As soon as behind the captive portal, the web page initiates the Home windows Take a look at Connectivity Standing Indicator, a professional service that determines whether or not a tool has Web entry by sending an HTTP GET request to hxxp://www.msftconnecttest[.]com/redirect. That website, in flip, redirects the browser to msn[.]com. As Thursday’s put up defined:
As soon as the system opens the browser window to this deal with, the system is redirected to a separate actor-controlled area that probably shows a certificates validation error which prompts the goal to obtain and execute ApolloShadow. Following execution, ApolloShadow checks for the privilege stage of the ProcessToken and if the gadget is just not working on default administrative settings, then the malware shows the consumer entry management (UAC) pop-up window to immediate the consumer to put in certificates with the file title CertificateDB.exe, which masquerades as a Kaspersky installer to put in root certificates and permit the actor to realize elevated privileges within the system.
The next diagram illustrates the an infection chain:

ApolloShadow invokes the GetTokenInformationType API to test if it has enough system rights to put in the foundation certificates. If not, the malware makes use of a classy course of that spoofs a web page at hxxp://timestamp.digicert[.]com/registered, which in flip sends the system a second-stage payload within the type of a VBScript.
As soon as decoded, ApolloShadow relaunches itself and presents the consumer with a Consumer Entry Management window looking for to raise its system entry. (Microsoft supplied many extra technical particulars in regards to the method in Thursday’s put up.)
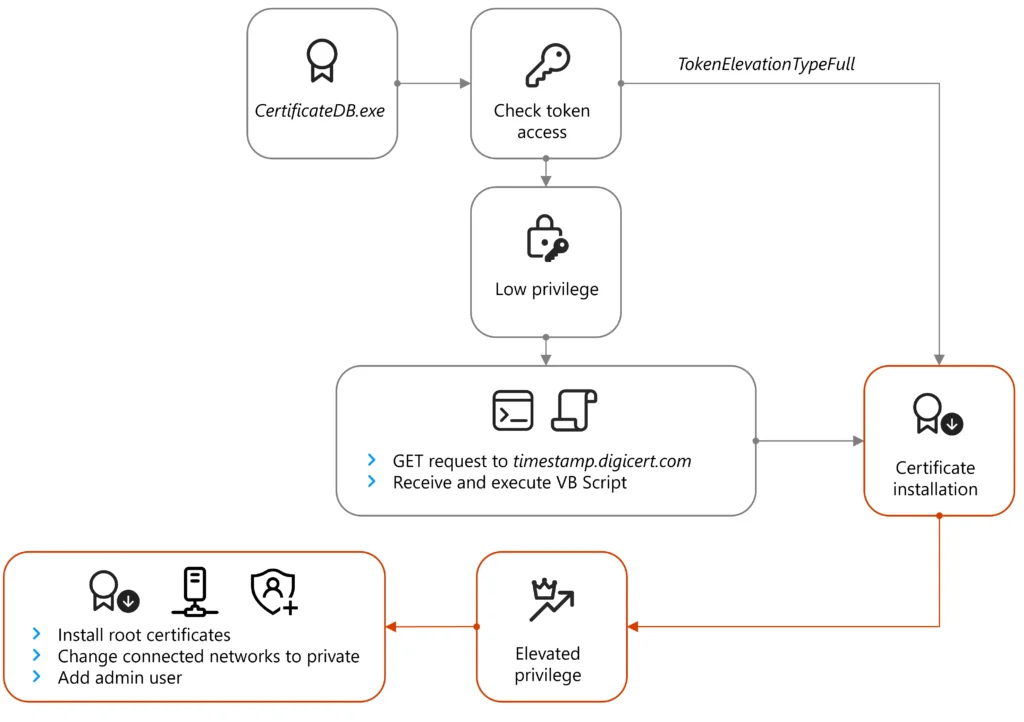
If ApolloShadow already has enough system rights, the malware configures all networks the host connects to as non-public.
“This induces a number of adjustments together with permitting the host gadget to turn out to be discoverable and enjoyable firewall guidelines to allow file sharing,” Microsoft defined. “Whereas we didn’t see any direct makes an attempt for lateral motion, the primary purpose for these modifications is prone to scale back the issue of lateral motion on the community.” (The Microsoft put up additionally supplied technical particulars about this system.)
Microsoft stated the power to trigger contaminated gadgets to belief malicious websites permits the menace actor to take care of persistence, probably to be used in intelligence assortment.
The corporate is advising all clients working in Moscow, notably delicate organizations, to tunnel their visitors by means of encrypted tunnels that hook up with a trusted ISP.










