A bunch of 16 malicious browser extensions has been caught masquerading as ChatGPT productiveness aids in an try and hijack consumer accounts. Found by the analysis agency LayerX Safety, these add-ons don’t attempt to break into ChatGPT itself however look ahead to a consumer to log in after which snatch their digital credentials.
The marketing campaign entails no less than 16 distinct extensions, all developed by the identical menace actor. This appears to be a calculated transfer to make sure wider attain and maintain the marketing campaign alive in case one model was flagged, as others will discover their manner onto customers’ computer systems.
Whereas the marketing campaign has seen roughly 900 downloads thus far, a determine LayerX researchers name a “drop within the bucket” in comparison with huge scams like GhostPoster, the hazard lies in how a lot belief customers place in these instruments.
One model even managed to hold a “featured” badge on the Chrome Internet Retailer, giving it some air of authority. LayerX determined to go public now as a result of these “GPT optimisers” have gotten as frequent as VPNs, they usually needed to cease the menace earlier than it hit a “important mass.” These findings have been shared solely with Hackread.com.
Getting A Digital Key to Your Personal Life
The rip-off depends on stealing what are generally known as session tokens. Consider these as a short lived digital key that tells a web site you might be already logged in. By grabbing these keys, attackers can “impersonate them, permitting them to entry the entire consumer’s ChatGPT conversations, knowledge, or code,” LayerX’s safety researcher and weblog put up writer Natalie Zargarov defined.
The attain of this theft is surprisingly deep. As a result of many individuals join their AI instruments to work platforms, the hackers may probably see into personal Slack channels, GitHub code repositories, and Google Drive information.
Furthermore, the investigation revealed that the software program runs in a high-privilege a part of the browser, which implies it will probably “observe or manipulate” knowledge that conventional safety software program usually misses.
Marketing campaign Appears A Coordinated Assault
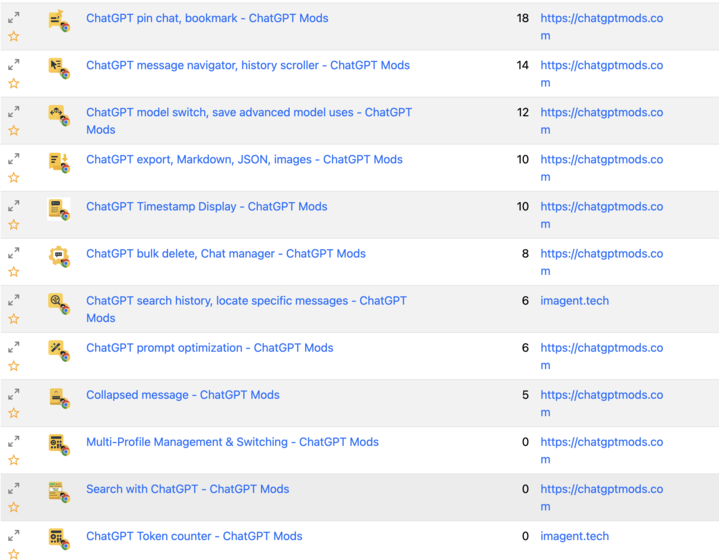
LayerX researchers imagine this wasn’t a sequence of accidents however a single, organised effort. As they probed additional, they recognized that 15 of those instruments have been on the Chrome retailer, whereas one was discovered on the Microsoft Edge market. All of them share the identical messy code and talk with particular attacker-controlled domains, together with chatgptmods.com and Imagents.prime.
One other troubling half is that these extensions have been principally uploaded in batches on the identical day and used practically similar icons and descriptions to look authentic.
“Most extensions within the marketing campaign present comparatively low particular person set up counts, with solely a small subset reaching larger adoption. We hope at LayerX that with this publication, the marketing campaign is stopped at an early stage with minimal influence,” the report concludes.
To remain protected, you could deal with any AI-linked extension as a high-risk utility. In case you have any “helper” instruments for ChatGPT put in that you just don’t recognise, one of the best transfer is to delete them.










