Figuring out the gadgets in your community is a vital safety activity. In any case, you may’t safe what you do not know. Whereas loads of fancy configuration administration instruments checklist the nodes on a community, generally the straightforward and easy utilities are finest.
Arp-scan is a device that discovers and identifies IPv4 community nodes by utilizing Handle Decision Protocol (ARP) queries to generate a complete checklist of gadgets. Its use of ARP units arp-scan properly aside from scanners that depend on ping (ICMP), TCP or Person Datagram Protocol (UDP) scans. Many instruments function at OSI Layer 3, comparable to Nmap. Not all community gadgets reply to such higher-level scans. As a result of ARP is a elementary part of networking, an arp-scan question at OSI Layer 2 will nearly definitely succeed.
Arp-scan has a particular limitation. As a result of ARP isn’t routable, an arp-scan is proscribed to the native subnet. That is usually precisely what you need: a targeted, direct and simply managed scan. For a broader community scan, take into account Nmap, Offended IP Scanner or an analogous device.
Let us take a look at tips on how to set up arp-scan, fundamental scan choices after which consider use instances.
Learn how to set up arp-scan
Putting in arp-scan in your Linux penetration testing field is so simple as calling up your distribution’s most well-liked package deal supervisor.
For Ubuntu, Debian and related distributions, kind:
apt set up arp-scan
On Fedora, Alpine Linux, Rocky or Crimson Hat Enterprise Linux distros, kind:
dnf set up arp-scan
On openSUSE, kind:
zypper set up arp-scan
On Arch Linux, kind :
pacman -S arp-scan
Many security-oriented distributions, comparable to Kali Linux, embrace arp-scan by default.
Mac customers ought to set up the Homebrew Mac package deal supervisor after which kind the next command to put in arp-scan:
brew set up arp-scan
The set up is more difficult for Home windows customers. You will want an arp-scan port (examine GitHub), the Cygwin Unix-like setting or Home windows Subsystem for Linux. After putting in arp-scan, run it from the Terminal. It is a command-line utility.

Learn how to run an preliminary scan
Arp-scan works by sending ARP requests to all IP addresses in a specified vary. These requests ask the receiving computer systems to answer the supply system with their IP deal with. That is an integral a part of fundamental IP networking, so all programs ought to reply. Arp-scan information every response and shows the outcomes.
The essential arp-scan syntax depends on a consumer to establish a community interface and the subnet you wish to scan.
arp-scan -I
For instance, to scan subnet 192.168.2.0/24 on interface eth1, kind:
arp-scan -I eth1 192.168.2.0/24
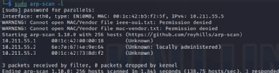
The outcomes embrace all gadgets that reply to the ARP question. Arp-scan identifies them by media entry management (MAC) and IP deal with, together with the community interface card producer. The scan ought to end rapidly, since there’s not a lot to the protocol.
Wi-fi networks additionally depend on MAC addresses, so you may specify your system’s wi-fi interface because the supply. This can be a helpful choice for locating rogue wi-fi gadgets in your community.
Further arp-scan choices
Numerous arp-scan choices can modify the device’s conduct. Mix the next with the usual scan choices for better flexibility:
- -q (quiet mode). Shows solely MAC and IP addresses with out exhibiting interface producer data.
- -x (plain mode). Hides the default header and footer data, making it simpler to import the scan’s outcomes into different codecs, comparable to CSV.
- -g. Ignores any duplicate responses.
- -r 3. Specifies the variety of retries (three, on this instance).
- -R. Randomizes the scan order of specified hosts.
Overview the arp-scan man web page for extra choices. Mix the assorted choices to assemble and format the knowledge wanted.
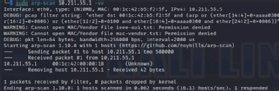
The arp-fingerprint command is a part of the arp-scan package deal. Use it to focus on a single host.
Improve the arp-scan output verbosity by utilizing the -v choice. The outcomes show scan passes in progress, packet size particulars, debug data and extra. Use a number of v choices for better element (comparable to -vvv).
Arp-scan use instances
Remember that arp-scan doesn’t try to cover from intrusion detection programs or different scan prevention instruments. Its queries are apparent and noisy. If you happen to choose a stealthy scan, take into account different instruments. Netdiscover, for instance, could be a very good different. ARP visitors, nevertheless, is a standard a part of networking, so different communications may camouflage your scan.
Use arp-scan in any situation the place detecting community nodes is essential however hiding your actions isn’t. Take into account the next examples:
- Community mapping and reconnaissance. Map networks for safety audits or scan for surprising and unknown gadgets.
- Moral hacking. Map networks and establish gadgets throughout pen testing or different respectable safety actions.
- Troubleshooting. Establish lively community nodes as half of a bigger troubleshooting course of.
Different community scanners, comparable to Nmap, work one layer larger within the OSI mannequin than arp-scan. This gives better performance, nevertheless it additionally limits a few of their usefulness. Since arp-scan operates at OSI Layer 2, it scans solely the native phase. It’ll, nevertheless, discover nodes different scanners may miss. Mix arp-scan and Nmap scans for finest outcomes. An arp-scan’s simplicity is its biggest asset.
Damon Garn owns Cogspinner Coaction and gives freelance IT writing and enhancing companies. He has written a number of CompTIA research guides, together with the Linux+, Cloud Necessities+ and Server+ guides, and contributes extensively to Informa TechTarget, The New Stack and CompTIA blogs.










