KrebsOnSecurity lately heard from a reader whose boss’s e-mail account received phished and was used to trick one of many firm’s clients into sending a big cost to scammers. An investigation into the attacker’s infrastructure factors to a long-running Nigerian cybercrime ring that’s actively focusing on established firms within the transportation and aviation industries.

Picture: Shutterstock, Mr. Teerapon Tiuekhom.
A reader who works within the transportation business despatched a tip a couple of current profitable phishing marketing campaign that tricked an government on the firm into coming into their credentials at a faux Microsoft 365 login web page. From there, the attackers rapidly mined the chief’s inbox for previous communications about invoices, copying and modifying a few of these messages with new bill calls for that have been despatched to a few of the firm’s clients and companions.
Talking on situation of anonymity, the reader mentioned the ensuing phishing emails to clients got here from a newly registered area title that was remarkably just like their employer’s area, and that at the very least certainly one of their clients fell for the ruse and paid a phony bill. They mentioned the attackers had spun up a look-alike area only a few hours after the chief’s inbox credentials have been phished, and that the rip-off resulted in a buyer struggling a six-figure monetary loss.
The reader additionally shared that the e-mail addresses within the registration information for the imposter area — roomservice801@gmail.com — is tied to many such phishing domains. Certainly, a search on this e-mail handle at DomainTools.com finds it’s related to at the very least 240 domains registered in 2024 or 2025. Nearly all of them mimic respectable domains for firms within the aerospace and transportation industries worldwide.
An Web seek for this e-mail handle reveals a humorous weblog submit from 2020 on the Russian discussion board hackware[.]ru, which discovered roomservice801@gmail.com was tied to a phishing assault that used the lure of phony invoices to trick the recipient into logging in at a faux Microsoft login web page. We’ll come again to this analysis in a second.
JUSTY JOHN
DomainTools reveals that a few of the early domains registered to roomservice801@gmail.com in 2016 embrace different helpful info. For instance, the WHOIS information for alhhomaidhicentre[.]biz reference the technical contact of “Justy John” and the e-mail handle justyjohn50@yahoo.com.
A search at DomainTools discovered justyjohn50@yahoo.com has been registering one-off phishing domains since at the very least 2012. At this level, I used to be satisfied that some safety firm absolutely had already printed an evaluation of this explicit menace group, however I didn’t but have sufficient info to attract any stable conclusions.
DomainTools says the Justy John e-mail handle is tied to greater than two dozen domains registered since 2012, however we will discover a whole lot extra phishing domains and associated e-mail addresses just by pivoting on particulars within the registration information for these Justy John domains. For instance, the road handle utilized by the Justy John area axisupdate[.]web — 7902 Pelleaux Street in Knoxville, TN — additionally seems within the registration information for accountauthenticate[.]com, acctlogin[.]biz, and loginaccount[.]biz, all of which at one level included the e-mail handle rsmith60646@gmail.com.
That Rsmith Gmail handle is related to the 2012 phishing area alibala[.]biz (one character off of the Chinese language e-commerce large alibaba.com, with a distinct top-level area of .biz). A search in DomainTools on the telephone quantity in these area information — 1.7736491613 — reveals much more phishing domains in addition to the Nigerian telephone quantity “2348062918302” and the e-mail handle michsmith59@gmail.com.
DomainTools reveals michsmith59@gmail.com seems within the registration information for the area seltrock[.]com, which was used within the phishing assault documented in the 2020 Russian weblog submit talked about earlier. At this level, we’re simply two steps away from figuring out the menace actor group.
The identical Nigerian telephone quantity reveals up in dozens of area registrations that reference the e-mail handle sebastinekelly69@gmail.com, together with 26i3[.]web, costamere[.]com, danagruop[.]us, and dividrilling[.]com. A Internet search on any of these domains finds they have been listed in an “indicator of compromise” listing on GitHub maintained by Palo Alto Networks‘ Unit 42 analysis staff.
SILVERTERRIER
In response to Unit 42, the domains are the handiwork of an enormous cybercrime group primarily based in Nigeria that it dubbed “SilverTerrier” again in 2014. In an October 2021 report, Palo Alto mentioned SilverTerrier excels at so-called “enterprise e-mail compromise” or BEC scams, which goal respectable enterprise e-mail accounts by social engineering or pc intrusion actions. BEC criminals use that entry to provoke or redirect the switch of enterprise funds for private achieve.
Palo Alto says SilverTerrier encompasses a whole lot of BEC fraudsters, a few of whom have been arrested in numerous worldwide legislation enforcement operations by Interpol. In 2022, Interpol and the Nigeria Police Drive arrested 11 alleged SilverTerrier members, together with a distinguished SilverTerrier chief who’d been flaunting his wealth on social media for years. Sadly, the lure of simple cash, endemic poverty and corruption, and low limitations to entry for cybercrime in Nigeria conspire to supply a relentless stream of recent recruits.
BEC scams have been the seventh most reported crime tracked by the FBI’s Web Crime Criticism Heart (IC3) in 2024, producing greater than 21,000 complaints. Nevertheless, BEC scams have been the second most expensive type of cybercrime reported to the feds final yr, with almost $2.8 billion in claimed losses. In its 2025 Fraud and Management Survey Report, the Affiliation for Monetary Professionals discovered 63 % of organizations skilled a BEC final yr.
Poking at a few of the e-mail addresses that spool out from this analysis reveals numerous Fb accounts for folks residing in Nigeria or within the United Arab Emirates, a lot of whom don’t seem to have tried to masks their real-life identities. Palo Alto’s Unit 42 researchers reached an analogous conclusion, noting that though a small subset of those crooks went to nice lengths to hide their identities, it was normally easy to be taught their identities on social media accounts and the key messaging providers.
Palo Alto mentioned BEC actors have turn out to be much more organized over time, and that whereas it stays simple to search out actors working as a gaggle, the observe of utilizing one telephone quantity, e-mail handle or alias to register malicious infrastructure in help of a number of actors has made it much more time consuming (however not unimaginable) for cybersecurity and legislation enforcement organizations to kind out which actors dedicated particular crimes.
“We proceed to search out that SilverTerrier actors, no matter geographical location, are sometimes related by only some levels of separation on social media platforms,” the researchers wrote.
FINANCIAL FRAUD KILL CHAIN
Palo Alto has printed a helpful listing of suggestions that organizations can undertake to reduce the incidence and influence of BEC assaults. Lots of these ideas are prophylactic, equivalent to conducting common worker safety coaching and reviewing community safety insurance policies.
However one advice — getting acquainted with a course of generally known as the “monetary fraud kill chain” or FFKC — bears particular point out as a result of it gives the only finest hope for BEC victims who’re in search of to claw again funds made to fraudsters, and but far too many victims don’t understand it exists till it’s too late.
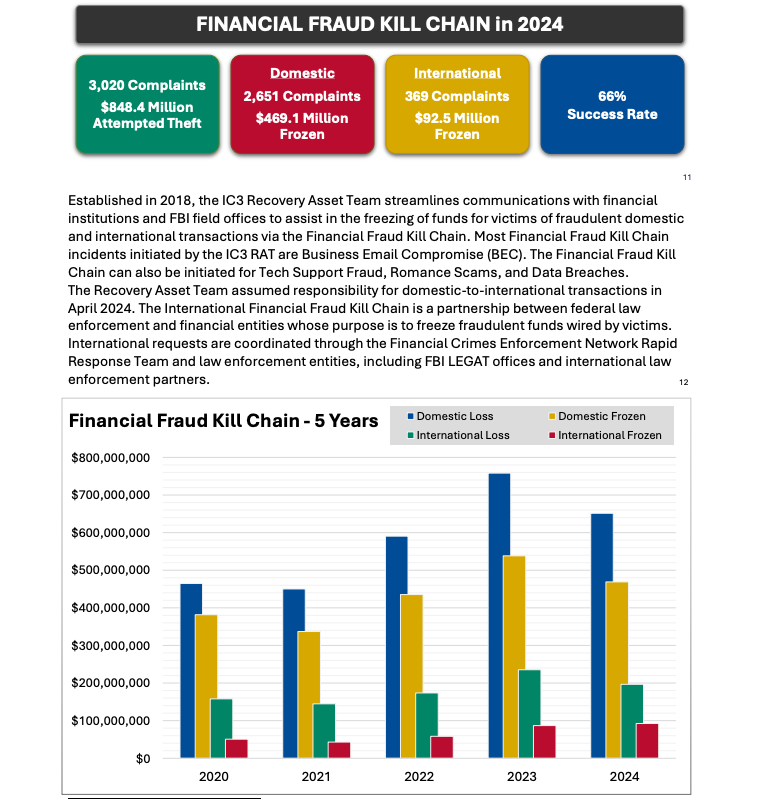
Picture: ic3.gov.
As defined in this FBI primer, the Worldwide Monetary Fraud Kill Chain is a partnership between federal legislation enforcement and monetary entities whose goal is to freeze fraudulent funds wired by victims. In response to the FBI, viable sufferer complaints filed with ic3.gov promptly after a fraudulent switch (typically lower than 72 hours) will likely be robotically triaged by the Monetary Crimes Enforcement Community (FinCEN).
The FBI famous in its IC3 annual report (PDF) that the FFKC had a 66 % success price in 2024. Viable ic3.gov complaints contain losses of at the very least $50,000, and embrace all information from the sufferer or sufferer financial institution, in addition to a accomplished FFKC kind (offered by FinCEN) containing sufferer info, recipient info, financial institution names, account numbers, location, SWIFT, and any extra info.










