As soon as a menace actor is on an endpoint, EDR options are sometimes the one impediment between them and their goal – whether or not that’s deploying ransomware, putting in malware, accessing knowledge, or launching additional assaults.
Consequently, menace actors usually search for methods to disable safety merchandise: escalating privileges if essential to attempt to kill processes and providers, working EDR killers, and a bunch of different strategies.
Tamper safety – a mechanism designed to cease menace actors from interfering with safety merchandise, often enforced by a kernel-mode driver – is subsequently a essential a part of any safety suite, and plenty of distributors, together with Sophos, have developed some type of it.
In step with our earlier efforts to supply transparency round our kernel drivers and content material replace structure, and our dedication to CISA’s Safe By Design initiative, we wished to briefly clarify our tamper safety characteristic and the way it works.
What does tamper safety do?
Because the identify suggests, Sophos’ Tamper Safety is designed to forestall manipulation, both by unauthorized customers or malware, of the Sophos product. It’s an added, however essential, safety on high of what we think about to be our essential function: defending the working system and its functions – and, by extension, customers.
Tamper Safety is enabled by default; Sophos goals for secure-by-default configurations and Tamper Safety isn’t any exception. Whereas it may be turned off by a certified person, we encourage customers to solely achieve this when they should change the native Sophos configuration or uninstall an present Sophos product. Safe defaults are an essential design precept, as not all organizations have the time or experience to lock down their environments – creating alternatives for attackers.
Crucially, solely a Sophos Central administrator can flip off Tamper Safety, and will need to have the required password, which is generated routinely by Central and is barely accessible to licensed customers with applicable safety roles and multi-factor authentication (MFA), reminiscent of a passkey or an authenticator app. By design, no native or area administrator can override this, or flip off Tamper Safety except they’re additionally a Sophos Central administrator and have the distinctive machine tamper safety password.
Our philosophy right here is that adjustments to Tamper Safety and menace safety coverage shouldn’t be made by the identical accounts used for routine IT administration. As an alternative, we assist role-based administration, enabling the separation of day-to-day IT from essential safety controls.
Tamper Safety prevents the next:
- Altering on-device settings for menace safety, together with on-access scanning, suspicious conduct monitoring, internet safety, and Sophos Reside Safety
- Disabling Tamper Safety
- Uninstalling the Sophos agent software program
- Reinstalling the Sophos agent software program
- Stopping Sophos processes
- Stopping Sophos providers
- Altering Sophos service configuration
- Deleting or altering Sophos recordsdata or folders
- Deleting or altering Sophos registry keys.
Closing the gaps
We’re acutely aware that menace actors are consistently in search of new methods to intrude with safety merchandise. As an illustration, updates or reinstallations can result in protections being briefly disabled, offering a niche for attackers to get a foot within the door and attempt to disable tamper safety methods. With our built-in strategy to endpoint safety, menace engines, and MDR providers, we preserve a novel end-to-end view of contemporary assaults, feeding insights immediately again into growth.
Furthermore, with every little thing we construct, our goal is safety by design – together with replace mechanisms and Tamper Safety. So, for instance:
- We intentionally don’t use MSI for endpoint set up or updates. As an alternative, Sophos Endpoint powered by Intercept X makes use of a proprietary replace system designed to forestall interruption of safety
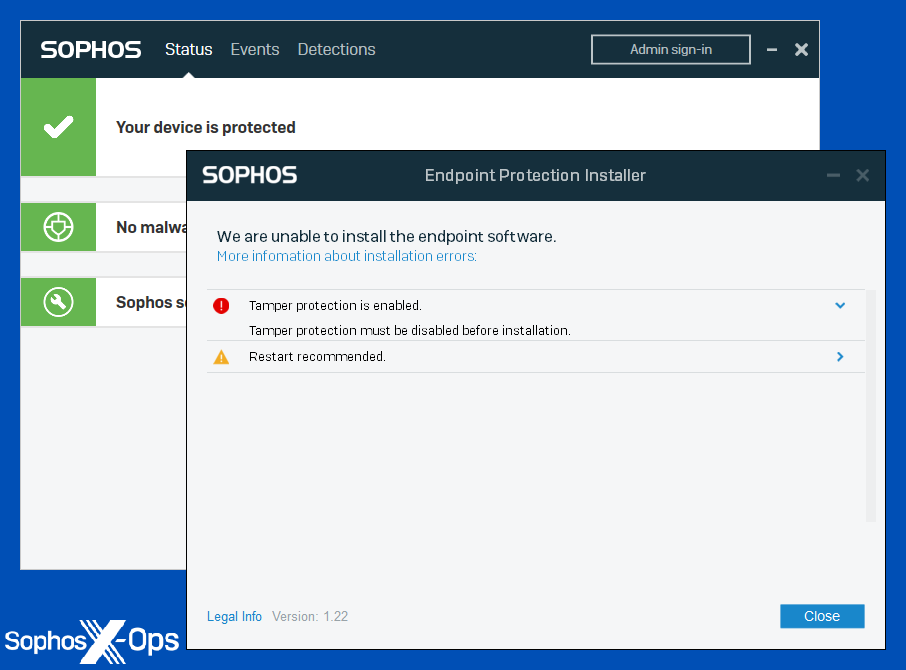
- As famous above, Tamper Safety is on by default, and stays lively throughout updates, upgrades, and downgrades. Its safety extends to processes, providers, software program elements, configuration recordsdata, registry keys, and unauthorized uninstallation and reinstallation
- Part updates happen in parallel, with present elements dealing with operations till handoff is full – leading to zero downtime in safety all through the replace. Core drivers and providers solely improve by way of reboot, eliminating runtime tampering dangers.
Determine 1: Sophos Tamper Safety prevents unauthorized upgrades/downgrades—even from different Sophos installers
Nevertheless, we by no means assume that our defenses are excellent. We’ve got participated in an exterior bug bounty program since December 2017, and we usually take a look at our Tamper Safety by way of inside engineering evaluations, exterior red-teaming, and real-world menace intelligence. That is a part of our safety funding: constantly bettering the components of our methods that actual attackers would possibly attempt to exploit.
Conclusion
Our goal is to make sure your complete safety and replace floor resists tampering, even from attackers with full system entry.
Efficient tamper safety should assume that attackers have administrative rights, perceive how your safety merchandise work, and can exploit any predictable hole. Sophos Endpoint is designed to withstand such makes an attempt with out counting on momentary exceptions or post-failure restoration. Safety stays lively all through all operations, together with updates. This represents our broader Safe by Design strategy, the place system integrity takes precedence over deployment comfort.