DocuSign has emerged as a cornerstone for over 1.6 million clients worldwide, together with 95% of Fortune 500 corporations, and boasts a consumer base exceeding one billion.
Nevertheless, this widespread adoption has made DocuSign a primary goal for cybercriminals.
Leveraging the platform’s trusted popularity, risk actors are more and more deploying subtle phishing campaigns to reap company credentials, infiltrate networks, and execute monetary fraud.
Rising Cyber Threats Concentrating on a Trusted Platform
As phishing accounts for 19% of information breaches and 60% contain a human factor, per Verizon’s findings, understanding these threats is important for organizations aiming to safeguard delicate information.
DocuSign-themed phishing campaigns make use of social engineering ways to deceive customers into compromising their safety.
Victims typically obtain emails mimicking legit DocuSign “envelopes,” full with pressing prompts to “assessment paperwork” by way of clickable yellow buttons or QR code attachments.
These result in malicious websites, corresponding to counterfeit Microsoft login pages, the place customers are tricked into coming into credentials or monetary particulars.
QR codes pose a novel threat, as cell gadgets used to scan them typically lack strong safety software program, making it simpler for attackers to bypass defenses.
Past information theft, these assaults can function entry factors for privilege escalation, lateral motion inside company networks, and even ransomware deployment or information exfiltration.
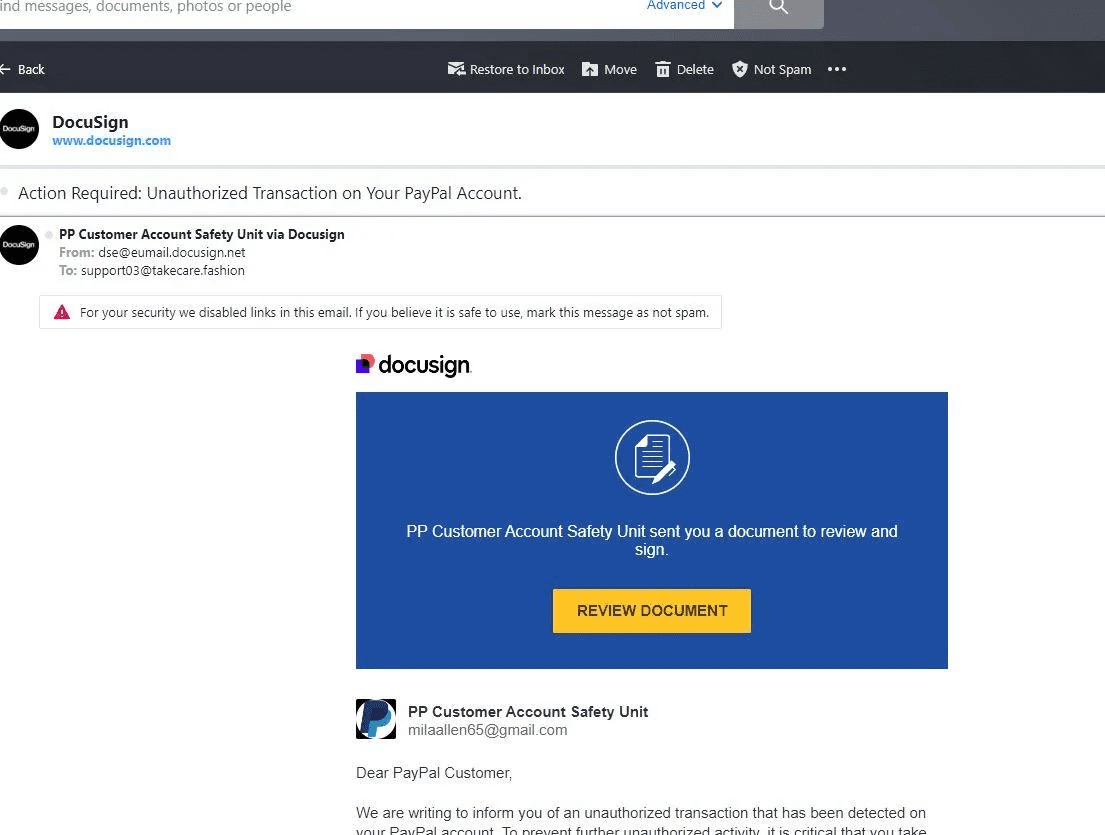
Instance of a rip-off abusing folks’s belief in Docusign for information theft
Mechanisms of DocuSign-Themed Phishing Assaults
Latest incidents spotlight the range of those scams, with cybercriminals registering actual DocuSign accounts to ship authentic-looking envelopes spoofing trusted entities like suppliers or municipal companies.
Others orchestrate pretend bill scams to trick corporations into transferring funds or make use of refund frauds that coax victims into divulging private data over the telephone.
Moreover, some attackers exploit DocuSign’s APIs to craft seemingly legit notifications, mixing authenticity with deception.
These emails might impersonate HR or payroll departments, creating a way of urgency that prompts customers to behave with out scrutiny.
The result’s typically unauthorized entry to company methods, monetary losses, or stolen private information surfacing on the darkish net.
For companies, the stakes are excessive, as a single compromised account can cascade right into a full-scale breach.
In accordance with ESET Report, defending towards DocuSign phishing requires a multi-layered strategy.
Organizations should prioritize worker schooling by means of up to date phishing consciousness packages, educating workers to scrutinize emails for suspicious sender addresses, mismatched signatures, or grammatical errors, and to confirm vacation spot URLs earlier than clicking hyperlinks.
Reliable DocuSign emails embody safety codes for direct doc entry on their platform, by no means by means of e mail hyperlinks or preliminary attachments.
Implementing multi-factor authentication (MFA) throughout company accounts, implementing sturdy password hygiene by way of managers, and deploying superior safety options like ESET for malicious hyperlink and attachment detection are important technical safeguards.
Insurance policies ought to discourage interplay with unsolicited emails, encouraging customers to report suspicious messages to IT groups and DocuSign’s spam reporting tackle.
If a breach happens, swift motion corresponding to password resets, malware scans, gadget isolation, and darkish net monitoring is essential to comprise harm and inform future prevention methods.
Whether or not used for enterprise or private functions, DocuSign’s comfort have to be balanced with vigilance to outmaneuver cybercriminals exploiting belief in digital instruments.
Discover this Information Attention-grabbing! Observe us on Google Information, LinkedIn, & X to Get On the spot Updates!
.png
)


![AI Content material Is 4.7x Cheaper Than Human Content material [+ New Research Report]](https://blog.aimactgrow.com/wp-content/uploads/2025/06/ai-content-is-4.7x-cheaper-than-by-ryan-law-data-studies-120x86.jpg)







