Ask any safety, community or techniques administrator concerning the high instruments of their toolbox and Nmap is probably going on their checklist. Brief for Community Mapper, the versatile utility does all the things from performing port scans and managing safety configurations to troubleshooting community connections, documenting community environments and monitoring system uptime.
Nmap presents all kinds of options, and its extra scripting choices take it to a good greater degree. It gathers info, guesses OSes, offers efficiency info, lists system particulars comparable to MAC and IP addresses, and extra. As a result of Nmap is open supply, its help and capabilities are almost countless.
One in all Nmap’s most important capabilities to grasp is port scanning. Let’s look at frequent ports and port scanning use circumstances earlier than exploring how you can use Nmap to carry out numerous varieties of port scans.
Nmap port scanning 101
Ports are communication endpoints via which information flows. Port numbers vary from 0 to 65535:
- Port 0 is a reserved port that isn’t meant to be used in TCP or Person Datagram Protocol (UDP) messages.
- Ports 1 to 1023 are well-known ports used as defaults for web protocols, outlined by the Web Assigned Numbers Authority (IANA).
- Ports 1024 to 49151 are registered with IANA for particular purposes and companies.
- Ports 49152 to 65535, referred to as ephemeral, dynamic or personal ports, are used for momentary connections on an as-needed foundation.
A port scan is a community discovery approach that entails sending a sequence of messages, referred to as probes, to a tool. Port scanners, comparable to Nmap, are purposes that conduct port scans to determine which ports are open or closed.
Nmap port scan use circumstances
One in all Nmap’s most useful and broadly used capabilities is scanning for particular port info. Frequent Nmap port scan use circumstances embrace the next:
- Discovering and fixing potential vulnerabilities.
- Testing firewall guidelines.
- Safety auditing.
- Inventorying community units.
- Discovering new units on a community.
- Troubleshooting connectivity points.
- Mapping community topology.
- Figuring out community bottlenecks.
- Penetration testing.
- Performing incident response.
- Closing unused ports, i.e., making certain the server solely listens for site visitors for the companies it presents.
- Scanning cloud infrastructure, together with VMs, cloud companies and digital networks.
Word that malicious hackers additionally conduct port scans for community reconnaissance. Utilizing a port scanner, they will discern which companies a tool runs and determine vulnerabilities to use to provoke an assault.
Port standing classes
Nmap port scans return one of many following states per port checked:
- Open. Signifies a service actively listens and runs on this port and accepts connections.
- Closed. Signifies that whereas probes are acquired and the port is reachable, no companies at the moment run on the port.
- Filtered. Nmap acquired no indication that the probes have been acquired and can’t decide the port’s standing. That is typically as a consequence of packet filtering by a firewall.
- Unfiltered. Denotes probes have been acquired, however Nmap can’t decide the state.
- Open/Filtered. The port is open or filtered, however Nmap can’t decide the state.
- Closed/Filtered. The port is closed or filtered, however Nmap can’t decide the state.
obtain and set up Nmap
Start by downloading the suitable set up utility from the official Nmap web site.
- Linux customers: Set up Nmap utilizing the Pink Hat Bundle Supervisor linked within the description.
- Mac customers: Entry the binaries utilizing a disk picture file. You too can set up Nmap via the Homebrew bundle supervisor by typing $ brew set up nmap.
- Home windows directors: Obtain the installer software.
You too can compile Nmap your self should you want particular modifications or settings. To make use of a graphical model of Nmap fairly than work solely on the command line, obtain and set up the Zenmap entrance finish.
The Nmap web site consists of intensive documentation and a script repository containing many helpful and complicated configurations for any kind of scan.
Nmap port scans: Frequent ports and strategies
Frequent port and repair examples utilized in Nmap scans embrace the next:
- TCP port 22. Safe Shell, generally used to securely hook up with distant Linux, macOS and community units.
- TCP ports 80 and 443. HTTP and HTTPS, used for inner internet companies.
- TCP port 123. Community Time Protocol, used to synchronize time companies on community nodes.
- TCP port 3389. Distant Desktop Protocol, generally used for safe distant administration of Home windows techniques.
- TCP port 1433. Microsoft SQL Server database engine, frequent for MS SQL databases.
- TCP port 389. Light-weight Listing Entry Protocol, frequent for Microsoft Energetic Listing environments.
- TCP port 445. Server Message Block (SMB), used for contemporary Home windows file sharing.
- UDP ports 135, 137 and 138 and TCP port 139. Older SMB Home windows file sharing protocols.
Networks can have different ports open on some units for customized or third-party apps, so examine your documentation rigorously. Strive testing these ports in your group’s community, or scan scanme.nmap.org, a bunch arrange by the Nmap Safety Scanner Challenge for testing functions.
Frequent Nmap port scan varieties and strategies embrace the next:
- TCP SYN scans. Often known as TCP half-open scanning, these scans ship SYN (synchronization) packets however by no means full the TCP handshake.
- UDP scans. These ship UDP packets to focus on ports and decide port state.
- TCP join scans. These full a full TCP three-way handshake with goal ports, making it extra detectable, but additionally extra dependable.
- SCTP INIT scans. Like TCP SYN scans however for Stream Management Transmission Protocol, these ship INIT (initiation) chunks to find companies on SCTP-enabled techniques, for instance, VoIP and telecom networks.
- Null scans. Ship TCP packets with no flags set, which may bypass firewall guidelines and will reveal closed ports in the event that they reply with RST (reset) packets.
- FIN scans. Transmit packets with solely the FIN (end) flag set. FIN signifies the connection has been terminated, after which a closed port normally responds with an RST, whereas open and filtered ports do not reply.
- Xmas scans. These set the FIN, PSH (push) and URG (pressing) flags — lighting up the packet like a Christmas tree — to set off responses from closed ports.
- TCP ACK scans. Ship TCP packets with solely the ACK (acknowledgement) sign, which lets a sender know a packet has been acquired. Primarily used to map firewall guidelines and packet filtering settings.
- IP scans. Somewhat than scanning for ports, these scans decide which IP protocols are supported by the goal system.
- FTP bounce scans. Use an FTP server to scan for ports. Most fashionable FTP servers block this vulnerability.
conduct Nmap port scans, step-by-step
As you learn to use Nmap, you may discover the utility depends on many choices to handle precisely the way it scans targets. The first choice for port scanning is -p, adopted by a number of port numbers. Open a terminal window and use the next instructions to conduct numerous varieties of scans.
run a default scan
To run a default scan, use the next command with a specified goal, comparable to an IP tackle or host identify:
It will carry out a scan — both a TCP SYN scan for privileged customers or a TCP Join scan for unprivileged customers — of the commonest 1,000 TCP ports. Scan outcomes present goal info, together with IPv4 and IPv6 addresses, reverse DNS identify, ports and port states.
scan a selected, single port
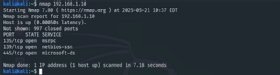
Kind the next command to scan a single port, such because the older Home windows file sharing port 135:
nmap -p 135 192.168.1.10
Substitute the goal’s hostname if identify decision is on the market. You too can goal internet URLs.
scan all ports
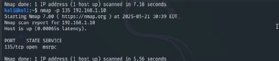
To scan all ports — 1 via 65,535, use the -p- command:
nmap -p- 135 192.168.1.10
This scans all ports, fairly than simply the highest 1,000 ports throughout a default scan.
scan a number of ports manually
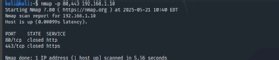
You would possibly wish to scan a number of ports concurrently, particularly ports associated to one another, comparable to internet companies or older SMB connections.
nmap -p 80,443 192.168.1.10
nmap -p 137,138,139 192.168.1.10
This strategy offers a neater and extra complete scan if you recognize precisely which ports you want outcomes for.
scan a spread of ports
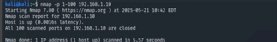
You too can inform Nmap to scan for a spread of ports, comparable to 1 to 100.
nmap -p 1-100 192.168.1.10
scan a number of ports robotically
Nmap meshes simply with automation and environment friendly processes. For instance, it could possibly scan ports you probably have to view. Start through the use of the -F choice for a quick scan of the 100 mostly used ports.
nmap -F 192.168.1.10
Word that Nmap’s default scan checks the 1,000 mostly used ports — which considerably will increase the time required for intensive community scans.
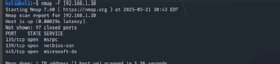
scan for the highest ports
Use the –top-ports choice if you wish to discover the scan to search for a selected variety of the highest ports. For instance, kind the next to scan the 20 mostly used ports:
nmap –top-ports 20 192.168.1.10
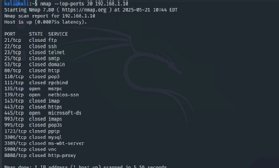
exclude ports from a scan
You’ll be able to script Nmap scans, which is especially helpful should you search for particular ports repeatedly. Scripting lends itself to extraordinarily particular instructions and choices. Nmap’s –-exclude-ports flag lets you forestall it from scanning specific ports. For instance, you would possibly generate a script to scan the 100 commonest ports utilizing the -F choice but additionally exclude internet companies ports you are already conscious of.
nmap -F –exclude-ports 80,443 192.168.1.10
Organising exclusions makes for extra environment friendly scans. The examples on this part goal a single machine, however the precision that exclusions enable can even profit network-wide scans of total subnets.
Scanning is a necessary a part of auditing
Scanning ports with Nmap is crucial for community auditing, service administration and hardening. The prevalence of infrastructure-as-code automation, orchestrated deployments, and scaling and virtualized units means you will not at all times know precisely what’s deployed in your setting. Scanning is a wonderful means to make sure you’re conscious of all entry factors.
Common Nmap scans assist guarantee a community’s performance and safety. Studying how you can use Nmap offers admins the talents and peace of thoughts mandatory for community and server hardening. It is also important for mapping a community, troubleshooting and making ready for an audit.
Obtain Nmap in your favourite OS at the moment and start studying the way it can enhance your organization’s safety posture and empower your help workforce.
Editor’s observe: It’s attainable to make use of Nmap each lawfully and unlawfully. It’s as much as you to make sure your utilization is lawful. Get acceptable permission and approval earlier than performing port scans, and deal with the data obtained ethically. If you’re uncertain whether or not your utilization is lawful, don’t proceed till you’ve got confirmed that it’s — for instance, by discussing and validating your deliberate utilization together with your group’s counsel.
Damon Garn owns Cogspinner Coaction and offers freelance IT writing and modifying companies. He has written a number of CompTIA examine guides, together with the Linux+, Cloud Necessities+ and Server+ guides, and contributes extensively to Informa TechTarget, The New Stack and CompTIA Blogs.










