As customers proceed to evaluate the Below Armour information breach, WorldLeaks, the rebranded model of the Hunters Worldwide ransomware group, is claiming to have breached Nike, Inc., a serious U.S.-based athletic footwear and attire firm.
The claims had been printed on the group’s official darkish internet leak website on Thursday, January 22, 2026. Over the weekend, WorldLeaks up to date the submit with what it says is supporting proof, alleging that the attackers exfiltrated greater than 1.4 terabytes of Nike information with 188,347 recordsdata that are actually being leaked on-line.
It’s value noting that the identical group was behind the Dell information breach in July 2025, during which it stole 1.3tb of information and later leaked it on-line.
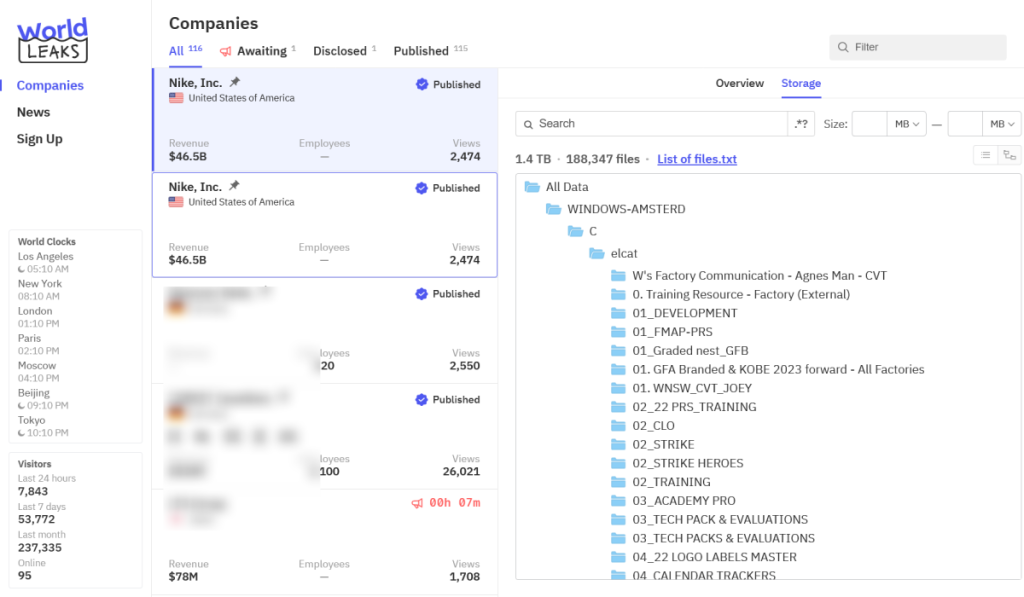
The Leaked Information
A fast evaluation of the folder names and recordsdata suggests the leaked information is closely centered on product improvement, manufacturing, and manufacturing unit operations. Many directories reference tech packs, schematics, BOMs, graded nests, coaching supplies, wash checks, trim calculators, and dimension units. This factors to detailed design specs for attire and sportswear throughout a number of seasons, together with future collections.
There are additionally repeated references to manufacturing unit companions, onsite coaching, inspections, dashboards, and inside workflows, which possible include operational paperwork shared between Nike groups and exterior producers. In sensible phrases, this might expose how merchandise are designed, examined, costed, and produced earlier than they ever attain shops.
The recordsdata additionally seem to incorporate inside shows, technique paperwork, art work, movies, and collaboration supplies tied to particular product strains, athletes, groups, and areas. File names reference Jordan, girls’s efficiency put on, coaching gear, tennis, golf, and federation or league-related attire, alongside art work recordsdata, embroidery designs, print layouts, and innovation decks.
There are additionally recordings, PDFs, and spreadsheets that recommend inside conferences, planning classes, and long-term improvement roadmaps. Whereas there isn’t any apparent signal of buyer cost information on this snapshot, the amount and nature of the fabric point out a deep look into Nike’s inside processes, provider relationships, and unreleased product ideas, data that will usually by no means be public.
Nike’s Response
Nike responded rapidly, stating that it’s investigating claims surfaced by WorldLeaks. “We all the time take client privateness and information safety very critically. We’re investigating a possible cybersecurity incident and are actively assessing the scenario,” the corporate stated.
Hackread.com is monitoring the scenario, and this text will likely be up to date as extra data turns into accessible.










