A lone hacker has managed to interrupt into the non-public recordsdata of about 50 main firms around the globe, together with Pickett, Sekisui Home, IFLUSAC, Iberia Airways, K3G Options, CRRC MA, GreenBills, and CiberC, reveals the newest analysis by the Israeli cybersecurity agency Hudson Rock performed for its sister web site Infostealers.com.
Researchers recognized the attacker who’s believed to be an Iranian nationwide working beneath the net names Zestix and Sentap. This particular person is presently auctioning off large quantities of stolen company information on darkish internet boards to the very best bidder.
Whereas we’d count on these massive organisations to be onerous to get into, this wasn’t a really tough job for the hacker. Nonetheless, researchers famous that the hacker merely used stolen passwords to log into accounts that didn’t have primary safety authentication in place.
How “Infostealers” Opened the Door
The hacker didn’t hack the businesses straight. As a substitute, they used Infostealers, particularly RedLine, Lumma, and Vidar. These viruses sneak onto an individual’s laptop often after the sufferer downloads a faux file or a cracked recreation, and quietly steal each password saved of their internet browser.
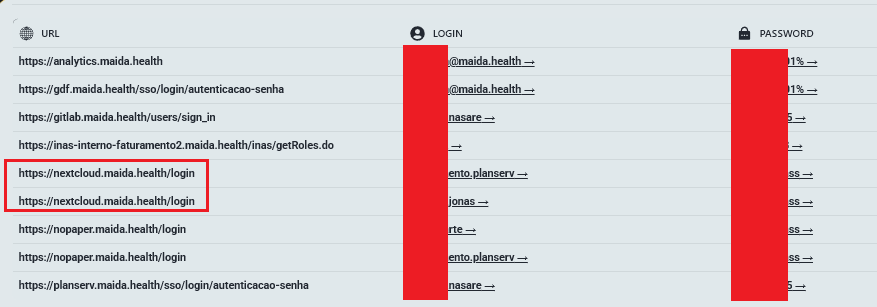
As soon as Zestix had these passwords, they simply used them to log into firm file-sharing websites like ShareFile, Nextcloud, and OwnCloud. The one purpose this labored is that these 50 firms did not activate Multi-Issue Authentication (MFA).
MFA, as we all know it, is that additional step the place a web site asks for a code out of your telephone after you sort your password. Since that second step wasn’t required, the stolen password was all of the hacker wanted to stroll proper in.
Who Was Affected?
The stolen information contains every part from non-public medical recordsdata to army blueprints. For instance, Iberia Airways had 77 GB of knowledge taken, together with security manuals for his or her planes. A U.S. agency known as Pickett & Associates misplaced 139 GB of knowledge, which included detailed maps of energy traces and utility stations.
It’s vital to say that in November 2025, Iberia Airways was additionally concerned in one other information breach through which Everest ransomware stole and later leaked 596GB of the airline’s inner and buyer information.
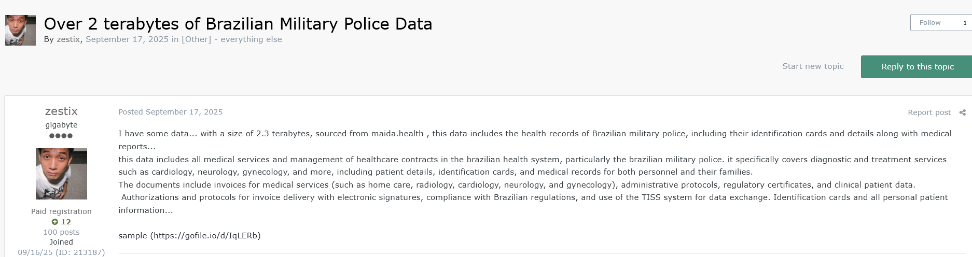
The attain of the assault, as per the corporate’s report, was really world. In Turkey, Intecro Robotics noticed its designs for army drones and fighter jets put up on the market. In Brazil, Maida Well being misplaced 2.3 terabytes of medical information belonging to the army police. Even public transit was hit, with inner plans for practice brakes and signalling utilized by the LA Metro being uncovered via an organization known as CRRC MA.
A Lesson in Fundamental Safety
A number of the stolen passwords utilized in these assaults had been years outdated. If these firms had compelled a password change or just required a telephone code to log in, this whole catastrophe might have been prevented.
Hudson Rock warns that credentials for workers at different giants like Samsung, Walmart, and Deloitte are additionally floating round in these hacker logs, which means they could possibly be in danger too. It is a reminder for all of us: a password alone is not sufficient to maintain your info secure.