Researchers at Forcepoint X-Labs have found a phishing marketing campaign utilizing Phorpiex malware to ship World Group ransomware. The assault makes use of misleading Home windows shortcut information (.lnk) and a singular ‘mute’ mode to encrypt knowledge offline and evade conventional safety detection.
A serious new safety report has alerted the general public to an enormous international e-mail rip-off designed to hijack computer systems and lock away private information. Researchers at Forcepoint X-Labs, led by Senior Safety Researcher Lydia McElligott, have found {that a} long-running hacker community often called Phorpiex, lively since roughly 2010, is now getting used to unfold a nasty sort of virus referred to as World Group ransomware.
A Acquainted Entice
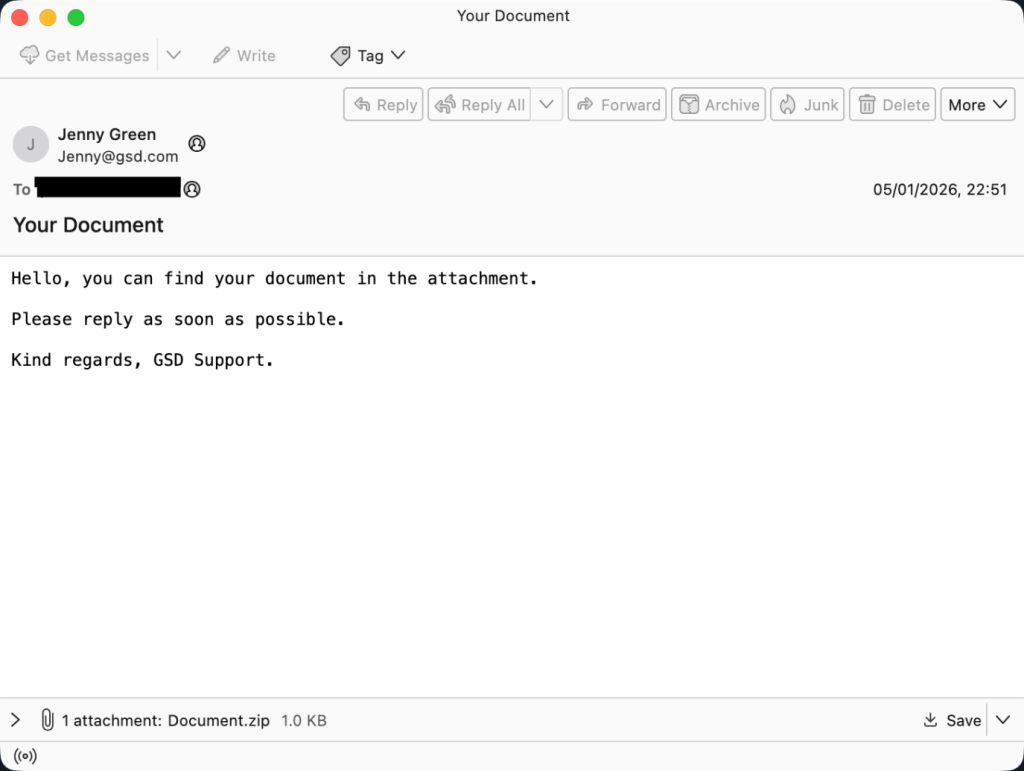
This marketing campaign, lively all through 2024 and 2025, begins with a plain e-mail. The topic line often reads “Your Doc,” a phrase designed to make you curious or fearful sufficient to click on. Inside is an attachment or a Zip folder, usually named Doc.doc.lnk. Hackers use a double extension right here as a result of Home windows usually hides the final a part of a file title. To a standard particular person, it simply appears like Doc.doc, however additional probing revealed it’s really a Home windows Shortcut file (.lnk).
As soon as clicked, the shortcut quietly tells your laptop to run background instructions utilizing a way referred to as Residing off the Land (LotL). As a substitute of bringing its personal suspicious instruments, it hijacks your laptop’s “wholesome” applications, like PowerShell and Command Immediate, to do its soiled work. These instructions obtain the precise virus, which hides in system folders below names like windrv.exe to appear like a professional Home windows half.
The Ransomware That Works in Silence
The analysis, shared with Hackread.com, identifies the ultimate payload as World Group, a successor to the older Mamona ransomware. What makes this model troublesome is its “mute” mode. Not like most viruses that “name house” to the web for directions, World Group does all the things regionally.
“The ransomware doesn’t retrieve an exterior encryption key; as a substitute, it generates the important thing on the host machine itself,” researchers famous within the weblog submit revealed at present.
As a result of it doesn’t want a server connection, it could actually lock information even on offline computer systems. Additional investigation revealed it makes use of a robust locking system referred to as ChaCha20-Poly1305, making it practically unimaginable to get better information with out the legal’s digital key.
Wiping the Proof
This virus is a “clear” legal. To hinder investigators, it makes use of a ping command to the handle 127.0.0.7 as a three-second timer. As soon as completed, it deletes its personal information out of your onerous drive to go away much less proof behind.
Researchers discovered that the virus even hunts in your backups. It quietly deletes Quantity Shadow Copies, the “security web” information used to revive knowledge. As soon as completed, your paperwork can have a .Reco extension, and your wallpaper will likely be changed with a ransom notice.
This marketing campaign reveals that hackers don’t all the time want complicated know-how to entice customers; typically, they only want a easy shortcut and a convincing e-mail. Utilizing widespread sense is vital. Don’t open unsolicited emails, click on hyperlinks they comprise, or obtain and run any hooked up information.