The extensions share different doubtful or suspicious similarities. A lot of the code in every one is very obfuscated, a design selection that gives no profit aside from complicating the method for analyzing and understanding the way it behaves.
All however one among them are unlisted within the Chrome Net Retailer. This designation makes an extension seen solely to customers with the lengthy pseudorandom string within the extension URL, and thus, they don’t seem within the Net Retailer or search engine search outcomes. It’s unclear how these 35 unlisted extensions might have fetched 4 million installs collectively, or on common roughly 114,000 installs per extension, once they had been so onerous to search out.
Moreover, 10 of them are stamped with the “Featured” designation, which Google reserves for builders whose identities have been verified and “observe our technical greatest practices and meet a excessive customary of person expertise and design.”
One instance is the extension Fireplace Defend Extension Safety, which, sarcastically sufficient, purports to verify Chrome installations for the presence of any suspicious or malicious extensions. One of many key JavaScript recordsdata it runs references a number of questionable domains, the place they’ll add knowledge and obtain directions and code:
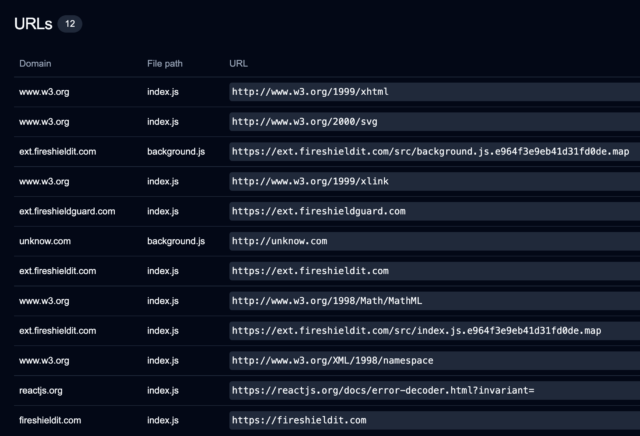
URLs that Fireplace Defend Extension Safety references in its code.
Credit score:
Safe Annex
One area particularly—unknow.com—is listed within the remaining 34 apps.
Tuckner tried analyzing what extensions did on this website however was largely thwarted by the obfuscated code and different steps the developer took to hide their conduct. When the researcher, as an example, ran the Fireplace Defend extension on a lab machine, it opened a clean webpage. Clicking on the icon of an put in extension often offers an possibility menu, however Fireplace Defend displayed nothing when he did it. Tuckner then fired up a background service employee within the Chrome developer instruments to hunt clues about what was occurring. He quickly realized that the extension related to a URL at fireshieldit.com and carried out some motion below the generic class “browser_action_clicked.” He tried to set off further occasions however got here up empty-handed.










