Earlier than dashing to show that you simply’re not a robotic, be cautious of misleading human verification pages as an more and more standard vector for delivering malware
24 Jul 2025
•
,
4 min. learn
Bots have gotten so much to reply for. They now make up over half of all web site visitors, and whereas some, equivalent to Google’s net crawlers and fetchers, have reputable functions, practically two-fifths are thought of malicious. Their energy could be harnessed for the whole lot from posting inflammatory social media posts to launching distributed denial-of-service assaults and hijacking on-line accounts utilizing, for instance, beforehand breached passwords.
So after we’re introduced with what’s often known as a CAPTCHA problem, which web sites generally use to discourage bots, many people comply with the directions and click on via. All the higher to maintain the bots out, proper? Properly, not all the time. Generally the web page itself is a faux and will land you in serious trouble.
This might, for instance, be the case with ClickFix, a social engineering method that has taken the menace panorama by storm just lately. Utilizing faux CAPTCHA photographs, ClickFix spreads all method of threats, together with infostealers, ransomware, distant entry trojans, cryptominers, and even malware from nation-state-aligned menace actors.
Why the CAPTCHA menace works
CAPTCHA threats work for a number of causes:
- It exploits our familiarity with the method and our belief in CAPTCHA as a method to preserve the digital world secure and safe.
- It additionally exploits the truth that many people are impatient after we’re shopping: we simply need to entry the content material we got here for and CAPTCHA is in our manner, therefore we’re extra prone to do what it says.
- It takes benefit of the actual fact we’re used to clicking via a number of steps to confirm ourselves on-line; for instance when paying on-line.
- It hides the malicious exercise from us, and our safety software program, and makes use of reputable Home windows instruments to remain underneath the radar.
What do CAPTCHA threats appear like?
There are numerous methods it’s possible you’ll be uncovered to a malicious CAPTCHA. It could be that you’re tricked into clicking on a malicious hyperlink in a phishing electronic mail, textual content or social media message. Due to AI, this menace is rising. Generative AI helps menace actors to scale social engineering assaults whereas bettering the standard of the language to near-perfect, in a number of languages without delay.
Alternatively, it’s possible you’ll go to a random, reputable website that hackers have injected malicious advertisements or different content material into. These are significantly harmful as no person interplay is required for the obtain. And it’s possible you’ll not understand that something untoward has occurred till it’s too late.
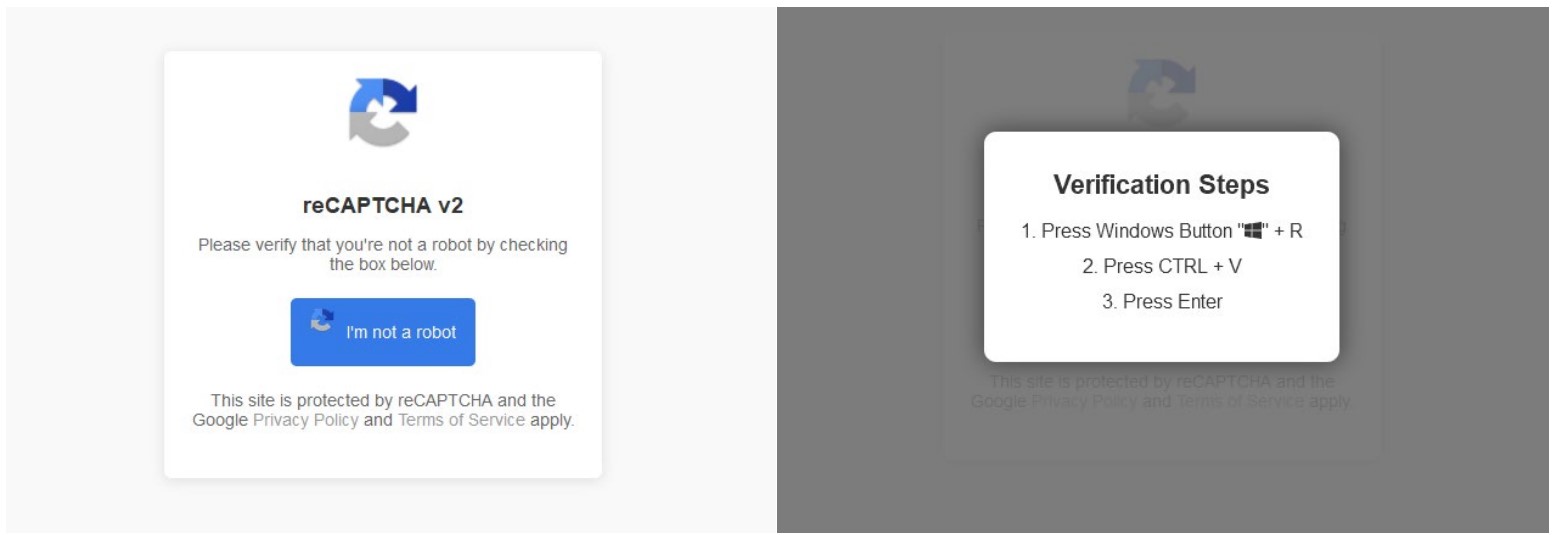
When the CAPTCHA field pops up it should look reputable sufficient. However what it asks you to do ought to set alarm bells ringing. As an alternative of the standard CAPTCHA job, like figuring out related photographs or typing textual content that has been obfuscated indirectly, it should ask you to carry out particular instructions like:
- Clicking via to confirm you’re a human
- Urgent Home windows key + R to open “Run”
- Urgent CTRL + V to stick a command secretly copied to the clipboard by the malware
- Urgent ENTER to execute the above command
This command usually triggers reputable Home windows instruments like PowerShell or mshta.exe to obtain extra malicious payloads from an exterior server. The tip purpose is often to put in infostealer malware in your system.
Infostealers are designed to scour the pc or cell phone for logins, photographs, contacts, and different delicate information to promote on the darkish net and/or use to commit id fraud. They aim browsers, electronic mail purchasers, crypto wallets, apps and the working techniques itself to take action – taking screenshots, keylogging and harvesting information in different methods.
In line with one research, there have been a minimum of 23 million infostealer victims in 2024, most of which had been Home windows techniques. They managed to steal over two billion sufferer credentials. Probably the most standard strains of infostealing malware, Lumma Stealer, compromised as many as 10 million units earlier than an worldwide effort, which concerned additionally ESET, disrupted this prolific malware-as-a-service (MaaS) menace.
A CAPTCHA menace may additionally set up a distant entry trojan (RAT), one other kind of malware however this time designed to offer distant entry to your machine. In line with one research, AsyncRAT was seen in 4% of incidents throughout 2024. This RAT has been operational since 2019 and carries out actions together with like information theft and keylogging.
Staying secure from CAPTCHA threats
To remain secure from infostealers, RATs and different nasties, contemplate the next:
- Keep alert to uncommon CAPTCHA requests like those listed above.
- Be cautious of any CAPTCHA problem that appears to pop up out of nowhere.
- Preserve your OS and browser software program updated, to reduce the danger of malware exploiting vulnerabilities in older variations.
- Set up safety software program from a good vendor and preserve it up to date. It will go a good distance towards blocking any malware or suspicious exercise.
- Don’t obtain pirated software program, as this might include malware of the kind that delivers faux CAPTCHAs.
- Think about using an advert blocker, which might cease you from being uncovered to any content material delivered by way of a malicious on-line advert.
What occurs for those who fall for a faux CAPTCHA
If the worst occurs and also you unwittingly execute the hidden instructions described above:
- Run a malware scan to search out and hopefully purge the machine of any malware that will have been covertly downloaded.
- Disconnect from the web and backup any essential photographs and/or information.
- Carry out a manufacturing facility reset in your pc or system.
- Change all of your passwords, utilizing sturdy, distinctive credentials saved in a password supervisor.
- Swap on multi issue authentication (MFA) for all accounts, in order that even when a hacker has stolen your passwords they’ll’t entry your accounts.
Falling for a CAPTCHA menace isn’t the top of the world. But it surely pays to behave quick if you end up in a worst-case situation. Be secure on the market.












