Community admins, safety admins and help technicians want instruments that shortly map the community infrastructure to show nodes, community gadgets and phase boundaries. Delivering repeatedly up to date outcomes, Netdiscover is a wonderful and versatile choice to uncover reside hosts on a community phase.
Let’s look at the significance of community mapping and how one can use Netdiscover within the course of. We’ll illustrate how one can set up Netdiscover and methods to run primary reconnaissance scans on wired and wi-fi networks.
Why community mapping is essential
Community mapping is a important element of cybersecurity and common operations. It helps admins detect unauthorized gadgets and establish gadgets that may not obtain updates, be misconfigured or unnecessarily expose vulnerabilities.
Visualizing a community provides admins a strategy to perceive how gadgets relate to one another and the way community visitors flows by means of them. The objective is to realize higher optimization and extra environment friendly troubleshooting.
Community mapping additionally underpins efficient incident response and catastrophe restoration. The maps show the paths between elements, enabling admins to construct in redundancy or create new connections if the originals fail.
Admins typically use Netdiscover along side different utilities, corresponding to Nmap, Wireshark and NetHogs, to offer an entire image of the community infrastructure and the information circulation inside it.
What’s Netdiscover?
Netdiscover depends on the Deal with Decision Protocol (ARP) and works at Layer 2 of the OSI mannequin to detect reside community nodes. It identifies MAC and IP addresses by both actively scanning a phase or passively sniffing packet headers for host info.
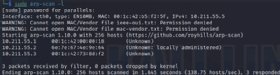
Some directors use arp-scan for related functions. Netdiscover is extra versatile, nonetheless, providing lively and passive modes. Think about using each instruments to make sure full scans.
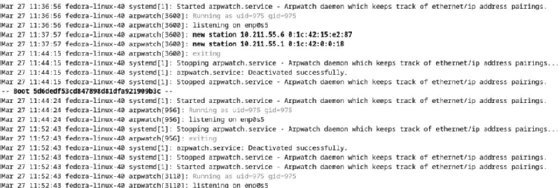
Netdiscover differs considerably from arpwatch, one other Layer 2 community reconnaissance utility. Arpwatch data and tracks MAC and IP tackle relationships, expecting modifications. It’s a monitoring utility fairly than a discovery instrument.
Methods to set up Netdiscover
Kali Linux, BlackArch Linux and Parrot Linux embody Netdiscover of their normal installations. In the event you’re utilizing a special distribution, set up it utilizing a bundle supervisor. You may also obtain Netdiscover from its GitHub website.
On an Ubuntu-like system, sort:
apt set up netdiscover
On a Pink Hat-like distro, sort:
dnf set up netdiscover
MacOS customers can compile Netdiscover for his or her platform. Home windows customers can attempt operating it utilizing the Home windows Subsystem for Linux.
Notice that you just may want so as to add repositories to put in Netdiscover on some distributions.
Methods to use Netdiscover
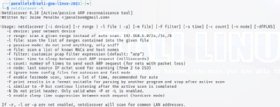
Like different highly effective Linux utilities, Netdiscover has many command choices. Discuss with the built-in assist documentation for all the alternatives.
To get details about Netdiscover, sort:
netdiscover -h
One in all Netdiscover’s distinctive options is its potential to run in lively or passive mode. Passive mode makes Netdiscover harder for intrusion detection techniques (IDSes) to note.
- Lively mode. Sends ARP requests to find hosts, which community monitoring instruments may detect. It is notably helpful when mapping a community the place not all hosts are lively on the time of the scan. So long as these hosts are on-line, they are going to reply to the ARP request even when they don’t seem to be actively sending and receiving different knowledge. That is Netdiscover’s default mode.
- Passive mode. Sniffs lively visitors to accumulate MAC tackle info as an alternative of querying hosts. Most community monitoring instruments will not choose up this sort of scan, however Netdiscover’s passive mode will not detect inactive community nodes and is way slower than an lively scan. Use the -p flag to specify passive mode.
Netdiscover additionally identifies a community interface card’s (NIC) vendor. Every {hardware} vendor is assigned a vendor ID that makes up the primary half of the NIC’s MAC tackle. Netdiscover can evaluate outcomes towards a database of distributors.
Methods to map a community with Netdiscover
Netdiscover doesn’t have a GUI, so plan to work within the Linux terminal to conduct your scans. That is typical of many Linux cybersecurity instruments.
Notice that routers may block ARP broadcasts. For finest outcomes, run Netdiscover on every community subnet. Condense the outcomes right into a single map or report from the person outcomes.
The varied Netdiscover scans output an identical desk of outcomes, together with IP tackle, MAC tackle, NIC vendor and hostname (if resolvable).
To run a primary scan, sort:
netdiscover
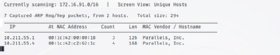
Use Ctrl+C to finish the scan.
You in all probability need to focus this scan extra successfully. Add the -i
netdiscover -i eth0 -r 192.168.2.0/24
This instance runs an lively scan on the subnet. Add the -p possibility for a passive scan, as seen under:
netdiscover -p
Contemplate quick scan when you’re doing primary mapping by yourself community — and due to this fact need not cover from an IDS. This selection may also assist when you scan a congested community with many hosts.
netdiscover -f
You may want Netdiscover to run passively for long-term monitoring. Start Netdiscover with a normal lively scan after which permit it to run passively after that to keep up info. The choice for this configuration is -L. The command is:
netdiscover -L
The preliminary lively scan gathers info shortly. The remaining passive mode retains the data present over time.
Keep in mind that you need to use many of those choices in conjunction to completely customise the instrument to your wants.
Netdiscover use circumstances
When studying how one can use Netdiscover, you will discover it is for anybody who must establish the techniques on a community. Examples embody the next:
- Admins mapping community environments.
- Safety professionals conducting audits and penetration testing.
- Community technicians troubleshooting community incidents.
- Wardriving/strolling and reconnaissance.
- Community and safety admins checking for rogue gadgets on wired and wi-fi networks.
- IT professionals conducting machine inventories.
- Community technicians needing to establish NIC distributors.
Plan to make use of Netdiscover while you want a quick, environment friendly method of discovering community nodes.
Netdiscover vs. Nmap: What is the distinction?
Most directors use Nmap as their main community discovery and for good cause: It is highly effective, versatile and returns a broad vary of outcomes. So, how does Netdiscover differ, and when is the precise time to make use of every?
Nmap operates at OSI Layer 3. It provides way more in depth scan choices, together with the next:
- Host discovery.
- Port scanning.
- OS identification.
- Vulnerability scanning.
Nmap provides complete scans of almost any info you want for pen testing, service mapping and host identification.
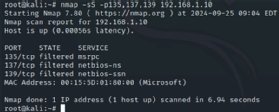
In some circumstances, nonetheless, Nmap is perhaps greater than you want for primary mapping or reconnaissance. In these conditions, Netdiscover provides a light-weight possibility that successfully maps community hosts with out the added burden of extraneous info or producing extra community visitors than mandatory. It is excellent for primary host enumeration on a number of native subnets. You will discover Netdiscover is a superb instrument to make use of in tandem with Nmap or when you do not want Nmap’s extraordinary capabilities.
The subsequent time it’s essential to discover all hosts on a phase or examine for unauthorized gadgets, think about using Netdiscover.
Damon Garn owns Cogspinner Coaction and offers freelance IT writing and modifying companies. He has written a number of CompTIA examine guides, together with the Linux+, Cloud Necessities+ and Server+ guides, and contributes extensively to Informa TechTarget, The New Stack and CompTIA Blogs.










