Faux Reserving.com emails trick lodge workers into operating AsyncRAT malware through faux CAPTCHA, concentrating on programs with distant entry trojan.
A brand new phishing marketing campaign is concentrating on lodge workers with faux Reserving.com emails, tricking victims into executing malicious instructions on their very own programs. The rip-off seems well-planned, combining social engineering with the top purpose to contaminate and compromise lodge networks with AsyncRAT.
It Begins with a Convincing Electronic mail
The assault begins with a message that seems to come back from Reserving.com. The e-mail claims a visitor has left behind necessary private belongings and urges the lodge supervisor to click on a button labelled “View visitor data.”
The e-mail is well mannered, pressing and designed to look professional, typical of social engineering makes an attempt designed to trick folks into clicking with out pondering.
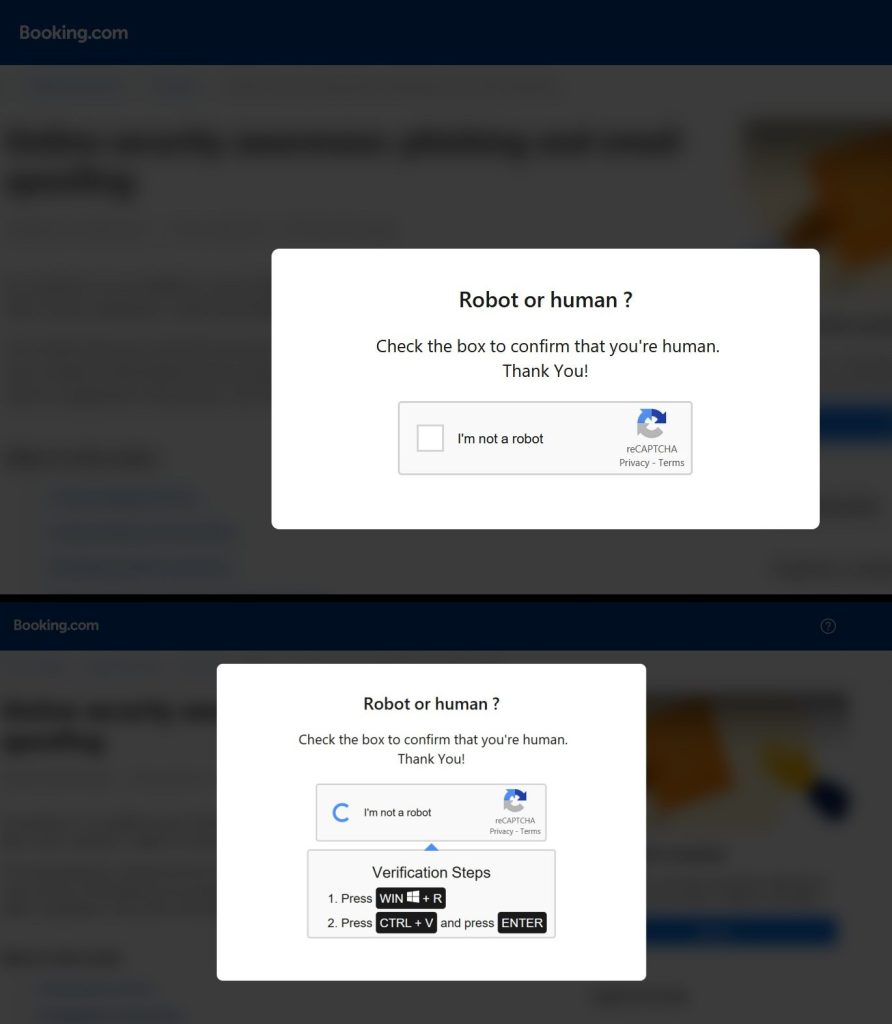
A Faux CAPTCHA Hides the Actual Menace
Clicking the hyperlink takes the consumer to a lookalike Reserving.com website hosted at: reserving.partlet-id739847.com. The web page initially presents a CAPTCHA asking the customer to substantiate they’re not a robotic.
After checking the field, customers are introduced with one thing way more suspicious — a set of directions that inform them to press WIN + R (to open the Home windows Run dialogue), adopted by CTRL + V and Enter. This trick makes use of the clipboard to ship and execute a hidden command.
Behind the Scenes: AsyncRAT
Safety evaluation of the malware delivered on this rip-off exhibits it’s AsyncRAT, a distant entry trojan. This malware has been lively for the reason that second half of 2019 and has gained recognition amongst cybercriminals due to its open-source and extremely customizable options.
AsyncRAT is able to:
- Keystroke logging
- Distant desktop viewing
- File entry and information theft
- Putting in further payloads
- Persistent management over contaminated programs
AsyncRAT has been actively utilized in cyberattacks over the previous few years. In Might 2021, Microsoft noticed AsyncRAT concentrating on aerospace and journey organizations. By November 2021, safety researchers discovered it being delivered alongside different malware households to contaminate programs and steal cryptocurrencies.
In June 2023, cybersecurity agency eSentire reported a brand new variant known as DcRAT, which was embedded in OnlyFans-related content material a rebranded model of AsyncRAT. Then in January 2024, the malware was noticed concentrating on crucial infrastructure in the USA, this time utilizing malicious GIF and SVG information to ship the payload.
The malware runs through MSBuild.exe, a professional Home windows utility, serving to it evade some antivirus instruments. It installs itself within the %AppData% listing and communicates with a command-and-control server at 185.39.17.70 over port 8848.
Why this Phishing Rip-off is Difficult
In contrast to fundamental phishing campaigns that purpose to steal passwords, this one goes a lot additional. It guides the consumer into executing malware manually, a intelligent option to bypass safety restrictions and keep away from triggering downloads.
If profitable, attackers may achieve full distant entry to lodge programs, placing buyer information, reservation data, and fee data in danger.
Ideas for Lodges and Employees
- By no means click on hyperlinks in unsolicited emails, even when they appear official.
- Don’t run instructions primarily based on directions from emails or web sites, particularly something involving the Home windows Run dialogue.
- Verify the area, actual Reserving.com hyperlinks don’t include additional subdomains like
partlet-id739847.
- Report suspicious messages on to Reserving.com through their official companion assist channels.
This marketing campaign is simply one other instance of how phishing has change into a risk by combining lifelike branding with malware execution ways. Lodge managers and workers ought to keep alert and deal with any sudden e mail involving visitor information with warning.