A collaborative effort by worldwide cybersecurity companies, together with the Nationwide Safety Company (NSA), Cybersecurity and Infrastructure Safety Company (CISA), Federal Bureau of Investigation (FBI), Australian Alerts Directorate’s Australian Cyber Safety Centre (ASD’s ACSC), Canadian Centre for Cyber Safety (CCCS), and New Zealand Nationwide Cyber Safety Centre (NCSC-NZ), has highlighted a vital safety difficulty often known as Quick Flux.
In line with a joint advisory, each cybercriminals and state-sponsored actors are exploiting this new approach, which permits them to hide malicious server places and preserve persistent command and management (C2) infrastructure and has been declared a nationwide safety menace.
Understanding quick flux
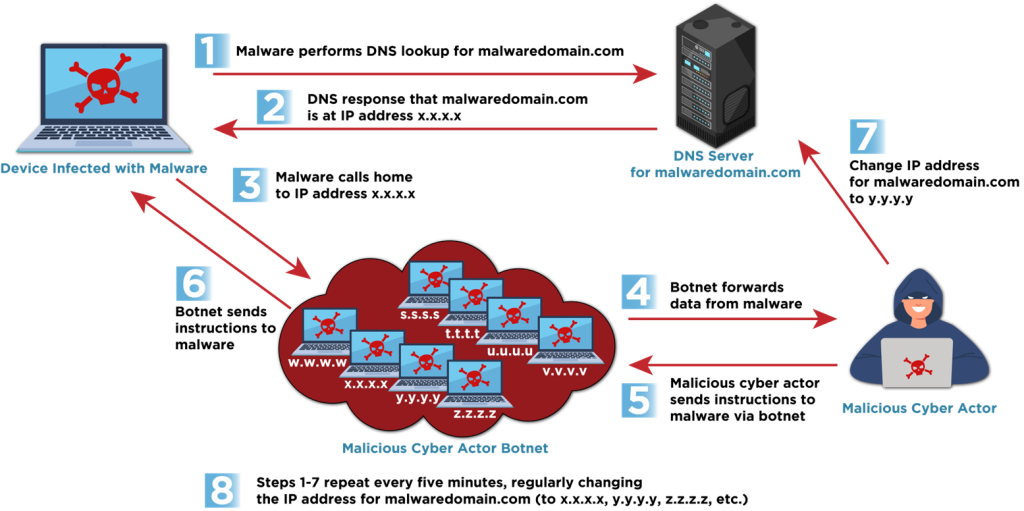
Quick flux’s core mechanism lies within the dynamic manipulation of Area Identify System (DNS) data. By quickly altering the IP addresses related to a single area, attackers successfully obfuscate the true location of their malicious servers. This speedy rotation renders conventional IP-based blocking strategies ineffective, because the goal IP deal with turns into out of date virtually instantly.
Analysis reveals that cybercriminals are using two strategies of quick flux- Single flux and Double flux. Single flux includes linking a single area title to quite a few, incessantly rotated IP addresses, making certain that even when one IP is blocked, the area stays accessible.
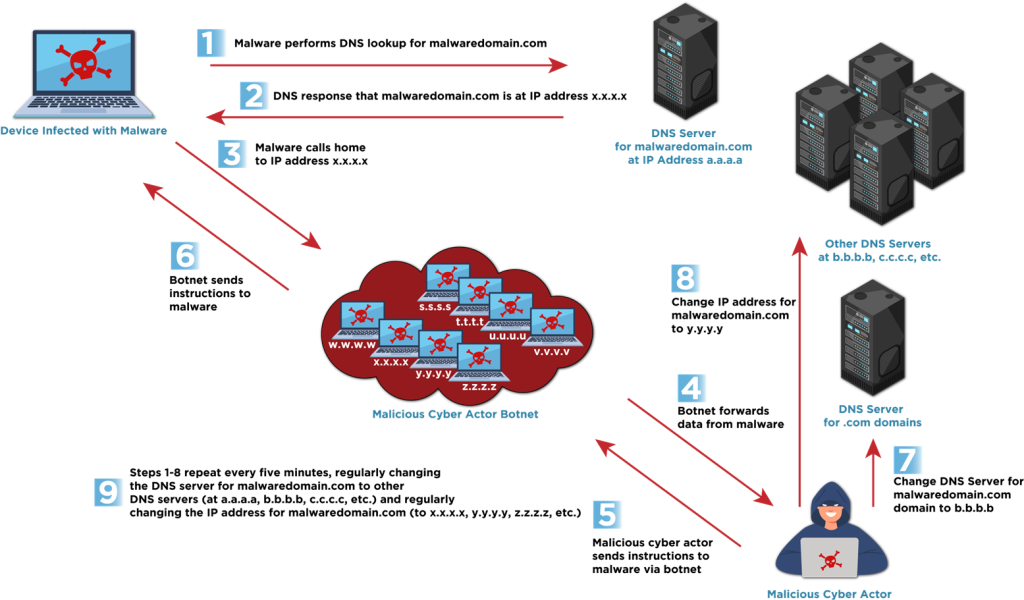
Conversely, Double flux additional enhances this obfuscation by additionally incessantly altering the DNS title servers liable for resolving the area, including one other layer of anonymity.
“These strategies leverage a lot of compromised hosts,” CISA notes, usually forming botnets, which act as proxies to cover the malicious visitors’s origin.
Malicious Purposes and the Function of Bulletproof Internet hosting
CISA emphasizes that Quick Flux shouldn’t be solely used for sustaining C2 communications. It performs a big function in phishing campaigns, making social engineering web sites tough to take down.
Moreover, “bulletproof internet hosting” (BPH) suppliers, who disregard legislation enforcement requests, are more and more providing it as a service to their shoppers. This enables for the seamless operation of malicious actions like botnet administration, faux on-line retailers, and credential theft, all whereas offering a layer of safety in opposition to detection and takedown, and has been utilized in Hive and Nefilim ransomware assaults. One BPH supplier even marketed the service’s capacity to bypass Spamhaus blocklists, highlighting its attraction to cybercriminals.
Detection and Mitigation
The companies strongly suggest a multi-layered strategy to detect and mitigate “quick flux” assaults. This contains leveraging menace intelligence feeds, implementing anomaly detection for DNS question logs, analyzing DNS file time-to-live (TTL) values, monitoring for inconsistent geolocation, and utilizing move knowledge to determine uncommon communication patterns.
For organizations, companies suggest DNS and IP blocking, reputational filtering, enhanced monitoring and logging, and phishing consciousness coaching as potent mitigation methods. It’s essential for organizations to coordinate with their Web service suppliers and cybersecurity suppliers, notably Protecting DNS (PDNS) suppliers, to implement these measures, the advisory concludes.
John DiLullo, CEO at Deepwatch, a San Francisco, Calif.-based AI+Human Cyber Resilience Platform, commented on the newest improvement, stating: This newest advisory will hit many organizations like a double espresso. Any enterprise counting on IP status as a reputable technique of securing their infrastructure or proprietary knowledge is a comfortable goal for such a exploit.”
“Luckily, correlative detection strategies, particularly these leveraging ‘low and gradual’ Machine Studying strategies, can defeat these intrusions handily. Nonetheless, many corporations’ infrastructures merely aren’t there but. This can be a important wake-up name,” he warned.