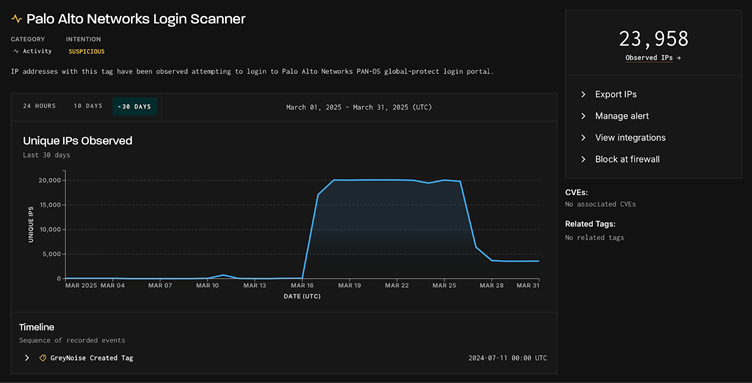
A wave of malicious exercise concentrating on Palo Alto Networks PAN-OS GlobalProtect portals has been noticed, with practically 24,000 distinctive IPs making an attempt unauthorized entry over the previous 30 days.
This coordinated effort, flagged by cybersecurity agency GreyNoise, highlights the rising sophistication of attackers probing community defenses as a precursor to potential exploitation.
GreyNoise detected the surge beginning on March 17, 2025, peaking at practically 20,000 distinctive IP addresses per day.
Whereas the exercise tapered off by March 26, it revealed constant patterns, with nearly all of IP addresses categorized as suspicious (23,800) and a smaller subset deemed outright malicious (154).

Bob Rudis, VP of Knowledge Science at GreyNoise, famous this pattern aligns with historic patterns linked to the emergence of recent vulnerabilities:
“Over the previous 18 to 24 months, we’ve noticed deliberate concentrating on of older vulnerabilities, typically adopted by the invention of recent exploits inside weeks.”
Organizations counting on Palo Alto Networks merchandise are urged to safe their login portals instantly, as attackers could also be getting ready for exploitation.
Key Observations
GreyNoise recognized a number of important parts within the breach try:
Supply and Vacation spot Evaluation
- Supply International locations: Nearly all of site visitors originated from the United States (16,249) and Canada (5,823), with further exercise from Finland, the Netherlands, and Russia.
- Vacation spot International locations: Overwhelmingly focused programs within the United States (23,768), adopted by smaller volumes aimed on the UK, Eire, Russia, and Singapore.
This international exercise underscores a coordinated operation spanning a number of areas.
High Contributors & Toolkit Indicators
A notable portion of site visitors was traced again to 3xK Tech GmbH, answerable for 20,010 IPs below ASN200373.
Different contributors included PureVoltage Internet hosting Inc., Quick Servers Pty Ltd., and Oy Crea Nova Internet hosting Resolution Ltd.
Three JA4h hashes related to the login scanner device have been recognized:
- po11nn11enus_967778c7bec7_000000000000
- po11nn09enus_fb8b2e7e6287_000000000000
- po11nn060000_c4f66731b00d_000000000000
These hashes point out a deliberate and systematic strategy to breaching the portals utilizing specialised connection instruments.
The incident attracts parallels to the 2024 espionage marketing campaign concentrating on perimeter units, as reported by Cisco Talos.
Though the strategies differ, each occasions emphasize the vital want for organizations to observe and defend edge units.
Suggestions for Organizations
Specialists have urged companies to behave swiftly:
- Audit March Logs: Evaluate exercise for uncommon entry makes an attempt.
- Carry out Risk Hunts: Analyze programs for potential compromises or suspicious processes.
- Block Malicious IPs: Use actionable intelligence to attenuate publicity.
In gentle of the probing conduct, guaranteeing sturdy defenses round uncovered Palo Alto Networks portals is important to thwart future exploitation makes an attempt.
The rise in coordinated assaults in opposition to vital community programs serves as a stark reminder of the significance of proactive cybersecurity measures in a always evolving menace panorama.
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, and X to Get Instantaneous Updates!










