ESET Analysis has uncovered a major surge in CloudEye malware detections, with a 30-fold enhance within the second half of 2025.
The safety agency detected greater than 100,000 an infection makes an attempt over the six months, signaling a widespread menace affecting organizations globally.
CloudEyE operates as a Malware-as-a-Service (MaaS) downloader and cryptor designed to hide and deploy secondary payloads together with Rescoms, Formbook, and Agent Tesla identified data stealers and distant entry trojans.
The proliferation of CloudEyE represents a notable shift in malware distribution ways, leveraging the rising ecosystem of ransomware-as-a-service and malware-as-a-service platforms.
By functioning as a stealthy supply mechanism, CloudEyE allows menace actors to distribute numerous malware households whereas sustaining operational flexibility and anonymity.
This modular strategy permits attackers to customise payloads primarily based on course atmosphere, rising the effectiveness of their campaigns.
Multi-Stage An infection Chain
CloudEyE’s an infection methodology notes a complicated multi-stage structure that maximizes evasion capabilities.

The preliminary downloader stage spreads by means of PowerShell scripts, JavaScript information, and NSIS (Nullsoft Scriptable Set up System) executables.
These entry factors are generally delivered through spearphishing emails, drive-by downloads, and compromised web sites. As soon as execution is achieved, the downloader retrieves the cryptor element the second stage which comprises the ultimate payload.
A important attribute distinguishing CloudEyE is its heavy obfuscation throughout all an infection phases. This encryption and code obfuscation approach protects in opposition to endpoint detection and response (EDR) options, static evaluation, and menace intelligence databases.
The layered obfuscation strategy makes forensic evaluation considerably tougher for safety researchers and incident responders, permitting the malware to persist longer inside goal environments.
Geographic evaluation of CloudEyE’s assault distribution reveals concentrated focusing on in Central and Japanese Europe, accounting for 32 p.c of registered an infection makes an attempt throughout H2 2025.
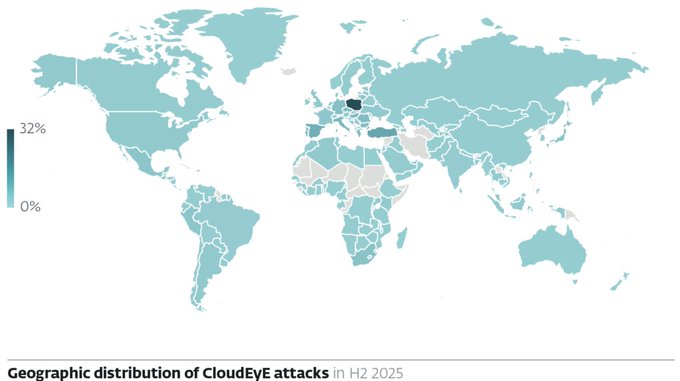
ESET noticed coordinated e mail marketing campaign waves all through September and October 2025, suggesting organized distribution efforts by subtle menace actors.
The geographic focus signifies focused operations somewhat than indiscriminate distribution, pointing to particular trade sectors or organizational vulnerabilities inside these areas.
Implications for Enterprise Safety
The CloudEyE surge underscores the evolving menace panorama the place modular malware architectures and MaaS platforms democratize malware distribution.
Organizations should acknowledge that conventional signature-based detection mechanisms show inadequate in opposition to closely obfuscated payloads.
The an infection chain’s reliance on PowerShell and JavaScript authentic system instruments highlights the problem of distinguishing malicious exercise from regular administrative operations.
Organizations ought to implement behavioral-based detection programs able to figuring out suspicious PowerShell and JavaScript execution patterns.
E-mail safety filtering ought to prioritize blocking NSIS executables and suspicious script attachments.
Moreover, endpoint detection and response options with superior heuristics and machine studying capabilities present superior visibility into obfuscated menace exercise.
Person safety consciousness coaching stays important, as spearphishing stays the first an infection vector for CloudEyE distribution.
The 100,000+ an infection milestone represents a watershed second in malware prevalence, demonstrating the operational maturity and attain of CloudEyE’s infrastructure.
Continued monitoring of this menace stays important as its modular design allows speedy evolution and adaptation.
Observe us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most popular Supply in Google.










