Cybersecurity researchers from CYFIRMA have revealed a brand new model of Neptune RAT, a distant administration software focusing on Home windows gadgets. Marketed on platforms like GitHub, Telegram, and YouTube with claims of being the “Most Superior RAT,” the malware is attracting each newcomers to cybercrime and seasoned hackers on the lookout for a ready-made software.
What Is Neptune RAT?
Neptune RAT is written in Visible Fundamental .NET and is designed to take management of a sufferer’s Home windows pc. Though its creator says the software program is supplied for “instructional and moral functions,” the software’s capabilities recommend in any other case.
Designed to steal consumer credentials, change cryptocurrency pockets addresses, and even lock information with ransomware options, Neptune RAT offers attackers complete management over an contaminated system.
How It Spreads
The malware is distributed freely on social platforms. Fairly than releasing the supply code, the developer hides the executable file, making the evaluation extra difficult. A number of the malicious code even replaces components of its strings with Arabic characters and emojis, which complicates reversing efforts by researchers. In its free model, Neptune RAT robotically generates PowerShell instructions to obtain and run extra parts hosted on file internet hosting service reminiscent of catbox.moe.
Harmful Capabilities
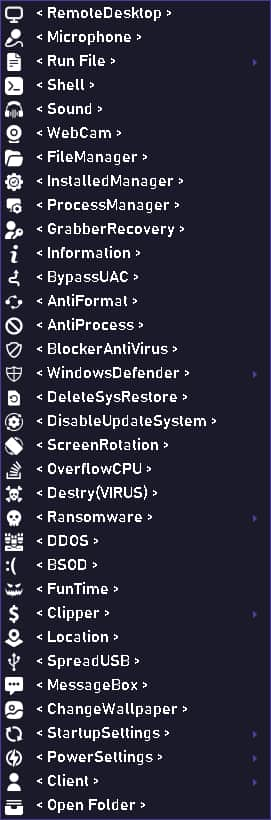
Neptune RAT comes with a mixture of modules that work collectively to compromise Home windows computer systems, together with the next:
- Credential Theft and Clipboard Hijacking: The malware features a password grabber that extracts login particulars from purposes and widespread internet browsers. It additionally displays the clipboard to detect cryptocurrency pockets addresses, changing them with the attacker’s personal.
- Ransomware and System Harm: As soon as activated, the RAT can encrypt information on the sufferer’s pc, extending their extensions to “.ENC, ”and drop an HTML file with ransom info. It might even corrupt system parts just like the Grasp Boot File if an attacker needs to render the system unusable.
- Evasion and Persistence: To keep away from being eliminated, the malware modifies registry values and provides itself to the Home windows Activity Scheduler. It additionally checks if it’s working in a digital atmosphere and stops execution if a digital machine is detected. This mix of strategies helps it preserve a persistent foothold on the system.
- Further Modules: Separate DLL information add additional capabilities, together with bypassing consumer account controls, stealing information from numerous electronic mail and browser purposes, and even enabling stay display monitoring.
Defending Your System
Since Neptune RAT makes use of totally different methods, each people and organizations have to act rapidly to guard themselves. The perfect method begins with some easy practices: solely obtain software program from sources you belief, make sure that Home windows and all of your packages, particularly safety instruments, are stored updated, and usually again up any necessary information.
It’s additionally a good suggestion to make use of anti-virus software program that may regulate each file modifications and community exercise, supplying you with higher safety towards something suspicious.
Knowledgeable Perception
Satish Swargam, Principal Safety Guide at Black Duck in Burlington, Massachusetts, supplied his perspective on Neptune RAT’s evolution. He defined that the malware makes use of superior strategies to extract delicate information from customers, spreading by means of platforms like GitHub, Telegram, and YouTube in ways in which slip previous customary safety instruments.
“This software is particularly regarding as a result of it may well deploy ransomware to lock your information, resulting in main interruptions for companies till the ransom is paid. It additionally lets hackers spy on screens in actual time and even swap clipboard contents with their very own cryptocurrency pockets addresses,” Swargam famous.
He added that because the malware continues so as to add new options, just like these shared on-line below the banner of instructional software program, organizations want to keep up fixed monitoring, deploy robust endpoint defenses, and implement energetic menace detection measures to scale back the danger of compromise.