Spotify boasts virtually 700 million energetic customers, together with 265 million premium subscribers. Because the world’s main music streaming service, it’s hardly stunning that it additionally attracts all method of dangerous actors who’re keen to use its customers.
Spotify accounts symbolize helpful digital belongings that may be monetized by way of a number of channels, together with on the darkish internet and the shadowy corners of Telegram. Whereas discounted in comparison with reliable subscription prices, the going costs of hacked Spotify accounts typically generate substantial income when bought in bulk. A single profitable phishing marketing campaign focusing on Spotify customers can yield massive numbers of accounts, which interprets into appreciable unlawful income.
Compromised accounts present helpful private information that can be utilized for id theft or social engineering assaults. Entry to a Spotify account could reveal private data, cost particulars, listening habits, and connections to social media and different on-line companies, which creates alternatives for extra focused assaults.
Moreover, hacked accounts function automobiles for artificially inflating stream counts. This apply, often known as “streaming fraud”, entails utilizing networks of compromised accounts to repeatedly play particular tracks, producing fraudulent royalty funds. Based on Beatdapp, a streaming fraud detection platform, at the least 10% of all track streams are fraudulent, taking as much as US$3 billion out of the worldwide music trade annually.
Now, understanding how Spotify accounts might be hacked is step one in direction of staying secure. Let’s evaluate the principle ways utilized by cybercriminals to acquire consumer credentials, the crimson flags to be careful for, and the best way to inform that your account could have been compromised.
Phishing
Phishing emails are a staple tactic, though many of those schemes have developed considerably past apparent rip-off emails replete with spelling errors and different giveaways. A lot of at present’s phishing campaigns depend on superior social engineering strategies and convincing visible components that may idiot even loads of cautious customers.
Typically talking, nevertheless, phishing ploys typically start with an e mail about supposedly severe points along with your account, akin to “Cost Technique Declined: Subscription Will Be Canceled.” These messages create a way of urgency and infrequently cloud judgment and improve the probability of hasty actions, particularly in the event that they’re full with official Spotify logos and formatting almost an identical to reliable Spotify communications.
For instance, a phishing e mail would possibly declare that your account shall be deactivated as a result of a cost difficulty. It is going to then immediate you to click on on a hyperlink to “resolve” the issue. As an alternative, you’ll find yourself on an imposter website that’s designed to steal your login credentials and presumably different delicate data.
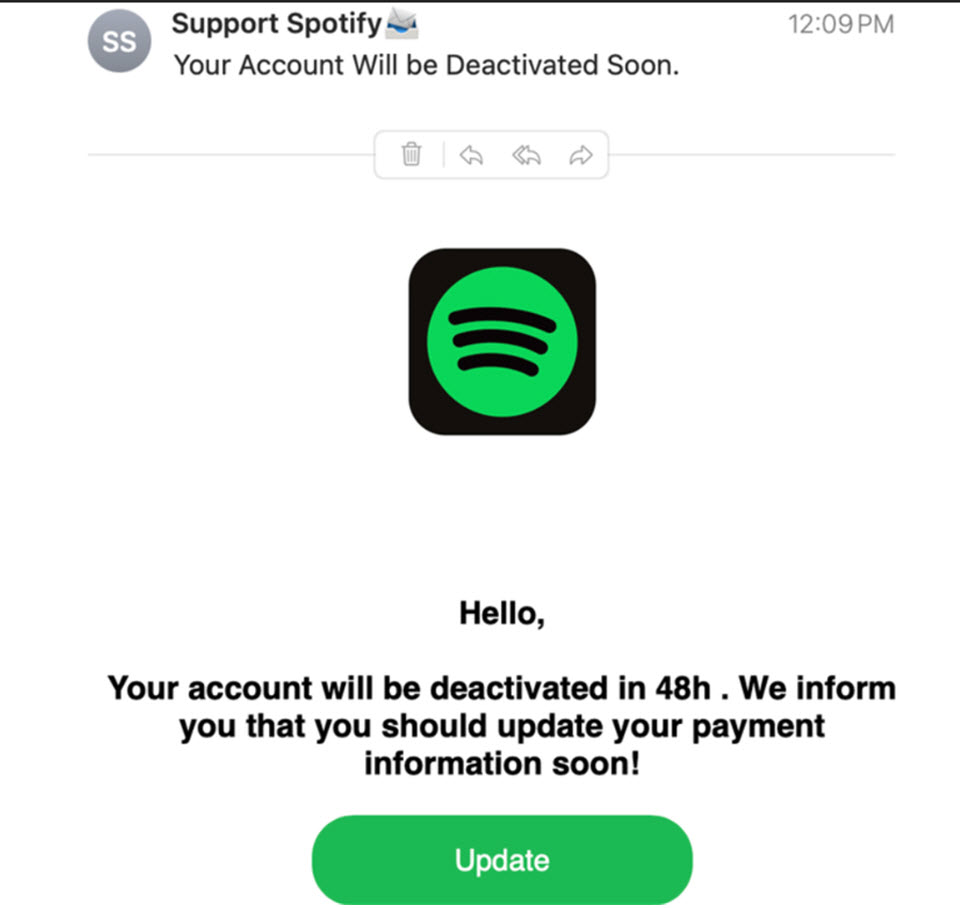
Phishing hyperlinks typically direct customers to imposter web sites that usually mirror Spotify’s login web page and even their domains seem reliable, at first look anyway.
These easy suggestions will go a great distance in direction of protecting you secure:
- Be skeptical of requests to your private data – Spotify won’t ever ask to your private data, akin to cost strategies or your password, nor will it ask you to pay by way of third events or obtain e mail attachments.
- Confirm the e-mail sender’s handle fastidiously – reliable Spotify emails come from domains ending with “@spotify.com”
- Test for spelling and grammar errors or different indicators that one thing isn’t proper: reliable emails often don’t comprise these sorts of errors.
- Hover over any hyperlink with out clicking to view the precise vacation spot URL.
- Manually navigate to Spotify by typing the handle in your browser moderately than clicking e mail hyperlinks.
- Defend your account with a robust and distinctive password, saved in a password supervisor, and allow two-factor authentication on it, ideally by way of an authenticator app or a {hardware} safety key.
Pretend apps
The attract of enhanced options and free premium entry has led to a proliferation of unauthorized Spotify third-party apps. These unofficial apps vary from seemingly harmless feature-enhancers to intentionally malicious software program designed to reap credentials.
Utilizing juicy lures, akin to blocking adverts and in any other case enhancing the free Spotify expertise, these apps search to take over the account.

To guard your self, stick with official app shops and solely obtain the Spotify app from official channels: the Apple App Retailer for iOS units, Google Play Retailer for Android units, and spotify.com for desktop shoppers.
Avoid any third-party instruments that promise to reinforce Spotify or present premium options with out cost, as these are virtually universally malicious. Moreover, repeatedly evaluate the functions put in in your units and take away any that you do not acknowledge or now not use.
Malware
The malware panorama focusing on streaming service credentials has grown more and more subtle. Past fundamental keyloggers, cybercriminals can now deploy malware particularly designed to focus on leisure service credentials, for instance whereas masquerading as browser extensions promising to reinforce streaming experiences or to permit downloading content material for offline use. Info-stealing malware can also be typically distributed by way of compromised software program downloads or malicious e mail attachments.
Preserve all software program up to date, as updates typically embody safety patches for recognized vulnerabilities. Use a good safety answer with real-time safety capabilities. Train warning when granting permissions to functions, particularly these requesting entry to delicate capabilities like accessibility companies or password managers.
Knowledge leaks
Knowledge breaches typically result in account takeovers partly due to folks’s penchant for reusing passwords throughout completely different companies. Given how interconnected our digital lives are, a information breach in a single service can result in account compromises throughout a number of platforms. There have been instances the place credentials uncovered in main information breaches or leaks have been efficiently utilized in credential-stuffing assaults on 1000’s of Spotify accounts.
To remain secure, implement a password administration technique that eliminates password reuse. Respected password managers generate distinctive, complicated passwords for every service and securely retailer them, requiring you to recollect solely a single grasp password. Moreover, repeatedly monitor breach notification companies like HaveIBeenPwned, which is able to provide you with a warning in case your e mail seems in new information breaches, permitting you to take fast motion earlier than it’s too late.
How can I inform if my Spotify account has been hacked?
The obvious signal is sudden modifications to your account settings or subscription particulars. This would possibly embody unauthorized upgrades or downgrades to your subscription plan, modifications to your e mail handle, or modifications to your cost information.
Uncommon exercise in your listening historical past or playlists may point out account compromise. This would possibly manifest as unfamiliar artists showing in your not too long ago performed tracks. In different instances, you would possibly encounter unexplained disappearance of playlists you’ve created or new playlists showing that you just did not create.
A lot the identical goes for session anomalies, which, too, also can reveal unauthorized entry. Spotify’s account web page exhibits all units the place your account is at the moment energetic. Unfamiliar units or areas on this listing strongly recommend your account has been compromised. Equally, when you continuously end up unexpectedly logged out of Spotify, this will likely point out another person is accessing your account and triggering session limits.
In the event you discover any of those crimson flags, try this Spotify web page and take fast motion:
- First, sign off of all units by way of your account settings web page.
- Then change your password instantly, guaranteeing the brand new password is powerful and distinctive.
- Subsequent, evaluate and revoke entry for any third-party functions you don’t acknowledge or now not use.
- Lastly, contact Spotify buyer help to report the unauthorized entry and request extra account safety measures.
Staying secure
Ensure that your digital kingdom is locked down. The jiffy spent securing your account at present may prevent hours of frustration tomorrow. Certainly, when you’re armed with data of attacker ways and the safety methods, you possibly can slam the door on would-be account thieves.
But additionally keep in mind that safety isn’t a set-it-and-forget-it characteristic. It’s a dwelling apply that evolves as rapidly because the threats themselves. Keep on high of the most recent risks lurking within the on-line area.











