Cybersecurity consultants are elevating alarms over the proliferation of more and more subtle phishing methods that leverage devoted Phishing-as-a-Service (PhaaS) toolkits to create authentic-looking pages.
These superior instruments enable even technically inexperienced attackers to generate convincing replicas of reputable web sites in real-time, considerably enhancing the effectiveness of credential-harvesting campaigns.
Phishing stays some of the persistent cybersecurity threats within the digital panorama.
Whereas the final word goal-stealing login credentials and delicate information-hasn’t modified, the strategies employed by attackers proceed to evolve at a regarding tempo.
The emergence of dynamically generated phishing pages represents a big development in these malicious methods.
In contrast to conventional phishing that required manually cloning goal web sites, trendy PhaaS toolkits automate the method, enabling attackers to spin up convincing replicas instantaneously.
LogoKit, a infamous instance of such toolsets that first surfaced in 2021, continues to be actively utilized in phishing campaigns worldwide.
Dynamic Phishing Assaults Unfold
The assault sometimes begins with a misleading e-mail designed to create urgency or curiosity, compelling recipients to click on with out cautious consideration.
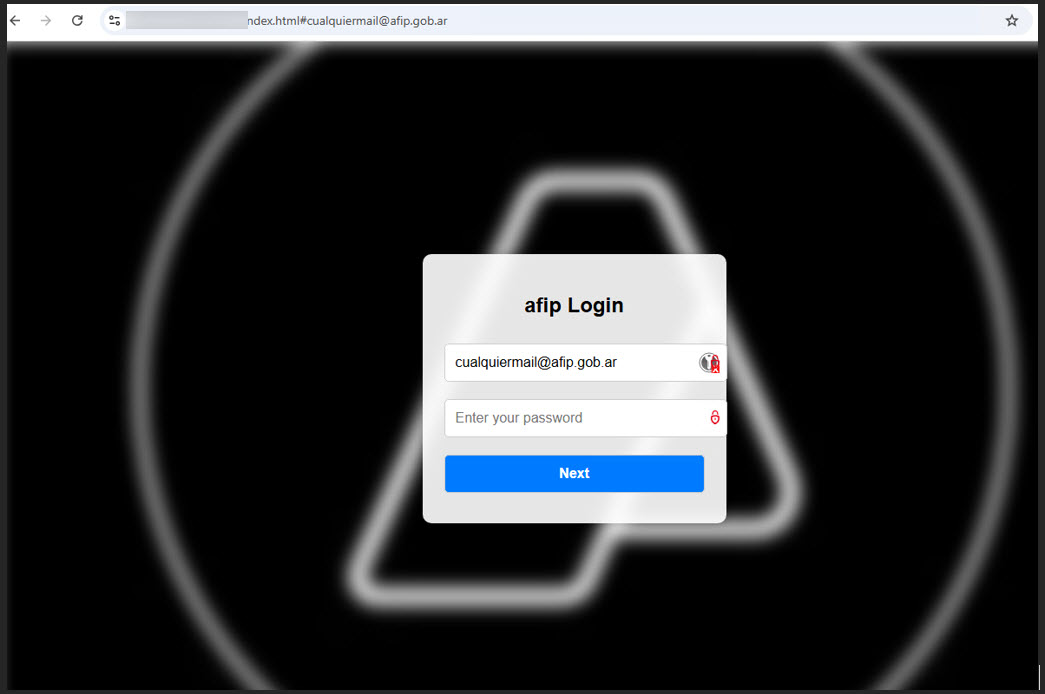
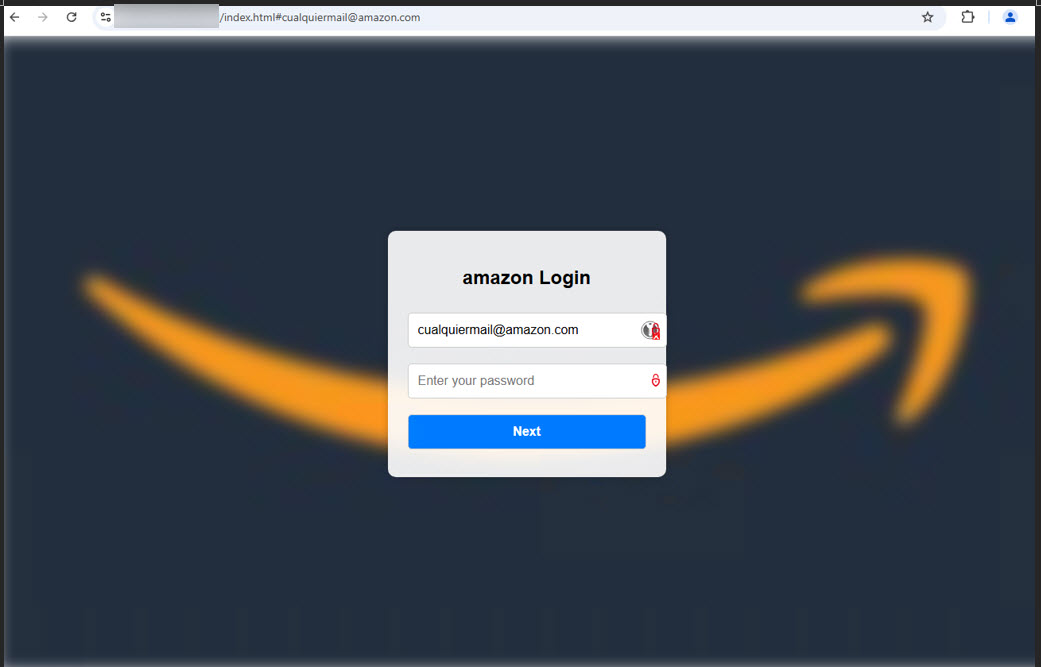
As soon as clicked, victims are directed to a complicated credential-harvesting website that dynamically retrieves branding parts of the impersonated firm.
These malicious pages leverage reputable third-party advertising and marketing providers like Clearbit by means of their APIs to fetch company logos and visible identifiers in real-time.
This system creates a convincing façade that may idiot even cautious customers. Including to the deception, attackers usually pre-populate fields with the sufferer’s e-mail handle or identify, creating the phantasm that the person has beforehand visited the positioning.
When victims enter their credentials, the knowledge is straight away transmitted to attackers through AJAX POST requests.
The web page then redirects to the reputable web site, leaving victims unaware that their delicate info has been compromised.
The PhaaS mannequin supplies a number of vital advantages for cybercriminals.
The true-time customization capabilities enable attackers to tailor phishing pages immediately for any goal group.
By incorporating genuine visible parts, these assaults extra successfully evade detection by each human customers and automatic safety techniques.
The infrastructure supporting these campaigns is often light-weight and simply deployed throughout numerous cloud platforms, together with Firebase, Oracle Cloud, and GitHub.
This agility makes the assaults each scalable and troublesome for safety groups to determine and neutralize shortly.
Maybe most regarding is the democratization of those assault capabilities.
PhaaS toolkits are available on underground boards, reducing the technical barrier to entry and enabling even novice attackers to launch subtle phishing campaigns.
Protecting Measures In opposition to Superior Phishing
Defending in opposition to these evolving threats requires a multi-layered method combining person consciousness and sturdy technical controls.
Safety consultants advocate verifying communications independently quite than clicking embedded hyperlinks in suspicious messages.
Customers ought to navigate on to reputable web sites or contact organizations by means of trusted channels.
Implementing robust, distinctive passwords for all on-line accounts stays important, particularly when mixed with two-factor authentication (2FA).
Safety professionals significantly advocate app-based or {hardware} token 2FA choices over SMS codes for enhanced safety.
Complete safety options with superior anti-phishing capabilities present one other essential layer of protection in opposition to these subtle assaults.
The emergence of AI-enhanced phishing presents further challenges, doubtlessly enabling hyper-personalized scams that transfer past templated approaches.
As phishing methods proceed to evolve, sustaining vigilant consciousness coupled with robust technical safeguards stays the best technique for cover in opposition to these ever-morphing threats.
Discover this Information Fascinating! Comply with us on Google Information, LinkedIn, & X to Get On the spot Updates!
.png
)