Lengthy recognized to be a candy spot for cybercriminals, small companies usually tend to be victimized by ransomware than giant enterprises
18 Sep 2025
•
,
5 min. learn

Suppose what you are promoting is just too small to be singled out for digital extortion? Suppose once more. Certainly, when you’re an SMB proprietor, you’d higher assume you’re a possible goal. Verizon information reveals that, whereas ransomware includes 39% of knowledge breaches at giant organizations, the determine rises to 88% for SMBs. Giant enterprises could also be extra ready to pay multimillion-dollar ransoms, however they’re usually additionally extra more likely to have the instruments and insurance policies in place to stop, detect and include breach danger.
In the meantime, SMB are, very similar to giant firms, totally depending on their information and IT infrastructure to function. The specter of everlasting information loss and a complete enterprise shutdown has usually been a strong motivator for paying the ransom payment, even with none assure that the enterprise will truly get its information again.
Making issues worse, attackers all the time search for extra levers to power cost, for instance by way of double-extortion assaults the place they each steal delicate information and encrypt and threaten to publish it. Other than stealing and threatening to leak or wipe delicate inner information, they may threaten DDoS assaults, regulatory complaints and, oddly sufficient, even bodily violence in some instances. In reality, attackers even fortunately regulate their ransom calls for to extend the chances of a cost, as discovered by Verizon.
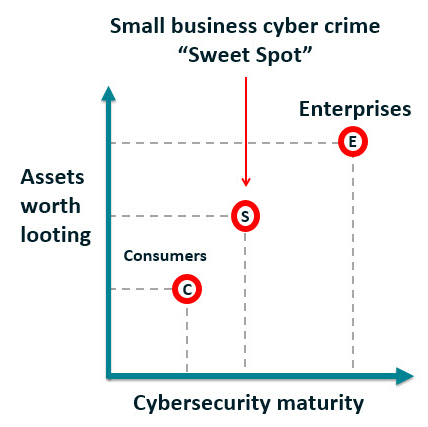
To place it bluntly, less-well defended SMBs are a juicy goal for attackers. Certainly, by having extra digital property and cash than shoppers and fewer cybersecurity protections than enterprises, these companies have for lengthy been in a “cybercrime candy spot”. In case you’re eager to maintain your organization’s information protected and methods safe, the excellent news is that it’s achievable with out breaking the financial institution.
How ransomware teams are evolving
To deal with the risk, you additionally want to know who or what’s driving it, and the way it’s altering. For one factor, the ransomware-as-a-service (RaaS) industrialization of cybercrime has lowered the boundaries to entry and facilitated the proliferation of ransomware. In the meantime, the turnover of ransomware manufacturers additionally continues apace, triggered partially by intensifying regulation enforcement efforts. As quickly as a gaggle is taken down, a brand new one usually emerges with related or different techniques and instruments in a bid to flee scrutiny. Moreover, fast-evolving TTPs make it more durable to mitigate danger.
Then again, ransomware rebrands may be a mirrored image of the difficulties many teams are having in turning a revenue. An evaluation of cryptocurrency ransom funds reveals a 35% lower between 2023 and 2024. But confronted with probably fewer victims prepared to pay, ransomware teams look like doubling down on those that do, as proven by a examine claiming that 55% of organizations that paid a ransom final 12 months did so a number of instances; with 29% paying three or extra instances.
How AI is remodeling ransomware
As expertise advances, ransomware teams are additionally altering tack to extend their possibilities of success. The standard methods to realize preliminary entry into sufferer networks stay vulnerability exploitation, phishing and distant entry compromise; equivalent to by way of credentials obtained by infostealer malware. But AI instruments might supercharge all of those efforts.
The UK’s Nationwide Cyber Safety Centre (NCSC) warned lately that over the following two years AI use will result in “a rise in frequency and depth of cyber threats.” Scanning for weak victims (reconnaissance), vulnerability exploitation, and social engineering particularly will change into extra democratized on the cybercrime underground.
In the meantime, ESET lately found what’s believed to be the world’s first AI-powered ransomware, “PromptLock.” It makes use of a professional mannequin from OpenAI to generate malicious scripts. “The prospect of AI-powered malware that may, amongst different issues, adapt to the surroundings and alter its techniques on the fly could usually symbolize a brand new frontier in cyberattacks,” ESET warns.
A separate ESET report highlights different new developments together with the looks of “EDR killers” – designed to terminate, blind, or crash endpoint detection and response (EDR) tooling put in on sufferer methods. Teams have additionally been noticed utilizing “ClickFix” social engineering techniques to trick customers into putting in malware on their machines.
shield what you are promoting
A handful of SMBs know to their price what can occur following a ransomware breach. Though already underneath monetary strain earlier than a 2023 assault, British logistics agency KNP subsequently fell into administration with the lack of 700 jobs.
To forestall what you are promoting going the identical means, undertake a prevention-first mindset by:
- Deploying sturdy patch administration to make sure vulnerabilities deemed the best danger are patched, to additional restrict the chance for preliminary entry and lateral motion.
- Updating identification and entry administration insurance policies and tooling consistent with a Zero Belief strategy. This implies assuming breach, steady verification of customers, least privilege insurance policies, and multi-factor authentication.
- Guaranteeing safety software program from a trusted vendor is positioned on all gadgets, from endpoints, servers to distant employee laptops.
- Backing up delicate information in keeping with business finest practices, in order that even when information are encrypted they are often restored, lowering your adversary’s leverage.
- Devising an incident response plan in collaboration with key stakeholders from throughout the enterprise. It also needs to be examined periodically to make sure it’s match for objective in serving to to speed up containment following an intrusion.
- Repeatedly monitoring your networks, endpoints and different components of the IT surroundings for indicators of suspicious conduct. These early warning indicators ought to assist to attenuate attacker dwell time.
- Updating coaching and consciousness programs to incorporate simulation workout routines that includes the newest phishing techniques, together with voice-based phishing (vishing). Your staff are each your finest asset and your weakest hyperlink.
Importantly, make certain to correctly consider your property, assets and dangers, together with these emanating from provide chains. Maintain a list of all open-source and proprietary off-the-shelf instruments utilized by your group. Extra broadly, asset visibility is the inspiration of any danger administration program. In different phrases, attackers are recognized to rely on blind spots. In case you don’t know a system exists or what information it holds, you may’t shield it.
Because the ESET SMB Digital Safety Sentiment 2022 has proven, many SMBs are more and more conscious of ransomware and different dangers going through their enterprise, however they don’t have the boldness of their in-house cybersecurity experience. It is smart then that a lot of them, particularly these with fewer assets, are more and more turning to managed detection and response (MDR) providers to and hand off the monitoring to an skilled accomplice who then performs 24/7/365 risk searching, detection and response, lowering the operational burden in your in-house workforce whereas guaranteeing any ransomware exercise is quickly recognized, contained and eradicated. Ransomware actors have to be despatched packing earlier than they’ve an opportunity to trigger any injury.