A brand new wave of cyber espionage assaults has introduced BPFDoor malware into the highlight as a stealthy and harmful device for compromising networks.
In accordance with safety specialists at Development Micro, BPFDoor is a state-sponsored backdoor attributed to the superior persistent menace (APT) group often called Earth Bluecrow (additionally known as Pink Menshen).
This malware exploits reverse shells and complex Berkeley Packet Filtering (BPF) strategies to infiltrate and management methods throughout telecommunications, finance, and retail sectors in areas similar to South Korea, Hong Kong, Myanmar, Malaysia, and Egypt.
Understanding BPFDoor Malware
BPFDoor, a backdoor detected as Backdoor.Linux.BPFDOOR, is uniquely highly effective as a result of its reliance on BPF, a kernel-level packet filtering know-how.

Whereas its core functionalities resemble rootkits, BPFDoor distinguishes itself by means of its capability to stay undetected by firewalls and evade standard community scans.
The malware prompts upon receipt of “magic sequences” — particular byte strings embedded in community packets — that set off predefined actions on the goal machine.
The first stealth capabilities of BPFDoor embrace altering course of names, avoiding port listening, and bypassing safety logs.
This makes it extremely appropriate for long-term espionage, permitting attackers to embed themselves deeply inside a community with out elevating suspicion.
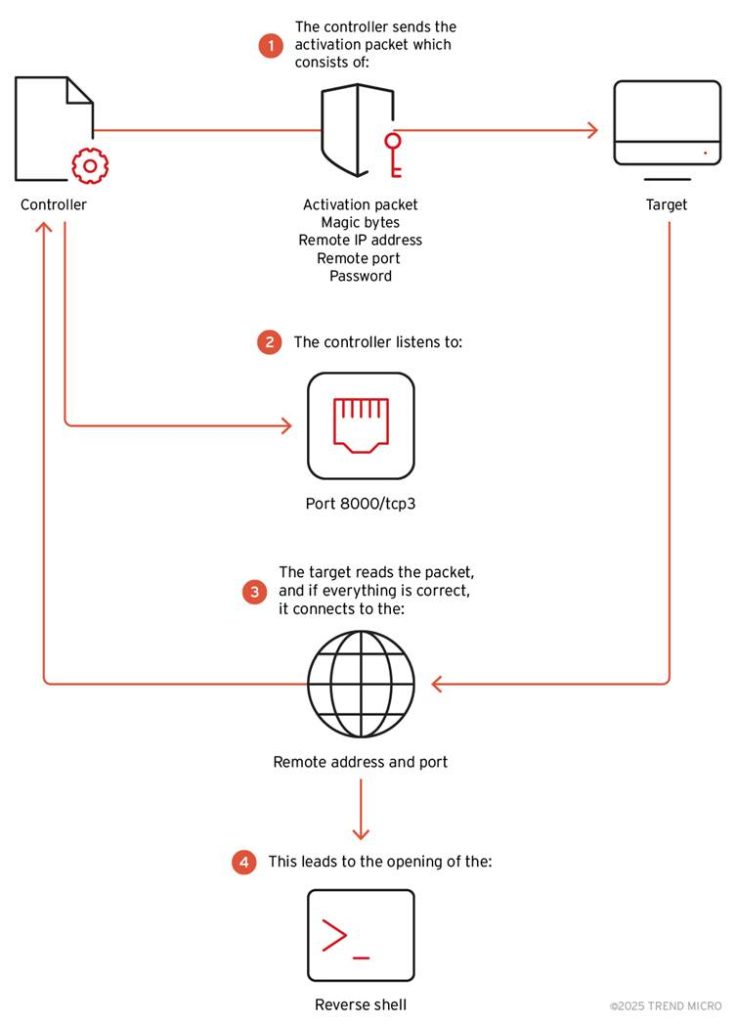

Reverse Shell Method and Lateral Motion
One in all BPFDoor’s alarming capabilities is its use of reverse shells to increase management over contaminated methods.
A reverse shell permits attackers to run instructions remotely on compromised servers by reversing the standard client-server communication mannequin. By way of this mode, attackers can transfer laterally throughout networks to entry delicate information or management further methods.
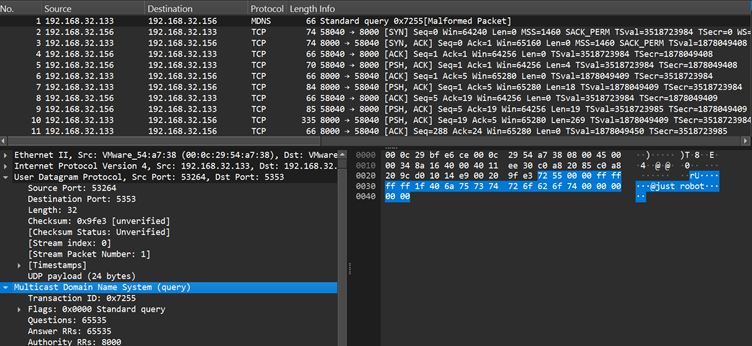
Utilizing a customized controller, menace actors deploy reverse shells by way of three protocols: TCP, UDP, and ICMP. As soon as activated, the malware communicates with the attacker’s system by bypassing normal safety defenses.
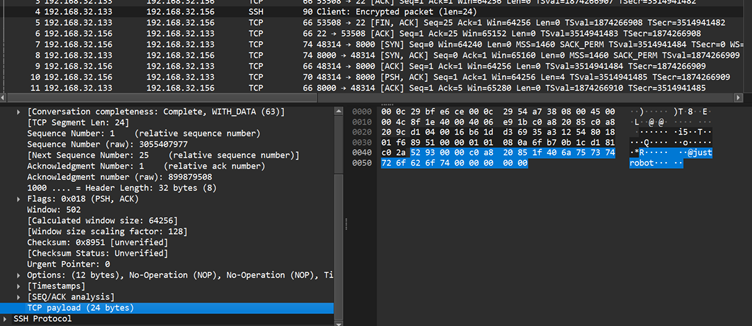

For instance, a controller command can ask BPFDoor to open an encrypted reverse shell session between an contaminated host and an attacker’s machine, enabling seamless distant entry.
The controller additionally permits attackers to change parameters like passwords, magic sequences, and vacation spot ports, enhancing customization for various targets.
Such versatility permits Earth Bluecrow to adapt its assaults for various industries and geographies.
Targets and Protection Mechanisms
Development Micro’s investigation revealed BPFDoor primarily targets Linux-based servers in sectors vital to nationwide and company safety.
Latest assaults have been noticed on telecommunications suppliers in South Korea and Myanmar, monetary establishments in Egypt, and retail companies in Malaysia.
Defenders are urged to watch community exercise for uncommon TCP, UDP, or ICMP packets containing suspicious magic sequences or patterns indicative of BPFDoor exercise.

BPFDoor’s capability to make use of reverse shells, mixed with its stealthy nature, poses vital dangers to organizations worldwide.
As Earth Bluecrow continues to refine its strategies, firms should bolster their defenses to guard in opposition to this superior cyber espionage device.
Detection, response, and proactive safety measures are vital to countering BPFDoor and safeguarding delicate networks.
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, & X to Get Instantaneous Updates!
.png
)









