For the previous week, domains related to the huge Aisuru botnet have repeatedly usurped Amazon, Apple, Google and Microsoft in Cloudflare’s public rating of probably the most often requested web sites. Cloudflare responded by redacting Aisuru domains from their prime web sites listing. The chief govt at Cloudflare says Aisuru’s overlords are utilizing the botnet to spice up their malicious area rankings, whereas concurrently attacking the corporate’s area identify system (DNS) service.
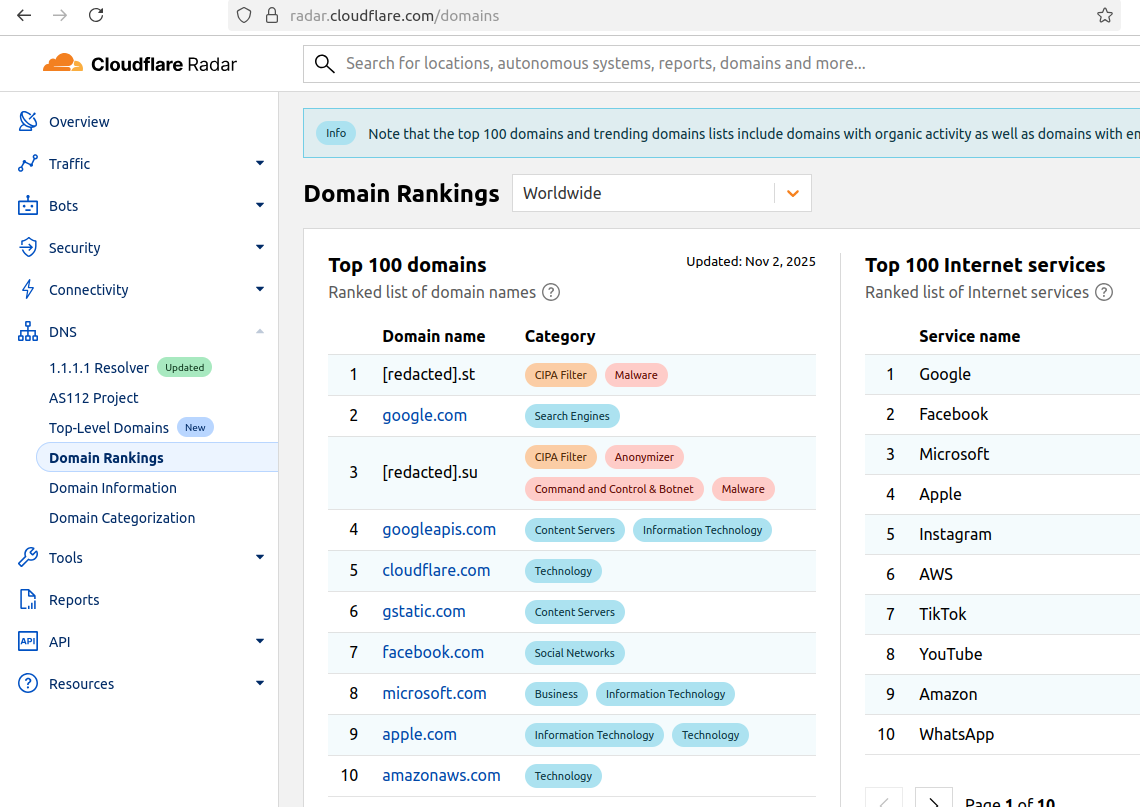
The #1 and #3 positions on this chart are Aisuru botnet controllers with their full domains redacted. Supply: radar.cloudflare.com.
Aisuru is a quickly rising botnet comprising a whole lot of 1000’s of hacked Web of Issues (IoT) units, comparable to poorly secured Web routers and safety cameras. The botnet has elevated in dimension and firepower considerably since its debut in 2024, demonstrating the flexibility to launch file distributed denial-of-service (DDoS) assaults nearing 30 terabits of knowledge per second.
Till just lately, Aisuru’s malicious code instructed all contaminated methods to make use of DNS servers from Google — particularly, the servers at 8.8.8.8. However in early October, Aisuru switched to invoking Cloudflare’s essential DNS server — 1.1.1.1 — and over the previous week domains utilized by Aisuru to regulate contaminated methods began populating Cloudflare’s prime area rankings.
As screenshots of Aisuru domains claiming two of the High 10 positions ping-ponged throughout social media, many feared this was one more signal that an already untamable botnet was operating fully amok. One Aisuru botnet area that sat prominently for days at #1 on the listing was somebody’s avenue handle in Massachusetts adopted by “.com”. Different Aisuru domains mimicked these belonging to main cloud suppliers.
Cloudflare tried to deal with these safety, model confusion and privateness issues by partially redacting the malicious domains, and including a warning on the prime of its rankings:
“Notice that the highest 100 domains and trending domains lists embrace domains with natural exercise in addition to domains with rising malicious conduct.”
Cloudflare CEO Matthew Prince instructed KrebsOnSecurity the corporate’s area rating system is pretty simplistic, and that it merely measures the quantity of DNS queries to 1.1.1.1.
“The attacker is simply producing a ton of requests, possibly to affect the rating but additionally to assault our DNS service,” Prince stated, including that Cloudflare has heard experiences of different massive public DNS companies seeing related uptick in assaults. “We’re fixing the rating to make it smarter. And, within the meantime, redacting any websites we classify as malware.”
Renee Burton, vice chairman of risk intel on the DNS safety agency Infoblox, stated many individuals erroneously assumed that the skewed Cloudflare area rankings meant there have been extra bot-infected units than there have been common units querying websites like Google and Apple and Microsoft.
“Cloudflare’s documentation is obvious — they know that on the subject of rating domains it’s important to make decisions on tips on how to normalize issues,” Burton wrote on LinkedIn. “There are numerous elements which are merely out of your management. Why is it laborious? As a result of causes. TTL values, caching, prefetching, structure, load balancing. Issues which have shared management between the area proprietor and all the things in between.”
Alex Greenland is CEO of the anti-phishing and safety agency Epi. Greenland stated he understands the technical purpose why Aisuru botnet domains are displaying up in Cloudflare’s rankings (these rankings are based mostly on DNS question quantity, not precise net visits). However he stated they’re nonetheless not meant to be there.
“It’s a failure on Cloudflare’s half, and divulges a compromise of the belief and integrity of their rankings,” he stated.
Greenland stated Cloudflare deliberate for its Area Rankings to listing the preferred domains as utilized by human customers, and it was by no means meant to be a uncooked calculation of question frequency or visitors quantity going by their 1.1.1.1 DNS resolver.
“They spelled out how their reputation algorithm is designed to replicate actual human use and exclude automated visitors (they stated they’re good at this),” Greenland wrote on LinkedIn. “So one thing has evidently gone improper internally. We must always have two rankings: one representing belief and actual human use, and one other derived from uncooked DNS quantity.”
Why would possibly or not it’s a good suggestion to wholly separate malicious domains from the listing? Greenland notes that Cloudflare Area Rankings see widespread use for belief and security willpower, by browsers, DNS resolvers, protected shopping APIs and issues like TRANCO.
“TRANCO is a revered open supply listing of the highest million domains, and Cloudflare Radar is one among their 5 knowledge suppliers,” he continued. “So there could be critical knock-on results when a malicious area options in Cloudflare’s prime 10/100/1000/million. To many individuals and methods, the highest 10 and 100 are naively thought-about protected and trusted, although algorithmically-defined top-N lists will all the time be considerably crude.”
Over this previous week, Cloudflare began redacting parts of the malicious Aisuru domains from its High Domains listing, leaving solely their area suffix seen. Someday prior to now 24 hours, Cloudflare seems to have begun hiding the malicious Aisuru domains solely from the net model of that listing. Nonetheless, downloading a spreadsheet of the present High 200 domains from Cloudflare Radar reveals an Aisuru area nonetheless on the very prime.
Based on Cloudflare’s web site, the vast majority of DNS queries to the highest Aisuru domains — practically 52 p.c — originated from the USA. This tracks with my reporting from early October, which discovered Aisuru was drawing most of its firepower from IoT units hosted on U.S. Web suppliers like AT&T, Comcast and Verizon.
Specialists monitoring Aisuru say the botnet depends on nicely greater than 100 management servers, and that for the second at the very least most of these domains are registered within the .su top-level area (TLD). Dot-su is the TLD assigned to the previous Soviet Union (.su’s Wikipedia web page says the TLD was created simply 15 months earlier than the autumn of the Berlin wall).
A Cloudflare weblog publish from October 27 discovered that .su had the best “DNS magnitude” of any TLD, referring to a metric estimating the recognition of a TLD based mostly on the variety of distinctive networks querying Cloudflare’s 1.1.1.1 resolver. The report concluded that the highest .su hostnames have been related to a preferred on-line world-building sport, and that greater than half of the queries for that TLD got here from the USA, Brazil and Germany [it’s worth noting that servers for the world-building game Minecraft were some of Aisuru’s most frequent targets].
A easy and crude strategy to detect Aisuru bot exercise on a community could also be to set an alert on any methods making an attempt to contact domains ending in .su. This TLD is often abused for cybercrime and by cybercrime boards and companies, and blocking entry to it solely is unlikely to lift any professional complaints.










