A latest evaluation printed by Infoblox reveals a complicated phishing operation, dubbed Morphing Meerkat, actively exploiting DNS vulnerabilities for years to conduct extremely efficient phishing campaigns.
In response to researchers, this operation makes use of a phishing-as-a-service (PhaaS) platform, enabling each technical and non-technical cybercriminals to launch focused assaults.
The platform is supplied with instruments to bypass safety methods, together with the exploitation of open redirects on adtech servers, redirection by means of compromised WordPress web sites, and the usage of DNS MX information to determine sufferer e-mail service suppliers. Additionally, they use mass spam supply and dynamic content material tailoring to evade conventional safety measures.
“We’ve found a phishing equipment that creatively employs DNS mail alternate (MX) information to dynamically serve pretend, tailor-made, login pages, spoofing over 100 manufacturers,” researchers famous within the weblog post, shared with Hackread.com forward of its launch.
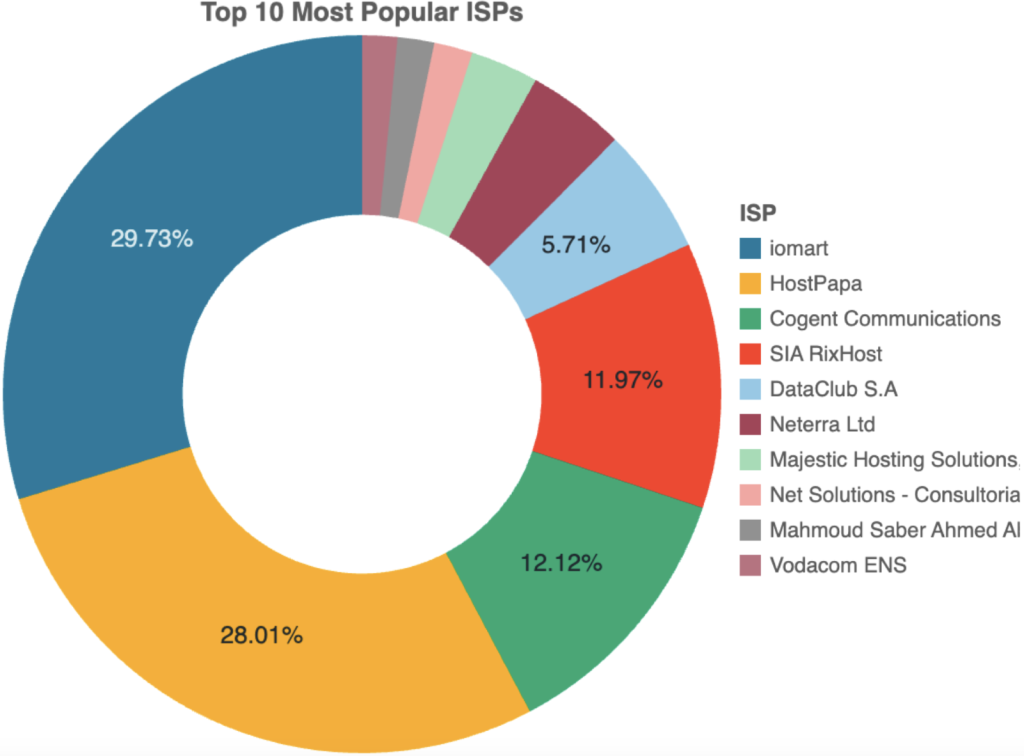
Concerning the distribution of spam emails, the platform’s major assault vector, researchers noticed a definite centralization sample, with a substantial portion originating from servers hosted by iomart (United Kingdom) and HostPapa (United States), indicating a unified community reasonably than dispersed exercise from a number of impartial entities.
Morphing Meerkat makes use of a dynamic serving of faux login pages custom-made to the sufferer’s e-mail service supplier by querying DNS MX information utilizing Cloudflare DoH or Google Public DNS. The platform maps these information to corresponding phishing HTML recordsdata, that includes over 114 distinctive model designs, guaranteeing a personalised phishing expertise and rising the chance of profitable credential theft.
The operation has developed considerably since its detection in January 2020. Initially, it focused solely 5 e-mail manufacturers (Gmail, Outlook, AOL, Workplace 365, and Yahoo) and lacked translation capabilities. By July 2023, it had built-in DNS MX records-based dynamic loading of phishing pages and now helps dynamic translation into over a dozen languages, together with English, Korean, Spanish, Russian, German, Chinese language, and Japanese.
To reap stolen credentials, they make the most of a number of strategies, together with e-mail supply by way of EmailJS, PHP scripts, AJAX requests, and communication with Telegram channels utilizing internet API hooks. The platform additionally implements anti-analysis measures, corresponding to disabling keyboard shortcuts and mouse right-clicks and obfuscating code to hinder safety researchers.
As Infoblox factors out, “reasonably superior web customers and safety researchers typically confirm the malicious state of a phishing webpage by analyzing its HTML code.” Morphing Meerkat counters this by actively blocking such inspection.
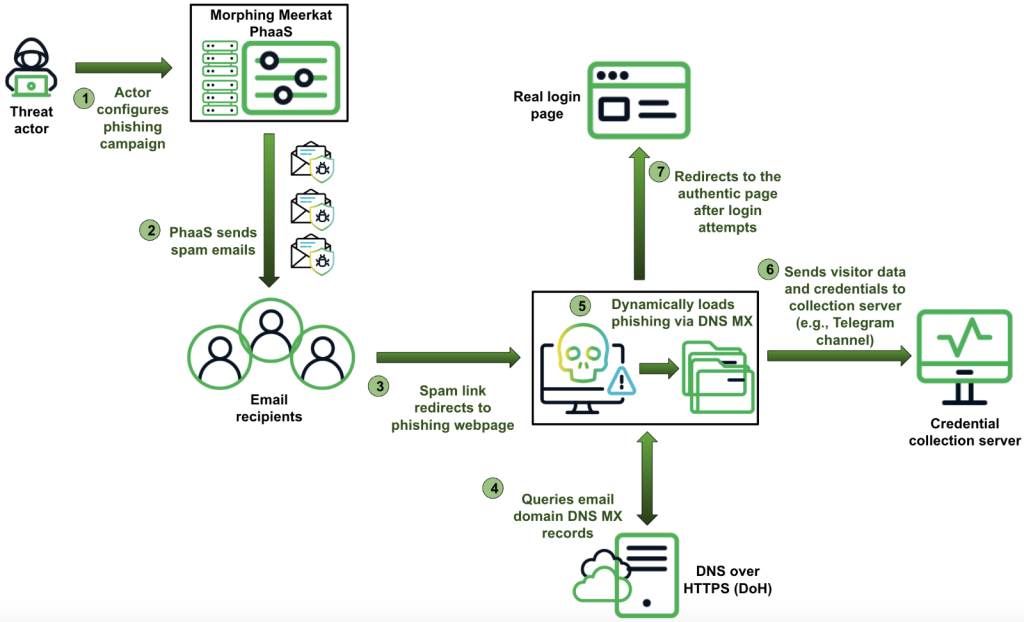
The usage of open redirect vulnerabilities on adtech platforms, notably DoubleClick, permits the menace actors to bypass e-mail safety methods by leveraging the area’s excessive popularity. The platform additionally employs cloaking methods, redirecting customers to reputable login pages and inflating code with non-functional parts, complicating menace evaluation.
Contemplating the platform’s potential to use safety blind spots by means of open redirects, DoH communication, and file-sharing companies, it’s important that organizations strengthen DNS safety, prohibit DoH communication, and restrict entry to non-essential infrastructure to stop exploitation.