A 22-year-old Oregon man has been arrested on suspicion of working “Rapper Bot,” a large botnet used to energy a service for launching distributed denial-of-service (DDoS) assaults towards targets — together with a March 2025 DDoS that knocked Twitter/X offline. The Justice Division asserts the suspect and an unidentified co-conspirator rented out the botnet to on-line extortionists, and tried to remain off the radar of legislation enforcement by guaranteeing that their botnet was by no means pointed at KrebsOnSecurity.
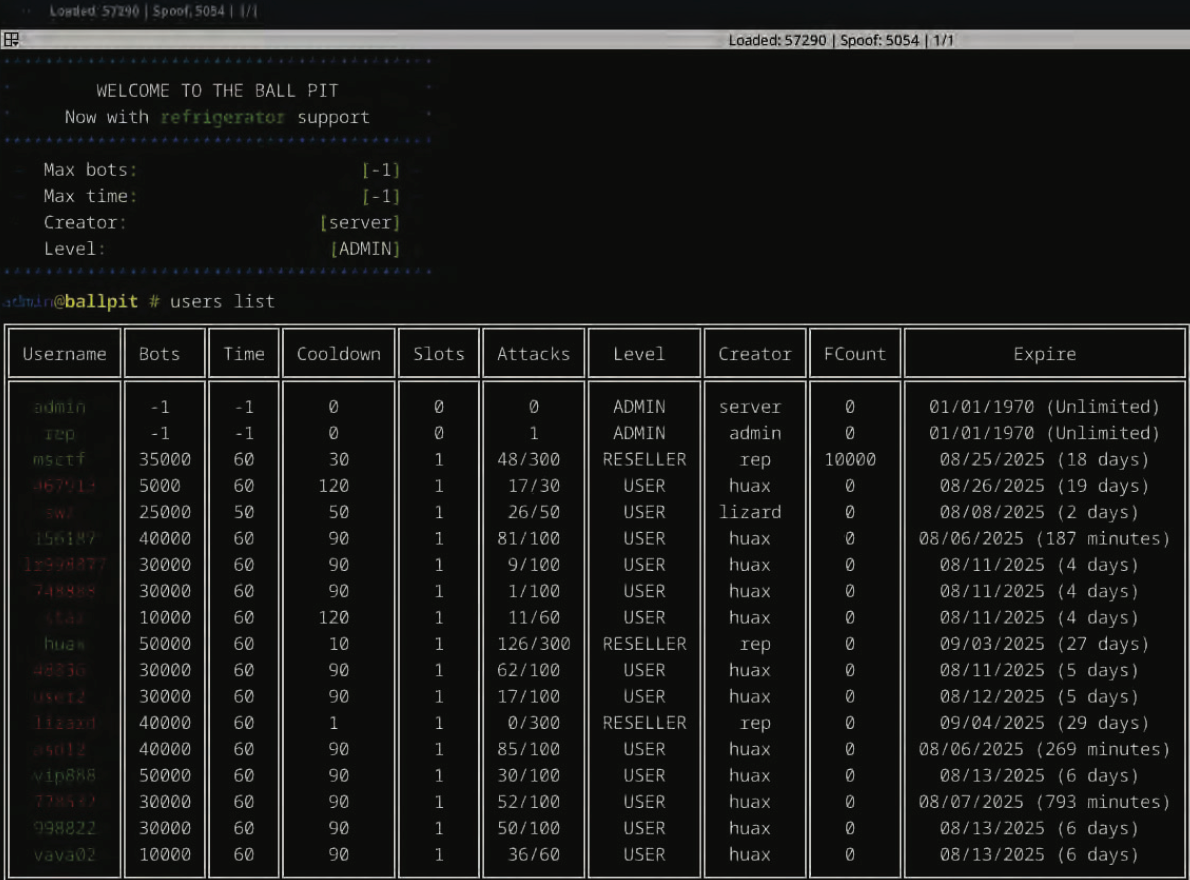
The management panel for the Rapper Bot botnet greets customers with the message “Welcome to the Ball Pit, Now with fridge assist,” an obvious reference to a handful of IoT-enabled fridges that had been enslaved of their DDoS botnet.
On August 6, 2025, federal brokers arrested Ethan J. Foltz of Springfield, Ore. on suspicion of working Rapper Bot, a globally dispersed assortment of tens of 1000’s of hacked Web of Issues (IoT) units.
The grievance towards Foltz explains the assaults normally clocked in at greater than two terabits of junk knowledge per second (a terabit is one trillion bits of information), which is greater than sufficient site visitors to trigger critical issues for all however essentially the most well-defended targets. The federal government says Rapper Bot persistently launched assaults that had been “lots of of occasions bigger than the anticipated capability of a typical server situated in a knowledge middle,” and that a few of its largest assaults exceeded six terabits per second.
Certainly, Rapper Bot was reportedly accountable for the March 10, 2025 assault that prompted intermittent outages on Twitter/X. The federal government says Rapper Bot’s most profitable and frequent clients had been concerned in extorting on-line companies — together with quite a few playing operations based mostly in China.
The prison grievance was written by Elliott Peterson, an investigator with the Protection Legal Investigative Service (DCIS), the prison investigative division of the Division of Protection (DoD) Workplace of Inspector Common. The grievance notes the DCIS acquired concerned as a result of a number of Web addresses maintained by the DoD had been the goal of Rapper Bot assaults.
Peterson stated he tracked Rapper Bot to Foltz after a subpoena to an ISP in Arizona that was internet hosting one of many botnet’s management servers confirmed the account was paid for by way of PayPal. Extra authorized course of to PayPal revealed Foltz’s Gmail account and beforehand used IP addresses. A subpoena to Google confirmed the defendant searched safety blogs consistently for information about Rapper Bot, and for updates about competing DDoS-for-hire botnets.
In accordance with the grievance, after having a search warrant served on his residence the defendant admitted to constructing and working Rapper Bot, sharing the income 50/50 with an individual he claimed to know solely by the hacker deal with “Slaykings.” Foltz additionally shared with investigators the logs from his Telegram chats, whereby Foltz and Slaykings mentioned how greatest to remain off the radar of legislation enforcement investigators whereas their rivals had been getting busted.
Particularly, the 2 hackers chatted about a Might 20 assault towards KrebsOnSecurity.com that clocked in at greater than 6.3 terabits of information per second. The temporary assault was notable as a result of on the time it was the most important DDoS that Google had ever mitigated (KrebsOnSecurity sits behind the safety of Undertaking Defend, a free DDoS protection service that Google supplies to web sites providing information, human rights, and election-related content material).
The Might 2025 DDoS was launched by an IoT botnet known as Aisuru, which I found was operated by a 21-year-old man in Brazil named Kaike Southier Leite. This particular person was extra generally recognized on-line as “Forky,” and Forky advised me he wasn’t afraid of me or U.S. federal investigators. However, the grievance towards Foltz notes that Forky’s botnet appeared to decrease in measurement and firepower on the similar time that Rapper Bot’s an infection numbers had been on the upswing.
“Each FOLTZ and Slaykings had been very dismissive of consideration looking for actions, essentially the most excessive of which, of their view, was to launch DDoS assaults towards the web site of the outstanding cyber safety journalist Brian Krebs,” Peterson wrote within the prison grievance.
“You see, they’ll get themselves [expletive],” Slaykings wrote in response to Foltz’s feedback about Forky and Aisuru bringing an excessive amount of warmth on themselves.
“Prob cuz [redacted] hit krebs,” Foltz wrote in reply.
“Going towards Krebs isn’t an excellent transfer,” Slaykings concurred. “It isn’t about being a [expletive] or afraid, you simply get a whole lot of issues for zero cash. Infantile, however good. Allow them to die.”
“Ye, it’s good tho, they may die,” Foltz replied.
The federal government states that simply previous to Foltz’s arrest, Rapper Bot had enslaved an estimated 65,000 units globally. That will sound like rather a lot, however the grievance notes the defendants weren’t excited by making headlines for constructing the world’s largest or strongest botnet.
Fairly the opposite: The grievance asserts that the accused took care to keep up their botnet in a “Goldilocks” measurement — guaranteeing that “the variety of units afforded highly effective assaults whereas nonetheless being manageable to regulate and, within the hopes of Foltz and his companions, sufficiently small to not be detected.”
The grievance states that a number of days later, Foltz and Slaykings returned to discussing what that they anticipated to befall their rival group, with Slaykings stating, “Krebs may be very revenge. He gained’t cease till they’re [expletive] to the bone.”
“Stunned they’ve any bots left,” Foltz answered.
“Krebs is just not the one you wish to have in your again. Not as a result of he’s scary or one thing, simply because he won’t hand over UNTIL you’re [expletive] [expletive]. Proved it with Mirai and lots of different instances.”
[Unknown expletives aside, that may well be the highest compliment I’ve ever been paid by a cybercriminal. I might even have part of that quote made into a t-shirt or mug or something. It’s also nice that they didn’t let any of their customers attack my site — if even only out of a paranoid sense of self-preservation.]
Foltz admitted to wiping the person and assault logs for the botnet roughly as soon as every week, so investigators had been unable to tally the entire variety of assaults, clients and targets of this huge crime machine. However the knowledge that was nonetheless accessible confirmed that from April 2025 to early August, Rapper Bot carried out over 370,000 assaults, focusing on 18,000 distinctive victims throughout 1,000 networks, with the majority of victims residing in China, Japan, america, Eire and Hong Kong (in that order).
In accordance with the federal government, Rapper Bot borrows a lot of its code from fBot, a DDoS malware pressure also called Satori. In 2020, authorities in Northern Eire charged a then 20-year-old man named Aaron “Vamp” Sterritt with working fBot with a co-conspirator. U.S. prosecutors are nonetheless looking for Sterritt’s extradition to america. fBot is itself a variation of the Mirai IoT botnet that has ravaged the Web with DDoS assaults since its supply code was leaked again in 2016.
The grievance says Foltz and his accomplice didn’t permit most clients to launch assaults that had been greater than 60 seconds in length — one other approach they tried to maintain public consideration to the botnet at a minimal. Nonetheless, the federal government says the proprietors additionally had particular preparations with sure high-paying shoppers that allowed a lot bigger and longer assaults.
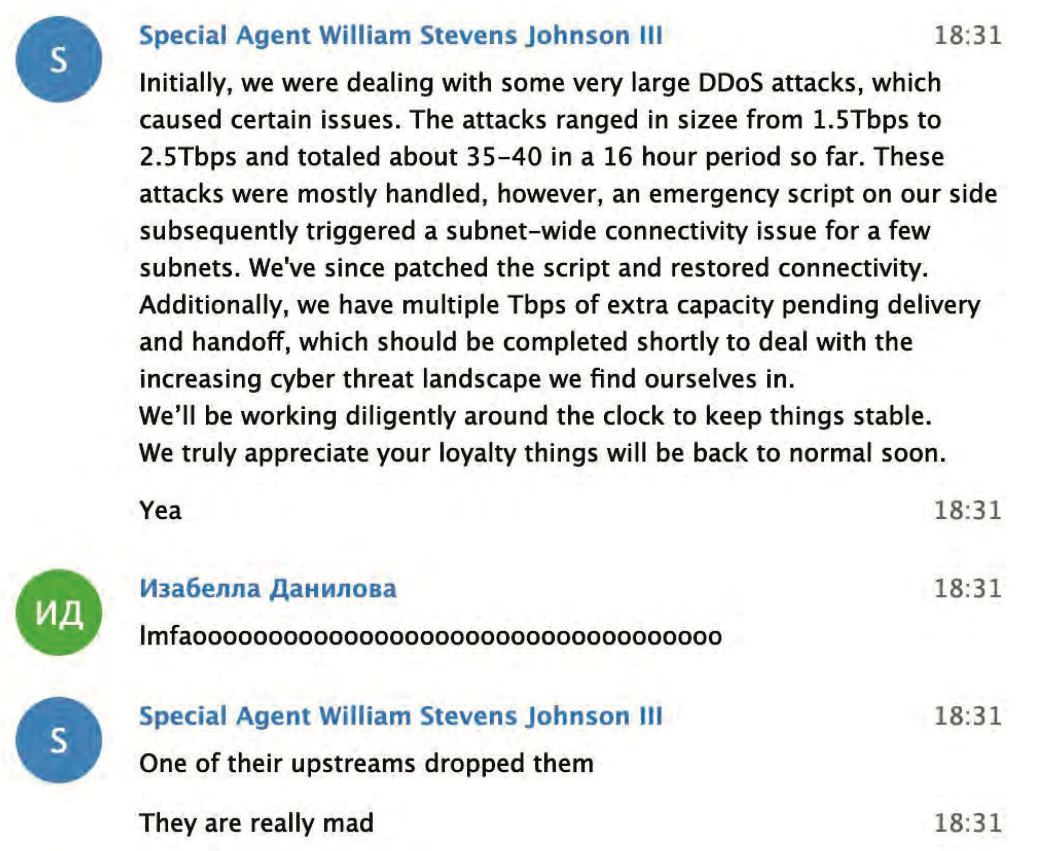
The accused and his alleged accomplice made gentle of this weblog publish in regards to the fallout from one in all their botnet assaults.
Most individuals who’ve by no means been on the receiving finish of a monster DDoS assault do not know of the associated fee and disruption that such sieges can carry. The DCIS’s Peterson wrote that he was capable of check the botnet’s capabilities whereas interviewing Foltz, and that discovered that “if this had been a server upon which I used to be working a web site, utilizing providers comparable to load balancers, and paying for each outgoing and incoming knowledge, at estimated business common charges the assault (2+ Terabits per second occasions 30 seconds) may need value the sufferer anyplace from $500 to $10,000.”
“DDoS assaults at this scale usually expose victims to devastating monetary affect, and a possible various, community engineering options that mitigate the anticipated assaults comparable to overprovisioning, i.e. growing potential Web capability, or DDoS protection applied sciences, can themselves be prohibitively costly,” the grievance continues. “This ‘rock and a tough place’ actuality for a lot of victims can go away them acutely uncovered to extortion calls for – ‘pay X {dollars} and the DDoS assaults cease’.”
The Telegram chat data present that the day earlier than Peterson and different federal brokers raided Foltz’s residence, Foltz allegedly advised his accomplice he’d discovered 32,000 new units that had been weak to a beforehand unknown exploit.

Foltz and Slaykings discussing the invention of an IoT vulnerability that may give them 32,000 new units.
Shortly earlier than the search warrant was served on his residence, Foltz allegedly advised his accomplice that “As soon as once more now we have the largest botnet locally.” The next day, Foltz advised his accomplice that it was going to be an ideal day — the largest thus far by way of revenue generated by Rapper Bot.
“I sat subsequent to Foltz whereas the messages poured in — guarantees of $800, then $1,000, the proceeds ticking up because the day went on,” Peterson wrote. “Noticing a change in Foltz’ conduct and anxious that Foltz was making modifications to the botnet configuration in actual time, Slaykings requested him ‘What’s up?’ Foltz deftly typed out some fast responses. Reassured by Foltz’ reply, Slaykings responded, ‘Okay, I’m the paranoid one.”
The case is being prosecuted by Assistant U.S. Legal professional Adam Alexander within the District of Alaska (not less than a few of the units discovered to be contaminated with Rapper Bot had been situated there, and it’s the place Peterson is stationed). Foltz faces one rely of aiding and abetting laptop intrusions. If convicted, he faces a most penalty of 10 years in jail, though a federal decide is unlikely to award anyplace close to that form of sentence for a first-time conviction.