Evolution
Following disclosure below advisory ZDI-24-1181, Axis launched model 25.3.710 of the plugin, which obscured credentials by way of .NET obfuscation.
Nevertheless, instruments like de4dot simply recovered the SAS tokens and entry keys, resulting in extra advisories ZDI-24-1328 and ZDI-24-1329.
In response, Axis issued model 25.3.711, eradicating storage account entry keys totally and embedding a read-only SAS token for a brand new account.
Whereas this decreased privileges, the brand new token nonetheless permitted attackers to listing and retrieve earlier MSI installers—a few of which contained the unique, extra permissive credentials.
The ultimate advisory, ZDI-25-858, prompted Axis to revoke the unique storage account keys and publish model 25.3.718 in March 2025.
This replace eradicated embedded credentials and enforced least-privilege entry, guaranteeing that solely approved clients might obtain plugin property and mannequin recordsdata.
Axis additionally eliminated all weak plugin variations from its storage infrastructure and notified affected companions to improve instantly.
Provide Chain and RCE Dangers
Past credential leaks, ZDI researchers examined potential repercussions of compromised RFA recordsdata. Revit household recordsdata function enter for 3D modelling and have traditionally been susceptible to parser vulnerabilities.

Pattern ZDI uncovered a number of vulnerabilities in Revit’s RFA dealing with that might allow distant code execution if an attacker changed legit mannequin recordsdata with malicious variants hosted on Axis’s storage accounts.
A profitable exploitation chain might end in provide chain compromise, as malicious installers or altered RFA recordsdata distribute throughout engineering corporations worldwide.

This incident echoes a 2023 case involving Microsoft’s PC Supervisor software, the place uncovered SAS tokens allowed full management over WinGet packages, subdomains, and URL-shortening providers.
Each examples underscore that signed binaries don’t assure safety and that credential publicity in customer-facing infrastructure can function a springboard for multi-stage assaults.
Axis Communications has absolutely patched the vulnerability with model 25.3.718. Nonetheless, the case highlights the necessity for steady safety evaluate of third-party plugins, strict adherence to the precept of least privilege for cloud credentials, and rigorous file-format parsing safeguards.
Organizations leveraging cloud distribution mechanisms and third-party extensions should proactively validate belief, implement sturdy secret administration, and monitor for anomalies to forestall provide chain exploits.
Observe us on Google Information, LinkedIn, and X to Get Prompt Updates and Set GBH as a Most popular Supply in Google.










