In my years writing about cybersecurity, I’ve realized one common fact: nobody wakes up enthusiastic about identification and entry administration (IAM), however everybody regrets ignoring it.
Between staff reusing weak passwords, phishing makes an attempt focusing on credentials, and the rising net of SaaS purposes, retaining accounts safe with out irritating customers is less complicated stated than carried out.
Throw in distant work, third-party integrations, and compliance audits into the combo, and it’s no shock that IAM appears like an infinite sport of catch-up. The problem isn’t nearly safety — it’s about discovering the appropriate IAM software that truly works with out including complexity to each day operations.
Should you’re a safety chief, IT supervisor, or enterprise decision-maker, discovering the greatest identification and entry administration software program in your group can really feel overwhelming. With so many choices promising hermetic safety and seamless integration, how are you aware which one actually delivers?
I’ve carried out all this analysis, so that you don’t need to. I spoke with IAM consultants, reviewed G2 stories, and gathered insights from my very own IT and safety crew (who’ve seen sufficient dangerous IAM setups to final a lifetime). After evaluating 15 main IAM options, I’ve narrowed it right down to the highest 5 that truly stand out for safety, scalability, and usefulness.
5 greatest identification and entry administration software program: My High Picks
- Microsoft Entra ID: Finest for organizations already within the Microsoft ecosystem
Seamless integration with Azure, Workplace 365, and Intune, with sturdy conditional entry insurance policies. ($6/person/month) - JumpCloud: Finest for multi-OS identification administration with built-in MDM Unified platform combining IAM, MDM, and listing companies for Home windows, macOS, Linux, iOS, and Android. ($9/person/month)
- Okta: Finest for enterprise-grade authentication and SaaS integrations
Versatile SSO and adaptive MFA that integrates with hundreds of apps throughout multi-cloud environments. ($2/person/month for SSO) - Salesforce Platform: Finest for companies operating on Salesforce
Constructed-in SSO, MFA, and buyer identification options with customizable entry insurance policies inside Salesforce. ($5/person/month) - Cisco Duo: Finest for easy, safe MFA and SSO
Straightforward-to-use authentication with Duo Push, adaptive insurance policies, and a free plan for small groups. ($3/person/month)
*These are the top-rated merchandise within the IAM software program class, in keeping with G2’s Winter 2025 Grid® Report. I’ve talked about the beginning value of their paid plans for simple comparability.
Whether or not you’re upgrading your IAM technique or wanting to decide on the main identification and entry administration platform for the primary time, this information will enable you discover the very best match in your group.
5 greatest identification and entry administration software program I like to recommend
With out IAM, managing person entry is like handing out keys to an workplace and dropping monitor of who has them or the place they’re getting used. It’s what retains that chaos in examine.
IAM protects entry, whereas operational threat administration software program helps tackle the dangers tied to these identities throughout the enterprise. It controls who will get entry to what, when, and the way securely, so IT groups can implement safety insurance policies, stop unauthorized entry, and cut back threat with out turning each login try right into a help ticket.
I’ve researched my fair proportion of IAM software program in all styles and sizes, from cloud-focused ones to on-premises options and from extremely customizable methods for giant enterprises to easy choices for rising groups.
From my analysis and conversations with IAM consultants, I’ve realized that the very best IAM software program isn’t nearly safety. It is in regards to the steadiness between safe person authentication, granular entry controls for imposing the least privilege, and clean integration with current methods.
And the stakes are solely getting greater. The worldwide IAM market is projected to succeed in $41.52 billion by 2030 from $15.93 billion in 2022.
How did I discover and consider the very best IAM software program?
Discovering the very best IAM software program isn’t nearly evaluating function lists or vendor guarantees — safety leaders want options that truly work in the true world. I began by analyzing G2 Grid stories, which rank IAM instruments primarily based on real-world adoption, person satisfaction, and enterprise match. This gave me a transparent view of which platforms dominate the house and the way they carry out in areas like authentication, entry management, and compliance.
To transcend rankings, I used AI to investigate a whole lot of person opinions of those merchandise. This helped me establish recurring themes — whether or not it was frustration over clunky authentication flows, reward for adaptive entry insurance policies, or considerations about integration with current safety stacks.
Given I couldn’t enroll and entry the software myself, I additionally spoke with IAM consultants, my very own IT and safety crew members, and professionals who take care of identification safety each day and use these instruments and validated their feedback with verified G2 opinions. Their suggestions helped me lower by means of the noise and give attention to options that ship sturdy safety with out turning into a bottleneck for IT operations.
The screenshots featured on this article could also be a mixture of these captured throughout testing and ones obtained from the seller’s G2 web page.
Do you know? On common, companies report ROI on IAM investments in 14 months, in keeping with G2 Information.
What makes the very best identification and entry administration software program: My standards
Based mostly on every thing I’ve realized, right here’s the guidelines I used to guage the highest IAM resolution:
- Robust authentication with out friction: Authentication must be strong, but it surely shouldn’t create pointless complications. If logging in appears like a chore, customers will take shortcuts — reusing passwords, writing them down, or bypassing safety altogether. I appeared for IAM options that provide multi-factor authentication (MFA) past the fundamentals, with choices like biometric verification, passwordless login, and adaptive authentication that adjusts safety necessities primarily based on threat. Single sign-on (SSO) was one other huge issue because it reduces login fatigue whereas sustaining safety. Danger-based authentication additionally stood out — options that analyze conduct, location, and gadget to set off further safety when wanted scored greater on my record.
- Granular entry controls and role-based administration: It’s not nearly who can log in — it’s about what they will entry as soon as inside. IAM options that provide sturdy role-based entry management (RBAC) made the lower, permitting IT groups to handle permissions at scale with out manually adjusting each person’s entry. I additionally checked out instruments with attribute-based entry management (ABAC), which considers context like gadget kind, location, and login conduct to make smarter entry choices. Simply-in-time entry was one other function that stood out, limiting high-privilege entry solely when it’s completely essential, decreasing long-term publicity to delicate methods.
- Integration with current safety infrastructure: An IAM system isn’t helpful if it doesn’t match into the broader safety ecosystem. I prioritized options that combine easily with identification suppliers like Energetic Listing and Azure AD, in addition to SIEM platforms for real-time authentication monitoring. IAM also needs to join with HR and ITSM methods for automated provisioning and de-provisioning of accounts — as a result of guide account administration is a recipe for errors and safety gaps.
- Compliance and audit-readiness: For organizations coping with strict rules, IAM isn’t only a safety software — it’s a compliance requirement. I targeted on options that provide built-in audit logs, detailed compliance reporting, and governance options like entry opinions and certification workflows. Assembly trade requirements like SOC 2, ISO 27001, HIPAA, and GDPR was one other main issue. Safety leaders want IAM instruments that don’t simply assist them safe identities but in addition make compliance audits much less of a nightmare.
- Scalability and adaptability for rising organizations: A very good IAM resolution ought to develop with the enterprise, not maintain it again. I evaluated how nicely these instruments help hybrid IT environments and whether or not they supply multi-tenant help for enterprises managing a number of subsidiaries or divisions. API-driven customization was one other key issue — organizations want IAM methods that enable them to automate workflows and combine with different safety instruments as a substitute of forcing a inflexible, one-size-fits-all strategy.
- Person expertise: IAM safety solely works if individuals really use it. I appeared for IAM options that provide clear, intuitive admin dashboards that IT groups can navigate with out in depth coaching. Self-service password reset was one other main issue — IT groups don’t have time to consistently unlock accounts simply because somebody forgot a password. The very best options cut back friction whereas nonetheless imposing sturdy safety insurance policies.
After checking every software towards this guidelines and cross-referencing it with skilled insights, real-world suggestions, and AI-driven overview evaluation, I recognized the highest 5 IAM options.
Whether or not you are on the lookout for the very best identification administration software with multi-factor authentication, or the very best IAM software program for securing distant workforces, there is a software under.
The record under comprises real person opinions from the IAM software program class. To be included on this class, an answer should:
- Provision and de-provision of person identities.
- Assign entry primarily based on particular person position, group membership, and different components.
- Implement person entry rights primarily based on permissions.
- Confirm person identification with authentication, which can embrace multi-factor authentication strategies.
- Combine with directories that home worker knowledge.
*This knowledge was pulled from G2 in 2025. Some opinions could have been edited for readability.
1. Microsoft Entra ID: Finest for organizations already within the Microsoft ecosystem
From what I’ve seen in G2 opinions, Microsoft Entra ID (previously Azure Energetic Listing) is commonly highlighted as one of many main identification and entry administration platforms, largely attributable to its deep integration into the Microsoft ecosystem. Many customers recognize how seamlessly it really works with different Microsoft companies like Azure, Dynamics 365, Intune, and Energy Platform.
I’ve seen that G2 customers ceaselessly point out how Entra ID comes included at no further value if your organization is already utilizing Microsoft companies. This built-in help for MFA, limitless SSO throughout SaaS apps, primary reporting, and self-service password modifications is a serious benefit, notably for companies which can be already built-in into the Microsoft atmosphere.
From my analysis, I’ve discovered that Entra ID’s sturdy authentication and safety controls stand out to many IT professionals. The power to implement versatile conditional entry insurance policies, particularly when paired with Intune for endpoint administration, is commonly praised as a complete resolution for unified entry management.
I’ve seen a number of G2 customers specific their appreciation for conditional entry, which permits IT groups to tailor safety insurance policies primarily based on person conduct, location, and threat ranges. This performance is particularly valued as a result of it helps steadiness safety with usability, prompting MFA for unrecognized gadgets whereas permitting trusted gadgets to entry sources with minimal friction.
One function that customers ceaselessly name out is Entra Join, which permits seamless integration of on-premises Energetic Listing with Entra ID. I’ve learn a number of opinions from organizations transitioning to the cloud who discover this notably useful for simplifying entry administration throughout each cloud and on-premises infrastructures.

That being stated, setup and configuration are frequent ache factors I famous amongst G2 reviewers, particularly for companies with blended IT environments. A number of reviewers be aware the time and complexity required to get every thing operating easily, notably when migrating from non-Microsoft setups.
Licensing prices was one other recurring theme in G2 suggestions I noticed. Whereas Entra ID provides a free tier, customers usually point out that the extra superior security measures, akin to these below identification safety, governance, and privileged entry administration, are solely obtainable in higher-tier licenses like Entra ID P2.
From my evaluation, small companies usually wrestle with the price of premium licensing regardless of needing superior options. Many G2 customers have shared that determining which Entra ID tier most closely fits their wants could be tough when balancing safety and compliance necessities.
General, regardless of the challenges, I’ve seen a basic consensus that Microsoft Entra ID is a stable IAM resolution. For giant organizations deep in Microsoft, it’s usually the reply to “which identification entry app is greatest for enterprises?”
What I like about Microsoft Entra ID:
- I’ve seen G2 customers reward how Entra ID integrates seamlessly with Azure, Workplace 365, and different Microsoft companies, making SSO and conditional entry clean and easy.
- I’ve additionally seen that hybrid identification administration with Entra Join is a standout function, particularly for companies nonetheless sustaining on-premises infrastructure, simplifying the sync between on-prem Energetic Listing and the cloud.
What G2 customers like about Microsoft Entra ID:
“Microsoft Entra is without doubt one of the greatest options Microsoft provides for verifying and figuring out enterprise know-how property akin to laptops and cellphones. It ensures that solely the appropriate individuals have entry to particular sources.
What I like essentially the most are these three options: multi-factor authentication with the Microsoft Authenticator app, identification administration for every gadget, and its integration with BitLocker, which supplies full disk encryption for the asset. This fashion, knowledge is securely saved and could be recovered with a BitLocker restoration key.”
– Microsoft Entra ID Overview, Erick Vincent Steve G.
What I dislike about Microsoft Entra ID:
- From what I noticed, establishing Entra ID isn’t precisely a clean experience. G2 customers who aren’t in Microsoft’s ecosystem took some further effort and time to get every thing configured correctly.
- Based mostly on my analysis, licensing value is one other ache level. G2 customers report that the free tier covers the fundamentals, however a number of the options that safety groups really need are locked behind Entra ID P2, which isn’t low cost.
What G2 customers dislike about Microsoft Entra ID:
“Customers unfamiliar with Microsoft merchandise will face difficulties in understanding the combination of this product, and the identical goes for firms utilizing non-Microsoft platforms. The price of implementing Microsoft Entra ID might be a priority for low-budget firms together with this, the businesses that pose challenges in environments with unstable web entry can face issues as a result of Entra ID is cloud-based.”
– Microsoft Entra ID Overview, Sahil C.
2. JumpCloud: Finest for multi-OS identification administration with built-in MDM
From what I’ve seen in G2 opinions, JumpCloud is commonly praised for being a versatile, cloud-first IAM resolution designed for organizations shifting away from conventional on-prem identification administration.
Many customers recognize its skill to handle identities throughout a number of platforms, together with Home windows, Android, iOS, macOS, and Linux, all from a single platform. This open listing strategy permits it to combine seamlessly not solely with Azure or Energetic Listing but in addition with Google Workspace, AWS, and different third-party SaaS apps, making it an interesting selection for multi-cloud and hybrid setups.
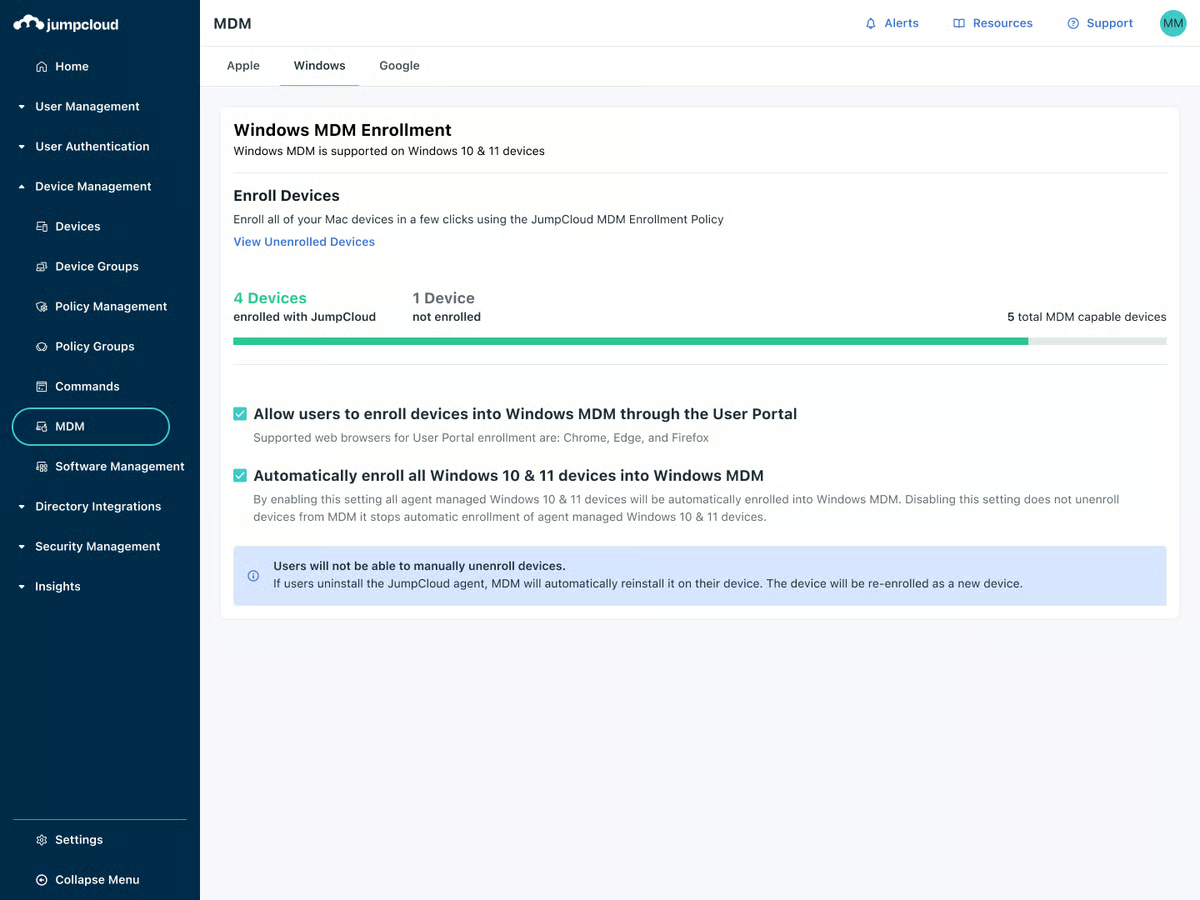
I’ve seen that G2 customers spotlight JumpCloud’s all-in-one platform, which mixes IAM, cell gadget administration (MDM), listing companies, and endpoint safety. This integration makes managing customers, gadgets, and safety insurance policies from a single platform notably enticing to IT groups juggling a number of working methods. Many customers report vital time financial savings and streamlined operations due to this unified strategy.
From a usability standpoint, I’ve seen a number of opinions commending JumpCloud for its clear and user-friendly interface. Customers discover the onboarding course of easy, and the flexibility to simply deploy SSO and MFA throughout the group is extremely valued.
One function that’s ceaselessly talked about in G2 suggestions is JumpCloud’s in depth data base, which incorporates step-by-step tutorials and movies. Many customers recognize this useful resource for making setup and implementation simpler. Moreover, JumpCloud’s buyer help receives optimistic opinions for being dependable and responsive when points come up.
Nonetheless, some G2 customers do level out sure lacking options. For example, the dearth of self-service for account unlocks implies that IT groups should manually help customers who’re locked out, which may turn into cumbersome. Distant help is one other space the place some customers be aware points, because it’s seen as considerably clunky and in want of enchancment.
I’ve additionally seen a number of G2 opinions point out that JumpCloud’s MDM capabilities, whereas helpful, could not present the identical degree of granular management and automation present in different MDM options, particularly in Apple-heavy environments. Customers managing giant fleets of gadgets, notably Apple gadgets, usually really feel that JumpCloud doesn’t fairly match as much as specialised MDM options like Jamf.
Regardless of these drawbacks, I imagine JumpCloud’s important energy is its unified strategy to IAM, listing companies, and MDM.
It provides an all-in-one resolution that works nicely for small and medium companies, regardless that it’d come at the next value level than standalone enterprise-grade IAM or MDM options. That’s why I take into account JumpCloud among the finest IAM options for mid-sized tech firms juggling a number of platforms. For organizations on the lookout for an built-in platform, JumpCloud stays a stable possibility.
What I like about JumpCloud:
- From what I’ve seen in G2 opinions, JumpCloud provides flexibility by managing identities throughout Home windows, macOS, Linux, Android, and iOS from one platform, not like Microsoft Entra ID, which is extra optimized for Microsoft environments.
- I’ve seen that JumpCloud combines IAM, cell gadget administration (MDM), listing companies, and endpoint safety, which simplifies IT administration throughout totally different working methods.
What G2 customers like about JumpCloud:
“JumpCloud could be very straightforward to make use of and user-friendly. It helped us handle our staff’ methods. We are able to now handle software program utility installations on these methods through a function in JumpCloud, Software program Administration, which is sort of useful.
Additionally, it is extremely straightforward to use any insurance policies through JumpCloud to end-user methods, akin to password coverage, MFA for logging into the system, and so on. Additionally, listing integration could be very straightforward to arrange, akin to AD, Cloud, or HR directories. With this, we will additionally run instructions on distant methods and take distant help/management of the system, which could be very helpful. And the client help is all the time there for you, and they’re fairly quick in responding.”
– Jumpcloud Overview, Saurabh R.
What I dislike about JumpCloud:
- I’ve discovered that self-service account unlocks are lacking, that means IT should step in each time a person is locked out, which different IAM options usually enable customers to deal with on their very own.
- I’ve additionally learn that distant help feels clunky, and MDM, whereas practical, doesn’t present the identical granular management and automation as instruments like Jamf, particularly for Apple-heavy environments.
What G2 customers dislike about JumpCloud:
“Jumpcloud has but to develop superior options like self-service for Account unlocks, Person orchestration, and governance capabilities, that are essential on this period of enterprise safety administration.“
– Jumpcloud Overview, Gangadhara S.
Controlling who accesses your methods is one a part of the puzzle. Managing the gadgets they use is the following. Discover the greatest Cell Gadget Administration (MDM) options I belief to maintain each endpoint safe, up to date, and compliant.
3. Okta: Finest for enterprise-grade authentication and SaaS integrations
Okta is without doubt one of the most versatile and scalable IAM options, particularly for organizations requiring sturdy safety and superior authentication. Like JumpCloud, it’s vendor-neutral and works nicely in multi-cloud environments and with advanced SaaS integrations.
I’ve seen that Okta integrates seamlessly with instruments like Microsoft, Google Workspace, and AWS, making SSO, adaptive authentication, and automatic person provisioning easy throughout a variety of purposes.
From a person expertise standpoint, I’ve discovered Okta’s interface intuitive for each IT groups and finish customers. It’s ceaselessly praised for providing one of many smoothest SSO experiences.
I additionally worth that Okta helps third-party MFA and token suppliers and its personal built-in MFA, giving firms the pliability to combine no matter works greatest for them. The customizable SSO portal is one other function that stands out for simplifying app administration.
On the subject of dealing with scale, Okta is commonly seen as the highest identification administration service for startups aiming to develop quick with out safety bottlenecks.

Nonetheless, from what I’ve learn on G2, pricing is usually a barrier for smaller companies and startups, as Okta provides a la carte pricing, which may add up rapidly when a number of companies are wanted.
I’ve come throughout opinions the place customers talked about that establishing Okta could be difficult. Configuring insurance policies, settings, and integrations takes effort and time, which was overwhelming for some G2 reviewers. Whereas Okta supplies good documentation and help, fine-tuning every thing for optimum safety and automation nonetheless requires a substantial funding of time.
What I like about Okta:
- I worth how Okta integrates seamlessly with Microsoft, Google Workspace, AWS, and SaaS apps, making SSO, adaptive authentication, and person provisioning easy.
- I additionally like the pliability to customise SSO insurance policies and blend them with MFA choices like Okta Confirm, Symantec VIP, Duo Safety, and Google Authenticator, balancing safety and usefulness.
What G2 customers like about Okta:
“Through the years, I’ve labored with Okta throughout varied firms, and I have to say that it’s actually among the finest SSO options in the marketplace. Not solely is it user-friendly with a contemporary interface, but it surely additionally boasts high-security requirements and helps working with hundreds of customers concurrently.”
– Okta Overview, Paloma G.
What I dislike about Okta:
- From what I noticed, the setup isn’t precisely fast. Okta is highly effective, however getting every thing configured takes time. Many G2 reviewers reported that there are a variety of settings to fine-tune, and the educational curve was steep.
- G2 reviewers point out the pricing as a draw back. For my part, it will also be a problem for smaller companies. With a minimal $1,500 annual contract, it could actually really feel out of attain for startups or small IT groups that solely want just a few core options.
What G2 customers dislike about Okta:
“Okta is dear and unsuitable for smaller companies. Pricing plans are a la carte and complicated. Configuring directories and person synchronization will take a variety of time and effort.”
– Okta Overview, Qual A.
4. Salesforce Platform: Finest for companies operating on Salesforce
Amongst CRM-heavy groups, Salesforce is a number one identification and entry administration platform with built-in SSO and MFA. G2 customers usually spotlight as a robust IAM resolution, particularly for companies already operating on the Salesforce Platform. Single Signal-On (SSO) and Multi-Issue Authentication (MFA) are two key options ceaselessly talked about, with reviewers noting that these are important elements of the answer.
I’ve seen that many G2 customers recognize Salesforce’s App Launcher. This allows customers to entry a variety of enterprise purposes — Salesforce apps in addition to third-party apps — while not having to log in individually. Even when utilizing Energetic Listing for person administration, customers can depend on Id Connect with handle Salesforce accounts, which is seen as a big profit for usability and safety.
I’ve encountered noticeable satisfaction concerning Salesforce’s degree of management over knowledge access. A number of reviewers point out how linked apps and OAuth allow fine-grained entry controls, permitting firms to limit entry to delicate data. This is especially useful for groups managing buyer accounts and delicate knowledge.
From what I’ve learn, many G2 customers discover the Buyer Id function to be a robust addition, particularly for giant companies that want to trace buyer exercise throughout a number of channels. Reviewers be aware that the flexibility for patrons to self-register, securely log in, and entry apps with a single identification is a standout function. The truth that it’s absolutely customizable to suit firm branding and workflows additionally helps companies streamline their processes.

Nonetheless, I’ve seen some customers be aware the complexity of the setup course of. G2 reviewers ceaselessly point out that configuring Salesforce Id could be time-consuming because of the giant variety of configurations, permissions, and integrations that should be adjusted. This makes onboarding extra sophisticated in comparison with devoted IAM options like Okta or JumpCloud.
I’ve seen that some G2 customers report the platform could be barely sluggish at occasions, particularly when coping with giant datasets or advanced workflows. Whereas this isn’t seen as a dealbreaker, some reviewers have raised it, notably concerning response occasions.
Lastly, I’ve learn a number of reviewers point out pricing as a consideration. Whereas Salesforce Id is commonly seen as a very good match for bigger enterprises already throughout the Salesforce ecosystem, G2 customers level out that it will not be as budget-friendly for small to mid-sized firms.
Based mostly on my evaluation of G2 opinions, Salesforce Id looks as if a stable possibility for companies already closely invested in Salesforce, notably these utilizing its CRM software program in Skilled, Enterprise, Limitless, or Efficiency Editions.
What I like about Salesforce Platform:
- I’ve seen that G2 customers discover Salesforce Id to be a pure extension of the Salesforce ecosystem, making it simpler to handle SSO, MFA, and person permissions inside one platform.
- I’ve seen that many reviewers recognize the Buyer Id (CIAM) function, permitting clients and companions to self-register and log in utilizing social sign-ins like Fb or LinkedIn.
What G2 customers like about Salesforce Platform:
“Salesforce is cloud-based and provides enterprise-grade scalability. Whether or not you are connecting to exterior methods through APIs, utilizing Salesforce Join for exterior knowledge sources, or leveraging pre-built connectors for in style instruments.
What I like greatest about Salesforce is its flexibility and energy in enabling companies to construct customized purposes with out requiring a variety of advanced coding. Additionally, buyer help is nice and really useful. I exploit Salesforce each day in my work. It’s straightforward to make use of, combine, and implement.“
– Salesforce Platform Overview, Rushabh U.
What I dislike about Salesforce Platform:
- From what I’ve learn, configuring Salesforce Id could be time-consuming. G2 customers point out that there are lots of settings and integrations to handle, making onboarding extra advanced.
- I’ve come throughout suggestions that processes could be sluggish, particularly with giant datasets or advanced workflows. Whereas not a serious challenge, slower response occasions can concern some customers.
What G2 customers like about Salesforce Platform:
“As a person, what I do not like about Salesforce is that it is extremely costly, particularly for small companies and startups. As a developer, when you find yourself coping with giant quantities of information, the stories and dashboard can run slowly, and typically, the governor restrict can limit the advanced operation.”
– Salesforce Platform Overview, Dhruv G.
IAM controls who will get entry, whereas community monitoring instruments assist monitor what occurs inside your methods. Right here’s my analysis of the very best choices.
5. Cisco Duo: Finest for easy, safe MFA and SSO
I’ve seen that G2 customers usually reward Cisco Duo for its easy strategy to safety. Many reviewers spotlight its simplicity and effectiveness, particularly concerning MFA, SSO, and adaptive authentication.
Not like some IAM instruments that really feel overloaded with pointless options, Duo stands out for retaining issues targeted and straightforward to handle, which is a constant theme in person suggestions.
From what I’ve seen, destructive suggestions tends to give attention to the educational curve of different IAM platforms. A number of customers have expressed that Duo is far simpler to make use of than different IAM instruments, which regularly have steep studying curves. Duo’s ease of use is ceaselessly talked about, with customers appreciating its easy interface and its flexibility by way of integration with varied purposes and platforms.
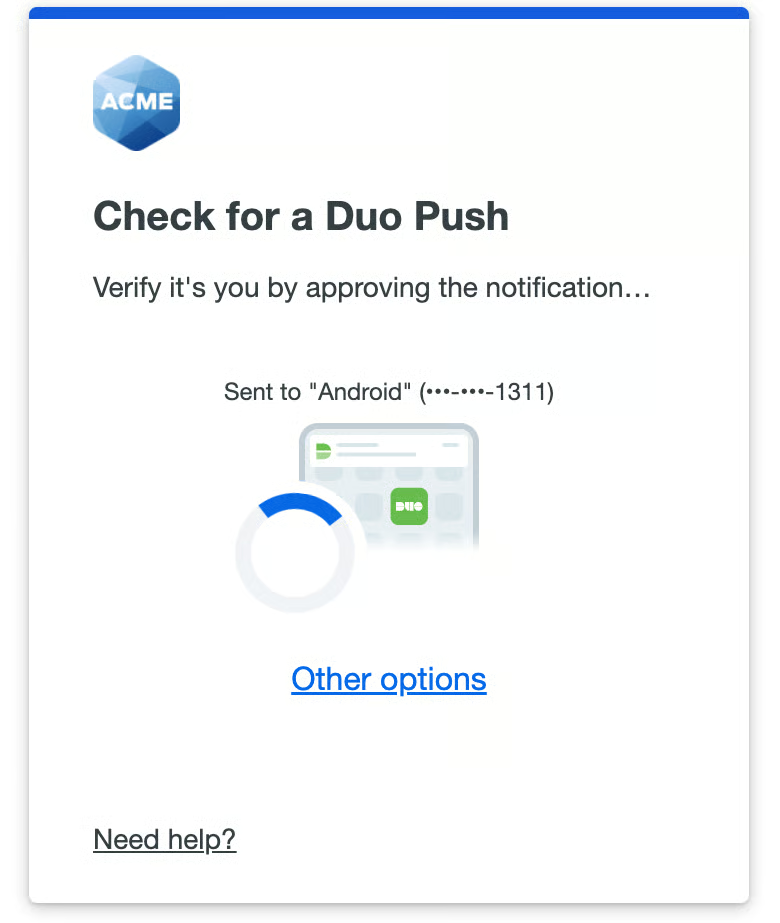
I’ve come throughout suggestions on G2 round Duo’s offline entry. Many customers have identified that its offline performance is restricted, which could be an inconvenience in sure eventualities. Whereas Duo provides sturdy core options, some customers really feel this facet might be improved for higher flexibility in offline environments.
I’ve learn a number of reviewers point out struggles with the person interface and design. Whereas the system is practical, many G2 customers imagine the UI might be extra intuitive and trendy. This suggestions means that whereas Duo is efficient, its design might be a barrier for customers who worth a extra streamlined, user-friendly expertise.
Regardless of these challenges, many G2 customers discover Duo to be a stable selection for organizations searching for dependable MFA and SSO options.
For small IT groups, Duo usually emerges as the very best IAM software program for small companies due to its free tier and straightforward deployment. Customers recognize the chance to check Duo’s options with as much as 10 customers for gratis, giving smaller groups or startups an inexpensive choice to implement safe entry controls.
What I like about Cisco Duo:
- I’ve seen that G2 customers recognize how Duo retains issues easy — deploying MFA and SSO with out pointless complexity, not like another IAM instruments.
- I’ve learn a number of reviewers point out how a lot they take pleasure in Duo Passport, which remembers gadget classes throughout apps, making entry smoother whereas sustaining tight safety.
What G2 customers like about Cisco Duo:
“It was easy to arrange, and authentication is nearly speedy when connecting to my firm’s VPN. I favor the push notification approval strategy, because it solely requires me to faucet a button on my cellphone. It combines with many different out-of-the-box options, and it provides cloud-based, AD-integrated SAML SSO and digital equipment options to guard even bespoke interfaces.
We utilized Duo to guard our VMware Horizon desktop atmosphere; setup and deployment have been easy, and I like how easy it’s to attach with Energetic Listing. Even higher, finish person onboarding was easy, and finish customers discovered the system easy to make use of, which is an important profit.”
– Cisco Duo Overview, Connie B.
What I dislike about Cisco Duo:
- Based mostly on my examine of G2 opinions, offline authentication in Duo is restricted, which is usually a downside for customers in low-connectivity areas or frequent vacationers.
- I’ve seen that the UI feels outdated, and plenty of G2 customers counsel a refresh to make it extra trendy and intuitive, particularly for IT groups dealing with giant deployments.
What G2 customers dislike about Cisco Duo:
“The setup of on-line and offline could be complicated for finish customers. Additionally, if time desyncs, it turns into an enormous downside.”
– Cisco Duo Overview, Jonathan M.
Discover the greatest password managers which can be designed to securely retailer, generate, and autofill passwords whereas defending person accounts.
Now, there are just a few extra choices, as talked about under, that did not make it to this record however are nonetheless price contemplating, in my view:
- AWS Verified Entry: Finest for securing AWS environments with Zero Belief entry controls.
- Google Cloud Id: Finest for organizations deep within the Google ecosystem needing seamless IAM.
- Oracle Id Cloud Service: Finest for hybrid cloud IAM with sturdy enterprise integrations.
- Rippling: Finest for combining IAM with HR and payroll administration in a single platform.
- IBM Confirm: Finest for AI-driven identification safety and superior risk detection.
- SailPoint: Finest for enterprise-level identification governance and compliance administration.
Continuously requested questions (FAQ) on IAM software program
1. Why is IAM vital for companies?
IAM enhances safety, reduces the danger of information breaches, streamlines person entry, and ensures compliance with trade rules (e.g., GDPR, HIPAA, SOC 2). It additionally improves productiveness by automating person provisioning and entry administration.
2. What options ought to I search for in IAM software program?
Key IAM options embrace:
- Single sign-on (SSO): Permits customers to log in as soon as and entry a number of purposes.
- Multi-factor authentication (MFA): Provides an additional layer of safety past passwords.
- Person provisioning and de-provisioning: Automates account creation and elimination.
- Function-based entry management (RBAC): Assigns permissions primarily based on job roles.
- Audit and compliance reporting: Helps monitor entry logs for safety and regulatory functions.
- Id federation: Helps cross-domain authentication.
3. What’s the distinction between IAM and PAM (Privileged Entry Administration)?
IAM focuses on managing entry for all customers in a company. PAM is particularly designed to safe entry for privileged accounts with elevated permissions, akin to system directors.
4. Is IAM software program cloud-based or on-premises?
IAM options could be:
- Cloud-based: Hosted by a supplier, scalable, and excellent for contemporary SaaS purposes.
- On-premises: Put in inside an organization’s infrastructure, providing extra management over safety insurance policies.
- Hybrid: Combines each fashions for flexibility.
5. Can IAM software program assist with Zero Belief safety?
Sure, IAM is a crucial part of Zero Belief by imposing identification verification, least privilege entry, and steady monitoring to stop unauthorized entry.
6. How a lot does IAM software program value?
IAM pricing varies primarily based on options, deployment kind, and the variety of customers. Some distributors supply subscription-based fashions, whereas others present enterprise licensing. Further prices could embrace implementation, help, and compliance options.
7. How can I select the appropriate IAM resolution for my enterprise?
Think about: Your group’s dimension and safety want Integration capabilities along with your current instruments, Compliance necessities, Scalability, ease of use, and Assist for contemporary safety practices (e.g., Zero Belief, MFA, adaptive authentication).
8. Which is the very best identification and entry administration software program?
The very best IAM software is dependent upon your group’s wants, funds, and current infrastructure. Common IAM options embrace Okta, Microsoft Entra ID (previously Azure AD), JumpCloud, Cicso Duo, Ping Id, IBM Safety Confirm, and ForgeRock. It is best to check options, integrations, and safety capabilities earlier than selecting.
9. What’s the greatest IAM resolution for mid-sized tech firms?
JumpCloud and Okta usually stand out, providing flexibility throughout working methods, SaaS integrations, and cloud environments with out overwhelming IT groups.
10. Which IAM software program is greatest for small companies or startups?
Cisco Duo is without doubt one of the most dependable identification entry apps for startups due to its ease of use and free plan. JumpCloud additionally works nicely for small companies that want gadget administration alongside IAM.
12. What’s the best-reviewed IAM service for company environments?
In response to G2 opinions, Microsoft Entra ID and Okta persistently rank because the best-reviewed IAM platforms for company environments, balancing enterprise-grade safety with scalability.
13. What’s the most dependable identification entry app for startups?
Cisco Duo usually ranks as essentially the most dependable identification entry app for startups, due to its intuitive setup, sturdy MFA and SSO help, and a beneficiant free tier for small groups.
14. Which IAM platform is greatest for managing person roles?
Okta and Microsoft Entra ID each excel at role-based entry management (RBAC), providing granular permission administration, attribute-based guidelines, and just-in-time provisioning to assist organizations implement least-privilege entry effectively.
IAM prepared
After digging into the very best IAM software program options, I’ve come to at least one conclusion: safety ought to work with individuals, not towards them. Even when organizations put money into IAM, adoption isn’t assured. G2 knowledge reveals the typical person adoption fee is simply 71% — that means almost one in three staff nonetheless don’t absolutely use their IAM instruments. That hole creates not solely safety dangers but in addition productiveness bottlenecks.
So the true problem isn’t simply shopping for IAM software program — it’s discovering an answer that truly works in apply for you, with out including complexity to each day operations.
The strongest authentication insurance policies on the earth gained’t assist if staff discover methods round them out of frustration. On the identical time, a simple login expertise means nothing if the improper individual good points entry. That’s the balancing act each IT and safety crew faces, and the appropriate IAM software makes all of the distinction.
If your organization is deep in Microsoft’s ecosystem, Entra ID is a robust selection. JumpCloud and Okta provide you with flexibility throughout totally different platforms. Salesforce Id is sensible if Salesforce runs your online business, and Cisco Duo retains issues easy with sturdy MFA and integrations. Every software has its place, however the very best IAM resolution is the one that matches how your group really operates.
On the finish of the day, IAM isn’t nearly securing logins — it’s about defending your online business from actual threats whereas retaining entry clean for the appropriate individuals. So, decide the appropriate IAM, and also you’re not simply imposing insurance policies — you’re constructing a safety tradition that truly works.
Nonetheless on the hunt? Discover our classes of identification administration methods to search out the very best match in your safety wants.











