ESET researchers have a look again on the vital adjustments within the ransomware ecosystem in 2024 and give attention to the newly emerged and at present dominating ransomware-as-a-service (RaaS) gang, RansomHub. We share beforehand unpublished insights into RansomHub’s affiliate construction and uncover clear connections between this newly emerged large and well-established gangs Play, Medusa, and BianLian.
We additionally emphasize the rising risk of EDR killers, unmasking EDRKillShifter, a customized EDR killer developed and maintained by RansomHub. We have now noticed a rise in ransomware associates utilizing code derived from publicly out there proofs of idea, whereas the set of drivers being abused is basically fastened.
Lastly, based mostly on our observations following the law-enforcement-led Operation Cronos and the demise of the notorious BlackCat gang, we provide our insights into the way to help on this intensive combat towards ransomware.
Key factors of this blogpost:
- We found clear hyperlinks between the RansomHub, Play, Medusa, and BianLian ransomware gangs.
- We achieved this by following the path of tooling that RansomHub gives its associates.
- We doc further findings about EDRKillShifter, correlating our observations with RansomHub’s public exercise.
- We provide insights into the rising risk of EDR killers, their anatomy, and their position within the ransomware world.
Overview
The combat towards ransomware reached two milestones in 2024: LockBit and BlackCat, previously the highest two gangs, dropped out of the image. And for the primary time since 2022, recorded ransomware funds dropped, specifically by a beautiful 35% regardless of reverse expectations in the course of the yr. Then again, the recorded variety of victims posted on devoted leak websites (DLSs) elevated by roughly 15%.
An enormous a part of this enhance is because of RansomHub, a brand new RaaS gang that emerged across the time of Operation Cronos. On this blogpost, we glance in depth at RansomHub and display how we leveraged to our benefit the best way associates use RansomHub’s tooling, permitting us to attract connections between RansomHub and its rivals, together with well-established ones like Play, Medusa, and BianLian.
All through this blogpost, we consult with entities forming the ransomware-as-a-service mannequin as follows:
- Operators, who develop the ransomware payload, keep the DLS, and supply providers to associates, often for a month-to-month charge and a share of the ransom fee (sometimes 5–20%).
- Associates, who hire ransomware providers from operators, and deploy the encryptors to victims’ networks and generally additionally apply knowledge exfiltration.
The rise of RansomHub
RansomHub introduced its first sufferer on its DLS (see Determine 1) on February 10th, 2024, 10 days earlier than the general public announcement of Operation Cronos. Whereas the gang’s rise was sluggish, it was additionally constant, and when – in April 2024 – RansomHub achieved probably the most sufferer postings of all energetic ransomware teams (disregarding LockBit posting fakes), it was clear that this was a gang to maintain an in depth eye on. Since then, RansomHub has dominated the ransomware scene.
To additional display how harmful RansomHub is, let’s evaluate it to LockBit. Determine 2 exhibits the every day cumulative sum (on the y-axis) of latest victims posted on the DLS of LockBit vs. RansomHub, ranging from RansomHub’s look in February 2024.
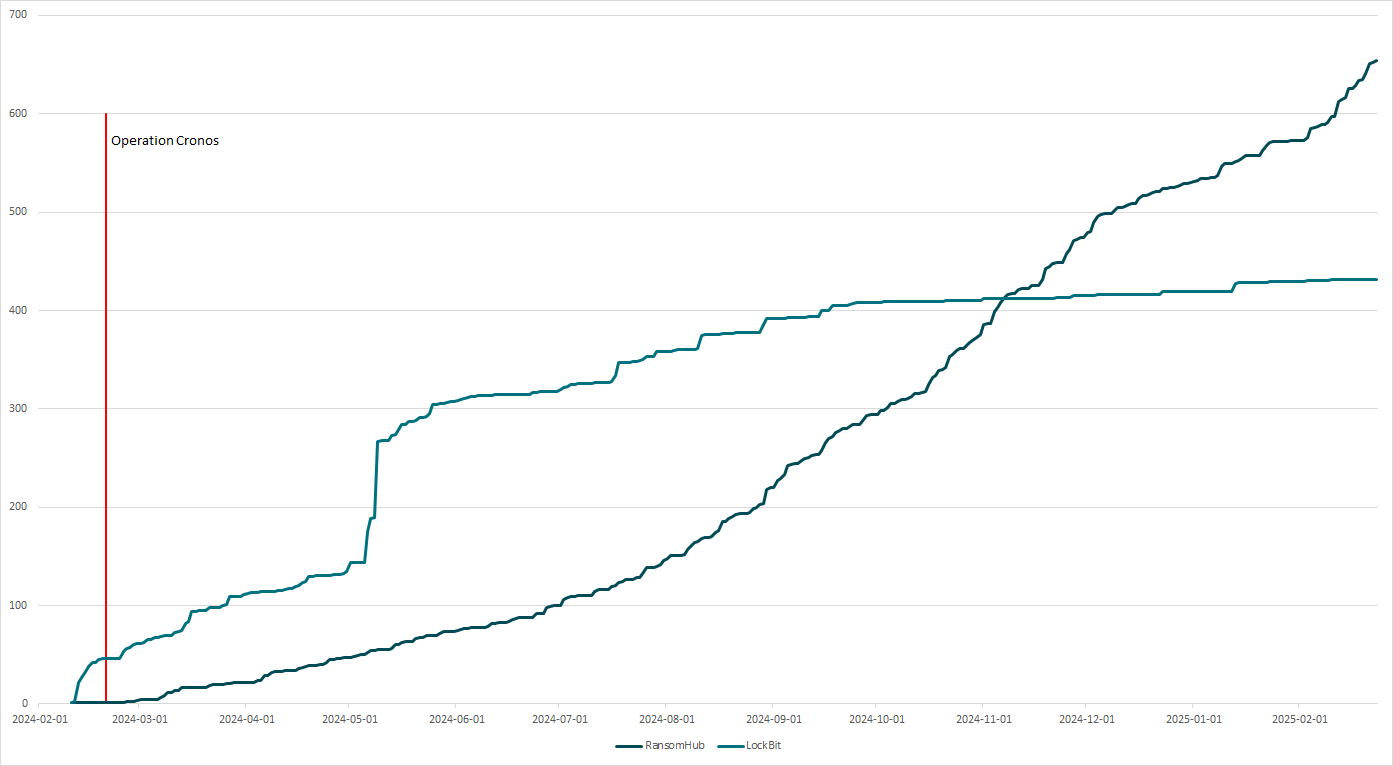
As you may clearly see, whereas RansomHub began saying victims extra slowly, almost 9 months later the gang was capable of accumulate extra victims because it began than LockBit, and that development continues to today. Contemplating that each BlackCat and LockBit suffered enormous blows proper across the time RansomHub emerged, we will confidently assume that many expert associates migrated to RansomHub; Notchy, the BlackCat affiliate who stole greater than 4 TB of information from Change Healthcare, is only one publicly identified instance.
Determine 3 exhibits the ransom observe that RansomHub associates depart on their victims’ machines.
We're the RansomHub.
Your organization Servers are locked and Information has been taken to our servers. That is critical.
Excellent news:
- your server system and knowledge might be restored by our Decryption Instrument, we help trial decryption to show that your recordsdata might be decrypted;
- for now, your knowledge is secured and safely saved on our server;
- no one on the earth is conscious in regards to the knowledge leak out of your firm besides you and RansomHub staff;
- we offer free trial decryption for recordsdata smaller than 1MB. If anybody claims they will decrypt our recordsdata, you may ask them to attempt to decrypt a file bigger than 1MB.
FAQs:
Who we're?
- Regular Browser Hyperlinks: https://ransomxifxwc5eteopdobynonjctkxxvap77yqifu2emfbecgbqdw6qd.onion.ly/
- Tor Browser Hyperlinks: http://ransomxifxwc5eteopdobynonjctkxxvap77yqifu2emfbecgbqdw6qd.onion/
Wish to go to authorities for cover?
- In search of their assistance will solely make the scenario worse,They are going to attempt to forestall you from negotiating with us, as a result of the negotiations will make them look incompetent,After the incident report is handed over to the federal government division, you can be fined ,The federal government makes use of your high-quality to reward them.And you'll not get something, and besides you and your organization, the remainder of the individuals will overlook what occurred!!!!!
Assume you may deal with it with out us by decrypting your servers and knowledge utilizing some IT Answer from third-party "specialists"?
- they'll solely make vital harm to your entire knowledge; each encrypted file might be corrupted without end. Solely our Decryption Instrument will make decryption assured;
Do not go to restoration corporations, they're basically simply middlemen who will earn money off you and cheat you.
- We're nicely conscious of circumstances the place restoration corporations let you know that the ransom worth is 5 million {dollars}, however the truth is they secretly negotiate with us for 1 million {dollars}, in order that they earn 4 million {dollars} from you. In the event you approached us instantly with out intermediaries you'd pay 5 occasions much less, that's 1 million {dollars}.
Assume your accomplice IT Restoration Firm will do recordsdata restoration?
- no they won't do restoration, solely take 3-4 weeks for nothing; in addition to your entire knowledge is on our servers and we will publish it at any time;
in addition to ship the data in regards to the knowledge breach out of your firm servers to your key companions and purchasers, rivals, media and youtubers, and so forth.
These actions from our aspect in direction of your organization may have irreversible unfavourable penalties for your small business popularity.
You do not care in any case, since you simply do not need to pay?
- We'll make you enterprise cease without end through the use of all of our expertise to make your companions, purchasers, workers and whoever cooperates together with your firm change their minds by having no alternative however to avoid your organization.
In consequence, in midterm you'll have to shut your small business.
So lets get straight to the purpose.
What do we provide in trade in your fee:
- decryption and restoration of all of your programs and knowledge inside 24 hours with assure;
- by no means inform anybody in regards to the knowledge breach out out of your firm;
- after knowledge decryption and system restoration, we are going to delete your entire knowledge from our servers without end;
- present useful advising in your firm IT safety so nobody can assault your once more.```
Now, with a view to begin negotiations, you could do the next:
- set up and run 'Tor Browser' from https://www.torproject.org/obtain/
- use 'Tor Browser' open http://ubfofxonwdb32wpcmgmcpfos5tdskfizdft6j54l76x3nrwu2idaigid.onion/
- enter your Shopper ID: [REDACTED]
* don't leak your ID or you can be banned and can by no means be capable of decrypt your recordsdata.
There might be no dangerous information on your firm after profitable negotiations for either side. However there might be loads of these dangerous information if case of failed negotiations, so do not take into consideration the way to keep away from it.
Simply give attention to negotiations, fee and decryption to make your entire issues solved by our specialists inside 1 day after fee acquired: servers and knowledge restored, every part will work good as new.
************************************************ Determine 3. RansomHub ransom observe
Recruiting part
Simply as any rising RaaS gang, RansomHub wanted to draw associates, and since there may be energy in numbers, the operators weren’t very choosy. The preliminary commercial was posted on the Russian-speaking RAMP discussion board on February 2nd, 2024, eight days earlier than the primary victims had been posted. There are some things to notice in regards to the preliminary announcement:
- Associates can obtain ransoms with their very own pockets after which afterward pay the operator.
- Associates get to maintain 90% of the ransom.
- The encryptor is obfuscated and helps Home windows, Linux, and ESXi platforms.
- RansomHub gives numerous methods to enter its RaaS program:
- Suggestion by an current affiliate.
- Proof of popularity.
- Proof of previous RaaS cooperation.
- Paying a deposit that’s returned after first profitable fee.
- Attacking Commonwealth of Unbiased States, Cuba, North Korea, and China is prohibited.
- Most well-liked communication is over qTox utilizing the ID 4D598799696AD5399FABF7D40C4D1BE9F05D74CFB311047D7391AC0BF64BED47B56EEE66A528.
Ensures like receiving ransom fee on to the affiliate’s pockets and holding a beneficiant 90% actually sound promising, particularly within the chaos following the BlackCat and LockBit disruptions. Moreover, the entry barrier may be very low, permitting even low-skilled associates to strive their luck.
It’s also value mentioning that RansomHub’s encryptor shouldn’t be written from scratch, however based mostly on repurposed code from Knight, a once-rival ransomware gang that offered its supply code in February 2024. The associates request the encryptor (typically known as a locker by RaaS operators) via the online panel provided by RansomHub (as is typical for RaaS gangs); the part accountable for producing the encryptor is usually known as a builder. As a result of info such because the distinctive sufferer ID is hardcoded within the encryptor, an affiliate must request a brand new one for each sufferer. RansomHub’s builder provides an extra layer of safety to its encryptors, a 64-character password, with out which the encryptor doesn’t work. This password is exclusive for every pattern, generated by the builder, and identified solely to the affiliate who requested the encryptor.
On June 21st, 2024, RansomHub operators modified the affiliate guidelines in response to an alleged breach by safety researchers. In response, the operator now not allowed vouching by current members as enough and strictly required a US$ 5,000 deposit for aspiring associates. This was the final noteworthy message from the RansomHub operators. Nonetheless, between the preliminary announcement and this rule change, another necessary occasion occurred, which we dive into within the subsequent part.
Increasing the arsenal – EDRKillShifter
On Could 8th, 2024, the RansomHub operators made a big replace – they launched their very own EDR killer, a particular kind of malware designed to terminate, blind, or crash the safety product put in on a vicim’s system, sometimes by abusing a susceptible driver.
RansomHub’s EDR killer, named EDRKillShifter by Sophos, is a customized instrument developed and maintained by the operator. EDRKillShifter is obtainable to RansomHub associates via the online panel, identical because the encryptor; it too is protected by a 64-character password. Performance-wise, it’s a typical EDR killer focusing on a big number of safety options that the RansomHub operators anticipate finding defending the networks they purpose to breach. A notable distinction lies within the code safety – the password protects shellcode that acts as a center layer of the killer’s execution. With out the password, safety researchers can neither retrieve the checklist of focused course of names nor the abused susceptible driver.
Sophos most likely selected “shifter” within the identify to replicate the truth that the abused driver shouldn’t be all the time the identical – at the very least two completely different susceptible drivers (abused by different identified EDR killers too) had been noticed. We dive extra in depth into EDRKillShifter and different EDR killers within the EDR killers on the rise part.
The choice to implement a killer and supply it to associates as a part of the RaaS program is uncommon. Associates are sometimes on their very own to search out methods to evade safety merchandise – some reuse current instruments, whereas extra technically oriented ones modify current proofs of idea or make the most of EDR killers out there as a service on the darkish net. Evidently, ransomware associates thought this was a good suggestion, as a result of quickly after the announcement, ESET researchers noticed a steep enhance in the usage of EDRKillShifter, and never completely in RansomHub circumstances, as we display within the subsequent part.
Roughly a month after EDRKillShifter’s announcement, on June 3rd, 2024, RansomHub operators posted one more replace, stating that they improved EDRKillShifter. ESET telemetry exhibits that some associates deployed this up to date model solely 4 days later.
Leveraging EDRKillShifter
ESET researchers took benefit of the large recognition that EDRKillShifter gained upon its launch to increase our analysis. We had been capable of leverage its utilization to affiliate RansomHub associates with the a number of rival gangs that additionally they work for, in addition to to retrieve clearer inside versioning of this EDR killer.
Linking associates to rival gangs
The distinction between RansomHub’s encryptor and EDRKillShifter is that there isn’t a motive for associates to construct a brand new pattern of EDRKillShifter for each intrusion (except there’s a main replace) – which is precisely what allowed us to uncover certainly one of RansomHub’s associates working for 3 rival gangs – Play, Medusa, and BianLian.
These three gangs differ considerably:
- BianLian focuses totally on extortion-only assaults, with no RaaS program providing on its DLS.
- Medusa doesn’t supply a RaaS program on its DLS both, however advertises its RaaS program on the RAMP underground discussion board.
- Play strictly denies ever operating a RaaS program on its DLS.
Discovering a hyperlink between RansomHub and Medusa shouldn’t be that stunning, as it is not uncommon information that ransomware associates typically work for a number of operators concurrently. Nonetheless, we didn’t anticipate well-established gangs working below the closed RaaS mannequin (that means that they don’t actively search for new recruits and their partnerships are based mostly on long-term mutual belief) to type alliances with RansomHub so shortly. Different well-established gangs, along with BianLian and Play, additionally function below the closed RaaS mannequin – the latest BlackBasta leak provided distinctive perception into the interior workings of such teams.
One strategy to clarify Play and BianLian getting access to EDRKillShifter is that they employed the identical RansomHub affiliate, which is unlikely given the closed nature of each gangs. One other, extra believable clarification is that trusted members of Play and BianLian are collaborating with rivals, even newly emerged ones like RansomHub, after which repurposing the tooling they obtain from these rivals in their very own assaults. That is particularly fascinating, since such closed gangs sometimes make use of a quite constant set of core instruments throughout their intrusions. Earlier than diving into the specifics of the found overlaps, let’s briefly introduce the modus operandi of the Play gang.
Play’s modus operandi
The Play gang posted the primary victims to its DLS on November 26th, 2022; the gang has proven regular development since then. In April 2024, Play made it to the highest three most energetic ransomware gangs on the scene and constantly remained within the prime 10 for the entire yr. The gang posts 25 new victims every month, on common, specializing in SMBs, hinting that the gang has at the very least a number of skilled, loyal associates. Lately, Play has been linked to the North Korea-aligned group Andariel.
As anticipated from a closed RaaS gang, most circumstances involving the Play encryptor present similarities. Sometimes, in such intrusions:
- the encryptors are saved in %PUBLICpercentMusic<6_random_alphanumeric_characters>.exe,
- SystemBC is utilized for payload supply and serves as a proxy,
- Grixba, a customized community scanner, is commonly used, and
- further tooling is commonly downloaded instantly from an IP handle.
The rest of the assault sometimes employs a large arsenal of instruments, in addition to living-off-the-land methods.
The puzzle
Let’s look in depth on the hyperlinks we found. We emphasize first a very powerful ones in Determine 4 after which dive into the small print of every of the intrusions. We imagine with excessive confidence that every one these assaults had been carried out by the identical risk actor, working as an affiliate of the 4 ransomware gangs proven in Determine 4. We’re not monitoring this risk actor below a devoted identify at this level, however for comfort, we’ll consult with this risk actor as QuadSwitcher.
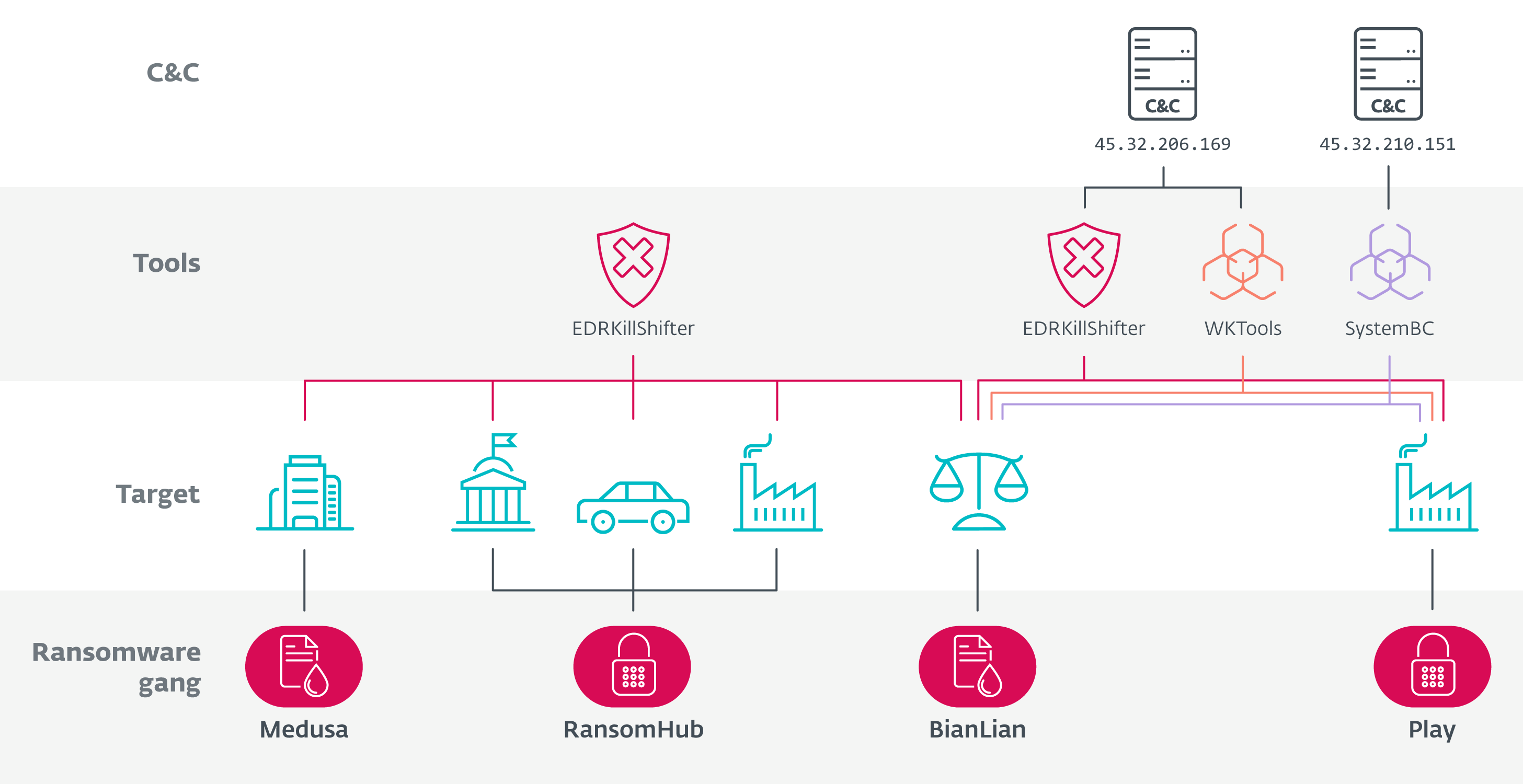
As you may see in Determine 4, there are a complete of 5 intrusions from 4 completely different ransomware gangs interlinked by:
- two EDRKillShifter samples (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257 and 77DAF77D9D2A08CC22981C004689B870F74544B5),
- the payload supply server 45.32.206[.]169 internet hosting EDRKillShifter and WKTools (a utility to discover and modify the Home windows kernel, utilized in many Play intrusions), and
- SystemBC with C&C server 45.32.210[.]151.
The next sections go into the person intrusions in additional element.
RansomHub
In July 2024, QuadSwitcher deployed the RansomHub encryptor together with EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257) to a producing firm in Western Europe and an automotive firm in Central Europe.
In August, QuadSwitcher compromised a governmental establishment in North America utilizing PuTTY, and shortly after Rclone. They proceeded by putting in AnyDesk and defending it with a password by way of a PowerShell script, anydes.ps1 (a part of the Conti leaks). Making an attempt to evade the safety resolution, the risk actor deployed EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257) and TDSSKiller.
BianLian
On the finish of July 2024, QuadSwitcher compromised an organization within the authorized sector in North America. Throughout that intrusion, the risk actor dumped the Lively Listing by executing
powershell “ntdsutil.exe ‘ac i ntds’ ‘ifm’ ‘create full c:temp1’ q q”,
deployed AnyDesk by way of the identical set up script from the Conti leaks, and used Superior IP Scanner to scan the community. Six days later, the attacker put in the ScreenConnect and Ammyy Admin distant monitoring and administration (RMM) instruments and deployed EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257). After virtually a month of no exercise, the attacker returned and downloaded two payloads from http://45.32.206[.]169/:
- WKTools.exe, the WKTools, utility typically utilized by Play
- Killer.exe, an occasion of EDRKillShifter (SHA-1: 77DAF77D9D2A08CC22981C004689B870F74544B5)
Moreover, QuadSwitcher deployed SystemBC utilizing 45.32.210[.]151 as its C&C server, and a signature BianLian backdoor with C&C server 92.243.64[.]200:6991 from http://149.154.158[.]222:33031/win64_1.exe. The sufferer was later introduced on BianLian’s DLS.
Play
In early August 2024, QuadSwitcher compromised a producing firm in North America. They deployed SystemBC with C&C 45.32.210[.]151, EDRKillShifter (SHA-1: 77DAF77D9D2A08CC22981C004689B870F74544B5), and WKTools, downloaded from http://45.32.206[.]169/WKTools.exe. In the end, the risk actor deployed the Play encryptor.
Medusa
On the finish of August 2024, QuadSwitcher compromised a know-how firm in Western Europe, downloading PuTTY from http://130.185.75[.]198:8000/plink.exe utilizing certutil.exe, adopted through the use of Course of Explorer and EDRKillShifter (SHA-1: BF84712C5314DF2AA851B8D4356EA51A9AD50257). The risk actor additionally downloaded MeshAgent from http://79.124.58[.]130/dl/git.exe, additionally by way of certutil.exe. The sufferer was later introduced on Medusa’s DLS.
The puzzle – conclusion
Moreover the hyperlinks summarized in Determine 4, there are TTPs that the majority resemble typical Play intrusions. In three of the circumstances, further malware and instruments had been downloaded from a root folder of a server accessed by way of an IP handle utilizing HTTP and QuadSwitcher additionally used SystemBC, commodity malware closely utilized by the Play gang. These hyperlinks lead us to imagine QuadSwitcher is said to Play the closest.
Moreover, QuadSwitcher has entry to at the very least two EDRKillShifter samples, compiled two months aside, signaling the risk actor had prolonged entry to RansomHub’s tooling.
Reconstructing EDRKillShifter improvement timeline
In September 2024, ESET researchers documented a case the place CosmicBeetle, an immature ransomware risk actor utilizing its personal signature encryptor, ScRansom, and the leaked LockBit 3.0 builder, grew to become an affiliate of RansomHub. Observe that CosmicBeetle shouldn’t be a gang, however a person distributing and growing numerous ransomware. Following the publication of our findings, we noticed CosmicBeetle additional make the most of EDRKillShifter throughout:
- a RansomHub assault towards a hospitality firm in South America in August 2024,
- a pretend LockBit assault towards an automotive firm in Central Europe in August 2024,
- a pretend LockBit assault towards a producing firm in East Asia in September 2024, and
- an assault with no encryptor deployed towards an unknown firm within the Center East in January 2025.
Different immature ransomware associates had been noticed utilizing EDRKillShifter earlier than deploying their customized encryptors (typically created just by utilizing the leaked LockBit 3.0 builder) as nicely. This exhibits one weak point of RansomHub – in its greed to develop as shortly as attainable, it wasn’t very choosy about its associates. In consequence, it was, by its personal admission, breached by safety researchers in June 2024. Moreover, immature associates have a tendency to go away considerably extra trails, which enabled us to be taught extra about each them and RansomHub.
Within the blogpost about CosmicBeetle, we talked about EDRKillShifter being deployed from an uncommon path C:UsersAdministratorMusic1.0.8.zip. Within the following months, a number of different immature associates left related trails that enabled us to partially reconstruct EDRKillShifter’s versioning, demonstrated in Desk 1. The VERSIONINFO column refers to EDRKillShifter’s model as listed in its VERSIONINFO useful resource, whereas the Deployment path refers back to the model talked about within the path found by ESET telemetry.
Desk 1. EDRKillShifter versioning
| Compilation date | VERSIONINFO | Deployment path |
| 2024-05-01 | 1.2.0.1 | N/A |
| 2024-06-06 | 1.2.0.1 | 1.0.7 / 1.0.8 |
| 2024-06-07 | 1.6.0.1 | 2.0.1 |
| 2024-07-10 | 2.6.0.1 | 2.0.4 |
| 2024-07-24 | 2.6.0.1 | 2.0.5 |
Following July 2024, there was solely a single very generic replace from the RansomHub operator posted on RAMP, correlating with our not seeing new variations of EDRKillShifter within the wild. Reconstructing the event timeline of EDRKillShifter additionally allowed us to identify these improvement practices:
- The InternalName property of the model data useful resource being both Config.exe or Loader.exe.
- The OriginalName property of the model data useful resource all the time being Loader.exe.
- The deployment filename various, mostly being Killer.exe, Magic.exe, or Loader.exe.
- The identify of the argument accepting the 64-character-long password being named both cross or key.
EDR killers on the rise
EDRKillShifter shortly gained recognition amongst ransomware associates, and as we simply demonstrated, they don’t use it completely in RansomHub intrusions. Nonetheless, it’s not the one EDR killer on the market; the truth is, ESET researchers have noticed a rise within the number of EDR killers utilized by ransomware associates.
An EDR killer is malware designed to run in a compromised community, to blind, corrupt, crash, or terminate safety options defending the endpoints. The apparent objective is to permit clean execution of the ransomware encryptor. Whereas extra immature ransomware associates settle with scripts that merely attempt to terminate a listing of processes, extra refined ones transcend that and use the method often called Deliver Your Personal Susceptible Driver (BYOVD).
EDR killers are an efficient and more and more well-liked addition to ransomware associates’ arsenals. Throughout an intrusion, the objective of the affiliate is to acquire admin or area admin privileges. Ransomware operators have a tendency to not do main updates of their encryptors too typically as a result of threat of introducing a flaw that would trigger points, finally damaging their popularity. In consequence, safety distributors detect the encryptors fairly nicely, which the associates react to through the use of EDR killers to “do away with” the safety resolution simply earlier than executing the encryptor.
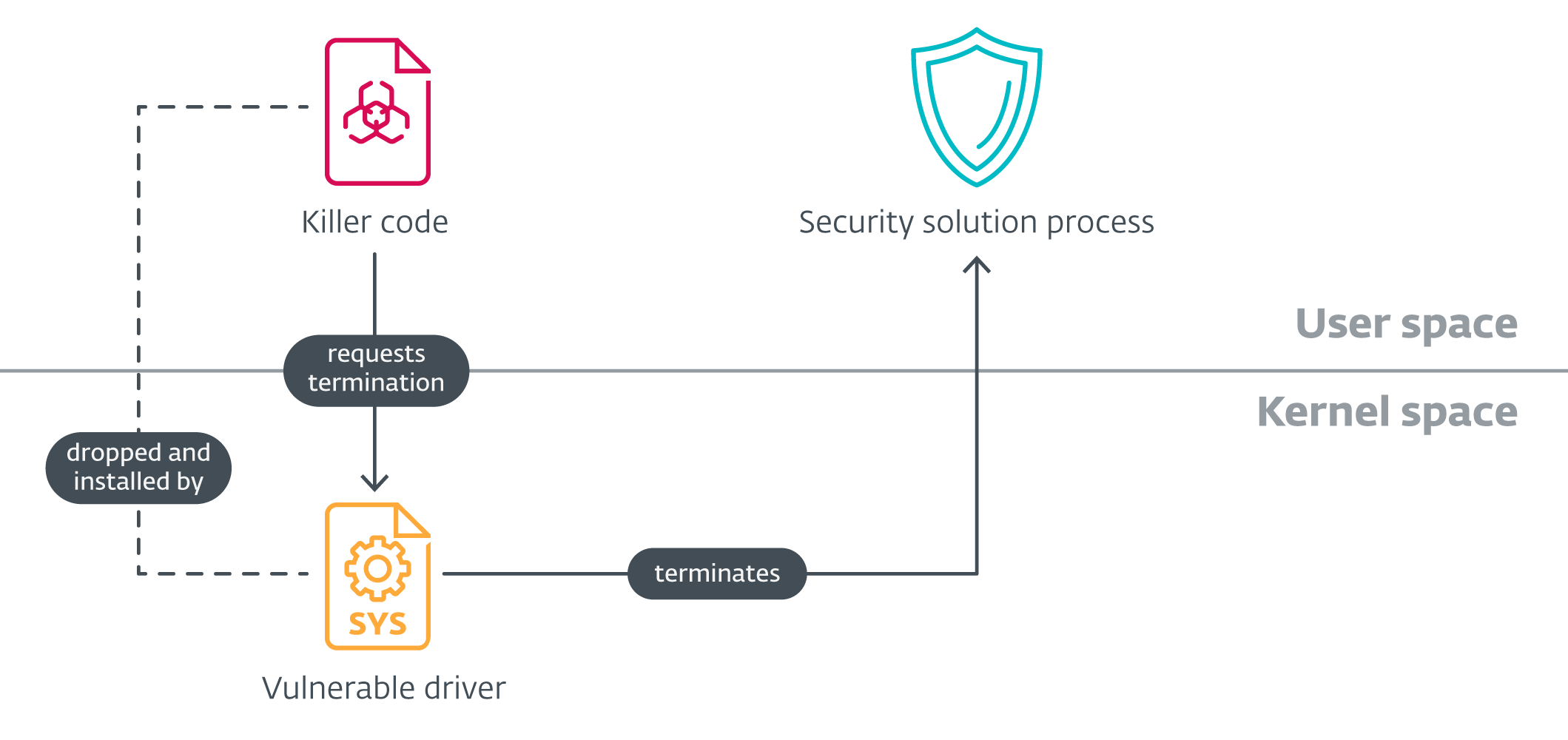
Anatomy of an EDR killer
Superior EDR killers include two elements – a consumer mode part accountable for orchestration (which we are going to consult with because the killer code) and a authentic, however susceptible, driver. The execution is usually very easy – the killer code installs the susceptible driver, sometimes embedded in its knowledge or sources, iterates over a listing of course of names, and points a command to the susceptible driver, leading to triggering the vulnerability and killing the method from kernel mode.
Few drivers, many killers
Sophos documented of their blogpost how completely different builds of EDRKillShifter abuse completely different susceptible drivers. One of many abused drivers, rentdrv2.sys, can be part of BadRentdrv2, a publicly out there EDR killer. The second, TFSysMon from ThreatFire System Monitor, can be part of TFSysMon-Killer, one other publicly out there PoC. The latter is a part of an even bigger assortment of 4 EDR killer PoCs written in Rust, which we now have noticed risk actors reimplement in C++ with out altering a single line of code.
Whereas the Residing Off The Land Drivers venture supplies over 1700 susceptible drivers, making them a profitable goal for cybercriminals, solely a handful of those drivers are abused by EDR killers – if there may be examined code abusing a vulnerability in certainly one of these drivers, it’s a lot simpler to reuse it with out having to design the code from scratch. Moreover, it permits the EDR killer builders to give attention to the killer code and its stealthiness.
Grey zone of EDR killers
Official instruments are abused by ransomware associates to work as EDR killers, too. Such instruments, just like the GMER rootkit detector and PC Hunter, by their nature require entry to kernel mode and must intently examine the internals of the working system. Sadly, additionally they supply a strong performance that may be abused when within the palms of malicious risk actors.
Including EDR killers to RaaS choices
RaaS packages typically don’t present associates solely with encryptors – further instruments and playbooks could also be a part of the bundle. As an example, LockBit provided Stealbit, a customized knowledge exfiltration instrument, to its associates, and the Conti leaks and Dispossessor leak disclosed that playbooks, scripts, and know-how are additionally a part of the ransomware gangs’ arsenal.
Including an EDR killer to a RaaS providing appears logical, and RansomHub shouldn’t be the one gang doing that. In October 2024, ESET researchers documented that the rising ransomware gang Embargo applied its personal EDR killer as nicely, known as MS4Killer, by modifying a publicly out there PoC. On the time of writing: whereas the group listed solely 14 victims on its DLS, it had already invested time and sources into growing its personal EDR killer.
It stays to be seen whether or not EDR killers discover their place in additional gangs’ choices. Nonetheless, this blogpost has additionally demonstrated that researchers could leverage their utilization to cluster associates and uncover new relationships between rival gangs.
Defeating EDR killers
Defending towards EDR killers is difficult. Risk actors want admin privileges to deploy an EDR killer, so ideally, their presence needs to be detected and mitigated earlier than they attain that time.
Whereas stopping the killer code from executing is one of the best method, code obfuscation could make this unreliable. Nonetheless, specializing in susceptible drivers supplies further protection choices. ESET considers drivers exploited by EDR killers doubtlessly unsafe. Due to this fact, customers, particularly in company environments, ought to be sure that the detection of doubtless unsafe purposes is enabled. This may forestall the set up of susceptible drivers.
Though not frequent, refined risk actors could exploit a susceptible driver already current on a compromised machine as an alternative of counting on BYOVD. To counter this, having correct patch administration in place is an efficient and important protection technique.
Conclusion
The ransomware ecosystem suffered vital blows in 2024. Regardless of the general variety of recorded assaults growing, it shouldn’t overshadow the optimistic impact of efficiently disrupting or eliminating two ransomware gangs that had been dominating the scene for years.
We are able to speculate about how a lot the results of regulation enforcement actions decreased ransomware funds, or how the rising consciousness and initiatives just like the Counter Ransomware Initiative are serving to ransomware victims perceive that paying the ransom is probably not the easiest way ahead.
What is evident, sadly, is {that a} new refined ransomware group, RansomHub, emerged, used the precise techniques to draw associates (a lot of whom we imagine transitioned from BlackCat and LockBit) in a brief interval, and was shortly capable of climb to the highest of the ladder. Within the foreseeable future, RansomHub will certainly attempt to stay among the many most energetic RaaS gangs.
Legislation-enforcement-led disruptions of RaaS operators have proved efficient, sowing mistrust within the RaaS ecosystem. Sadly, 2024 confirmed that associates are capable of regroup pretty shortly. In spite of everything, they’ve sturdy monetary incentives to deploy encryptors to and exfiltrate delicate knowledge from their targets. Though tougher to perform than disruptions, eliminating probably the most energetic associates from the image can be efficient as a result of it might probably forestall new RaaS operators from gaining energy as shortly as RansomHub did. We imagine that specializing in the associates, particularly by monitoring down their hyperlinks between numerous gangs – as demonstrated on this blogpost between RansomHub, Play, Medusa, and BianLian – will finally result in identification of the associates and their elimination from the sport.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis gives non-public APT intelligence studies and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete checklist of indicators of compromise and samples might be present in our GitHub repository.
Information
SHA-1
Filename
Detection
Description
97E13515263002809505
amd64.exe
WinGo/Kryptik.CV
RansomHub encryptor.
BF84712C5314DF2AA851
Loader.exe
Win64/Agent.DVP
EDRKillShifter.
87D0F168F049BEFE455D
amd64.exe
WinGo/Kryptik.CV
RansomHub encryptor.
2E89CF3267C8724002C3
Magic.exe
Win64/Agent.DVP
EDRKillShifter.
3B035DA6C69F9B05868F
TDSSKiller.exe
Win32/RiskWare.
TDSSKiller.
5ECAFF68D36EC1033742
svchost.exe
WinGo/HackTool.
Rclone.
DCF711141D6033DF4C91
anydes.ps1
PowerShell/Agent.AEK
Script that deploys and password protects AnyDesk.
E38082AE727AEAEF4F24
netscan.exe
Win64/NetTool.Gentle
SoftPerfect Community Scanner.
046583DEB4B418A6F1D8
conhost.dll
Win64/Coroxy.J
SystemBC.
3B4AEDAFA9930C19EA88
win64_1.exe
Win64/Agent.RA
BianLian backdoor.
460D7CB14FCED78C701E
WKTools.exe
Win32/WKTools.A
WKTools.
5AF059C44D6AC8EF92AA
pfw.exe
Win64/Agent.RA
BianLian backdoor.
67D17CA90880B448D5C3
1721894530.sys
Win64/RentDrv.A
Susceptible driver utilized by EDRKillShifter.
77DAF77D9D2A08CC2298
Killer.exe
Win64/Agent.DVP
EDRKillShifter.
180D770C4A55C62C09AA
1.dll
Win64/Coroxy.Ok
SystemBC.
DD6FA8A7C1B3E009F5F1
d.exe
Win32/Filecoder
Play encryptor.
FDA5AAC0C0DB36D173B8
GT_NET.exe
MSIL/Spy.Grixba.A
Grixba.
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 45.32.206[.]169 | N/A | Vultr Holdings, LLC | 2024‑07‑25 | Server internet hosting WKTools and EDRKillShifter. |
| 45.32.210[.]151 | N/A | The Fixed Firm, LLC | 2024‑08‑09 | SystemBC C&C server. |
| 79.124.58[.]130 | N/A | TAMATYA-MNT | 2024‑08‑22 | Server internet hosting MeshAgent. |
| 92.243.64[.]200 | N/A | EDIS GmbH – Noc Engineer | 2024‑07‑25 | BianLian backdoor C&C server. |
| 130.185.75[.]198 | N/A | Pars Parva System LTD | 2024‑08‑20 | Server internet hosting PuTTY. |
| 149.154.158[.]222 | N/A | EDIS GmbH – Noc Engineer | 2024‑07‑25 | Server internet hosting BianLian backdoor. |
MITRE ATT&CK methods
This desk was constructed utilizing model 16 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Useful resource Improvement | T1583 | Purchase Infrastructure | QuadSwitcher acquired infrastructure to host their tooling. |
| T1587.001 | Develop Capabilities: Malware | The RansomHub, Play, Medusa, and BianLian gangs develop their very own encryptors and associated tooling. | |
| T1588.001 | Get hold of Capabilities: Malware | The Play gang makes use of SystemBC, a commodity malware on the market. | |
| T1588.002 | Get hold of Capabilities: Instrument | Numerous third-party instruments are frequently utilized by the gangs’ associates. | |
| T1608.001 | Stage Capabilities: Add Malware | The Play gang uploaded its personal tooling to a devoted server for use throughout intrusions. | |
| T1608.002 | Stage Capabilities: Add Instrument | The Play gang uploaded the third-party instruments it makes use of to a devoted server for use throughout intrusions. | |
| Execution | T1059.001 | Command-Line Interface: PowerShell | QuadSwitcher deployed AnyDesk utilizing a PowerShell script. |
| T1059.003 | Command-Line Interface: Home windows Command Shell | Home windows Command Shell is frequently utilized by QuadSwitcher to difficulty instructions. | |
| Protection Evasion | T1078 | Legitimate Accounts | QuadSwitcher abuses extracted credentials of legitimate accounts to maneuver within the community stealthily. |
| T1078.002 | Legitimate Accounts: Area Accounts | QuadSwitcher finally gained area admin privileges in among the intrusions. | |
| T1480 | Execution Guardrails | RansomHub’s encryptor requires a password to run. | |
| T1562.001 | Impair Defenses: Disable or Modify Instruments | EDRKillShifter’s purpose is to disable safety options. | |
| T1562.009 | Impair Defenses: Protected Mode Boot | RansomHub’s encryptor permits rebooting to protected mode to encrypt recordsdata. | |
| T1218 | System Binary Proxy Execution | QuadSwitcher abused certutil.exe to obtain payloads. | |
| Credential Entry | T1110 | Brute Drive | QuadSwitcher tried to brute pressure credentials in the course of the intrusions. |
| Discovery | T1087 | Account Discovery | To be able to elevate privileges, QuadSwitcher found further accounts. |
| T1057 | Course of Discovery | EDRKillShifter appears for particular processes associated to safety options. | |
| Lateral Motion | T1021.001 | Distant Companies: Distant Desktop Protocol | RDP was typically used for lateral motion within the compromised networks. |
| T1021.002 | Distant Companies: SMB/Home windows Admin Shares | RansomHub helps distant encryption of recordsdata. | |
| Assortment | T1005 | Information from Native System | The BianLian gang focuses on knowledge exfiltration, gathering knowledge from native drives. |
| T1039 | Information from Community Shared Drive | The BianLian gang focuses on knowledge exfiltration, gathering knowledge from community drives. | |
| Command and Management | T1071 | Utility Layer Protocol | In Play intrusions, payloads are retrieved by way of HTTP. |
| T1132.002 | Information Encoding: Non-Normal Encoding | SystemBC employs a customized community protocol. | |
| T1219 | Distant Entry Software program | A number of RMM instruments had been used, together with AnyDesk and MeshAgent. | |
| Exfiltration | T1537 | Switch Information to Cloud Account | BianLian associates used Rclone to exfiltrate knowledge to a cloud account they management to keep away from typical file transfers/downloads and network-based exfiltration detection. |
| Influence | T1485 | Information Destruction | Some knowledge like backups could also be completely destroyed by ransomware gangs. |
| T1486 | Information Encrypted for Influence | The final word results of ransomware gangs’ actions is encryption of victims’ knowledge. | |
| T1657 | Monetary Theft | The ransomware gangs stress victims to pay ransom in trade for regaining entry to their knowledge. |











