TAMECAT is a complicated PowerShell-based backdoor linked to APT42, an Iranian state-sponsored hacking group.
It steals login credentials from Microsoft Edge and Chrome browsers whereas evading detection.
Safety researchers from Israel’s Nationwide Digital Company detailed its modular design in current SpearSpecter marketing campaign evaluation.
APT42 deploys TAMECAT in long-term espionage operations in opposition to senior protection and authorities officers.
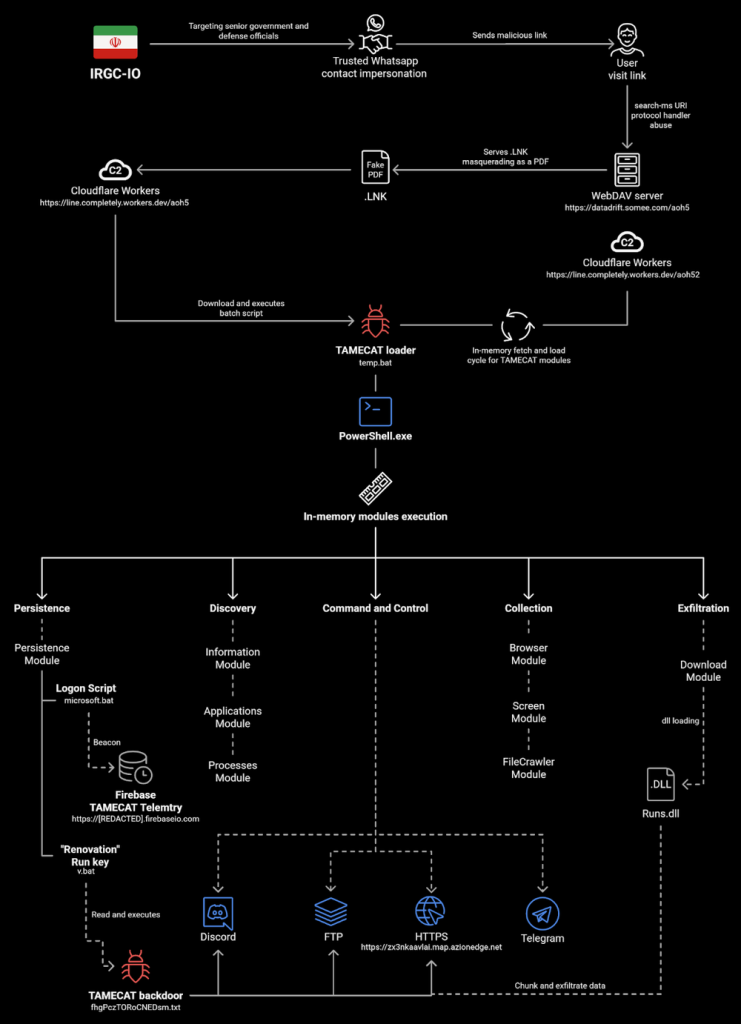
The group builds belief by means of social engineering earlier than compromising programs. TAMECAT receives instructions through Telegram bots, downloading further scripts for duties like display captures and browser information theft, as reported by Pulsedive.
The an infection chain begins with a VBScript downloader (SHA256: 5404e39f2f175a0fc993513ee52be3679a64c69c79e32caa656fbb7645965422). This script scans for antivirus merchandise utilizing WMI queries.
If “Home windows” seems within the AV record, it launches PowerShell through conhost with wget to fetch the loader from tebi[.]io. In any other case, it falls again to cmd.exe and curl for an alternate payload.
Loader Evaluation
The loader, nconf.txt (SHA256: bd1f0fb085c486e97d82b6e8acb3977497c59c3ac79f973f96c395e7f0ca97f8), makes use of AES-encrypted payloads.
It defines Gorba for decryption with key “T2r0y1M1e1n1o0w1” and Borjol for additional processing.
The script drops the primary three bytes from a base64 URL, downloads df32s.txt, and applies bitwise operations plus UTF-8 conversion to disclose extra code.
Decrypted modules deal with sufferer ID technology (written to %LocalAppDatapercentconfig.txt) and C2 communication to accurate-sprout-porpoise[.]glitch[.]me.

It collects OS particulars, laptop title, and a hardcoded token (GILNH9LX6TCZ9V8ZZSUF), encrypts through Borpos (AES-256, key: kNz0CXiP0wEQnhZXYbvraigXvRVYHk1B), and exfils through POST with customized “Content material-DPR” header for the IV.

C2 responses, separated by ¶, embody language (PowerShell/C#), base64 command, thread title, and begin/cease flags.
TAMECAT executes these in-memory, suspending Chrome processes and utilizing Edge’s distant debugging for credential extraction.
TAMECAT creates a Chrome listing in %LocalAppData% and targets saved logins. It leverages browser debugging protocols to dump credentials with out disk writes.

Obfuscation contains array fragments, wildcards, and string substitute traits shared with PowerStar variants.
Person-agent mimics Chrome 119: “Mozilla/5.0 (Home windows NT 10.0; Win64; x64) AppleWebKit/537.36…”. Platforms like Discord complement Telegram for C2 flexibility.
MITRE ATT&CK Mapping
- T1059.001: PowerShell execution.
- T1547: Boot/Logon Autostart (suspected persistence).
- T1555: Credentials from Password Shops (Edge/Chrome).
- T1071.001: Net Protocols (HTTPS C2).
- T1027: Obfuscated Recordsdata/Info.
Deploy EDR/AV to catch course of chains like wscript spawning PowerShell. Allow PowerShell script-block logging and constrain execution insurance policies to signed scripts solely. Monitor VBScript launching interpreters and anomalous browser debugging.
TAMECAT evolves, however layered defenses restrict its affect on high-value targets. Organizations ought to prioritize browser safety and logging amid rising nation-state threats.
Comply with us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most well-liked Supply in Google.










