The flexibility to make use of a revoked password to log in via RDP happens when a Home windows machine that’s signed in with a Microsoft or Azure account is configured to allow distant desktop entry. In that case, customers can log in over RDP with a devoted password that’s validated in opposition to a regionally saved credential. Alternatively, customers can log in utilizing the credentials for the web account that was used to register to the machine.
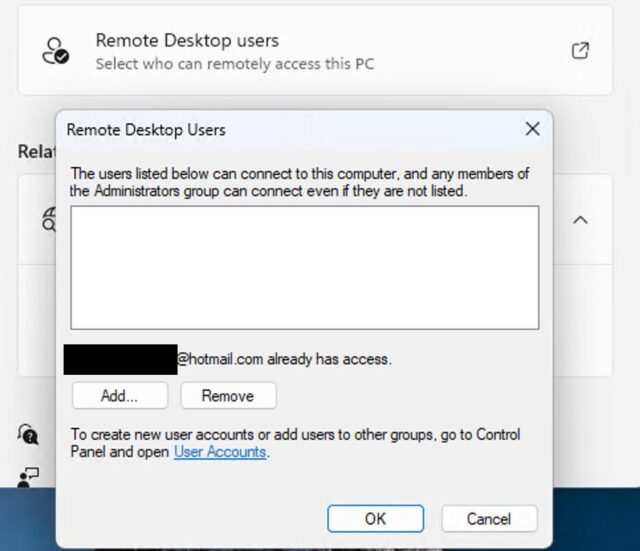
A screenshot of an RDP configuration window exhibiting a Microsoft account (for Hotmail) has distant entry.
Even after customers change their account password, nevertheless, it stays legitimate for RDP logins indefinitely. In some circumstances, Wade reported, a number of older passwords will work whereas newer ones gained’t. The outcome: persistent RDP entry that bypasses cloud verification, multifactor authentication, and Conditional Entry insurance policies.
Wade and one other knowledgeable in Home windows safety mentioned that the little-known habits may show pricey in situations the place a Microsoft or Azure account has been compromised, as an example when the passwords for them have been publicly leaked. In such an occasion, the primary plan of action is to alter the password to stop an adversary from utilizing it to entry delicate assets. Whereas the password change prevents the adversary from logging in to the Microsoft or Azure account, the previous password will give an adversary entry to the consumer’s machine via RDP indefinitely.
“This creates a silent, distant backdoor into any system the place the password was ever cached,” Wade wrote in his report. “Even when the attacker by no means had entry to that system, Home windows will nonetheless belief the password.”
Will Dormann, a senior vulnerability analyst at safety agency Analygence, agreed.
“It would not make sense from a safety perspective,” he wrote in an internet interview. “If I am a sysadmin, I might anticipate that the second I alter the password of an account, then that account’s previous credentials can’t be used wherever. However this isn’t the case.”
Credential caching is an issue
The mechanism that makes all of this doable is credential caching on the arduous drive of the native machine. The primary time a consumer logs in utilizing Microsoft or Azure account credentials, RDP will affirm the password’s validity on-line. Home windows then shops the credential in a cryptographically secured format on the native machine. From then on, Home windows will validate any password entered throughout an RDP login by evaluating it in opposition to the regionally saved credential, with no on-line lookup. With that, the revoked password will nonetheless give distant entry via RDP.










