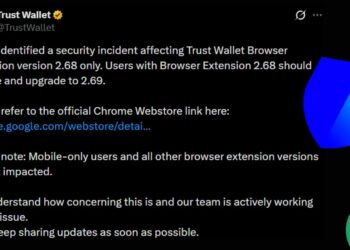
Lazarus Hackers Goal European Drone Producers in Energetic Marketing campaign
The North Korean state-sponsored Lazarus hacking group has launched a classy cyberespionage marketing campaign concentrating on European protection contractors concerned ...