Russian APT group Storm-2372 employs gadget code phishing to bypass Multi-Issue Authentication (MFA). Targets embrace authorities, know-how, finance, protection, healthcare.
Cybersecurity researchers at SOCRadar have found a brand new assault tactic utilized by the infamous Russian state-backed superior persistent menace (APT), Storm-2372. In accordance with SOCRadar’s analysis, shared with Hackread.com, Storm-2372 can now break into on-line accounts of main organizations with out attempting to guess passwords.
That is achieved by a technique known as “gadget code phishing,” which helps them get round even sturdy safety measures like Multi-Issue Authentication (MFA).
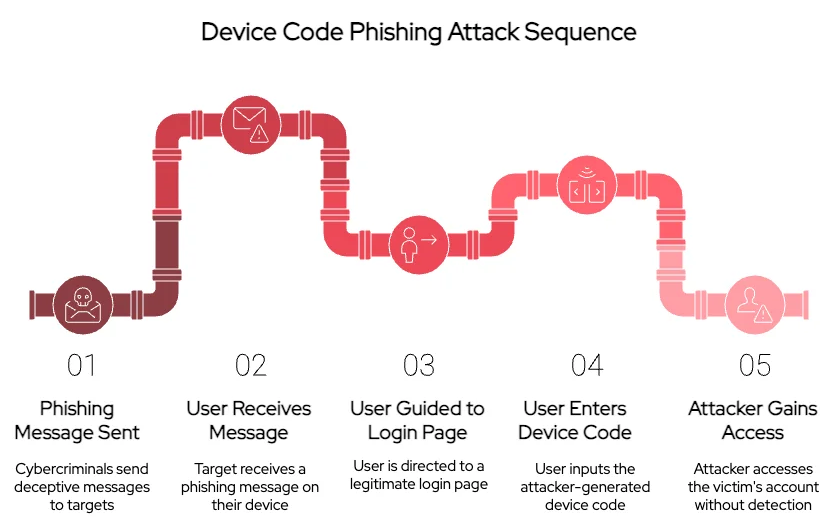
Machine Code Phishing takes benefit of the best way some gadgets, like sensible TVs, hook up with on-line companies. Normally, these gadgets offer you a particular code that you simply kind into a web site in your laptop or telephone to log in (OAuth gadget authorization move). Hackers are utilizing this similar course of to idiot individuals into giving them entry to their work accounts.
Right here’s the way it works
The hackers ship faux messages, usually by e mail or textual content, telling individuals they should use a tool code to log in. These messages direct them to real-looking login pages, like those from Microsoft. The victims then unknowingly kind in a code that the hackers have created. As soon as the individual enters the code, the hackers can get into their account without having a password or triggering the standard safety checks. This makes it a lot more durable to identify the assault because the victims don’t understand they’ve been compromised till it’s too late.
Beforehand, the strategy OG Machine Code Phishing was utilized by hackers to create a tool code utilizing particular instruments and despatched it through message. Nonetheless, these codes solely lasted about quarter-hour, making it tough for hackers to log in if the individual didn’t see the message.
Storm-2372 employs the extra superior Dynamic Machine Code Phishing approach, beforehand documented by Black Hills in 2023, to create faux web sites resembling actual login pages utilizing companies like Azure Net Apps. When a person visits these faux websites, they generate a brand new gadget code, permitting hackers to log in. They generally use CORS-Wherever to show the code accurately within the person’s browser. When the person enters the faux code, they obtain entry tokens and refresh tokens, permitting hackers to entry Microsoft e mail for as much as three months.
Storm-2372 is, reportedly, concentrating on organizations that maintain precious info and make vital selections. This contains authorities businesses, know-how corporations, banks, defence contractors, healthcare suppliers, and media corporations. They’ve been seen attacking organizations in nations like the US, Ukraine, the UK, Germany, Canada, and Australia.
This new trick reveals that these hackers are getting higher at fooling individuals to get previous even good safety programs, and firms want to search out smarter methods to guard themselves from such sneaky assaults.
“The marketing campaign underlines the essential want for contemporary organizations to embrace adaptive, context-aware protection mechanisms to counter identity-based threats which are more and more evading standard protections,” researchers concluded.