If in case you have ever obtained a boring electronic mail a couple of enterprise contract or a ‘request order,’ you may need clicked it with out pondering twice. However a brand new report means that these routine messages at the moment are a part of a deliberate rip-off.
Cybersecurity researchers at Forcepoint have found a brand new phishing rip-off during which attackers are utilizing a “multi-stage” course of to remain invisible and obtain their true aim of stealing your login particulars.
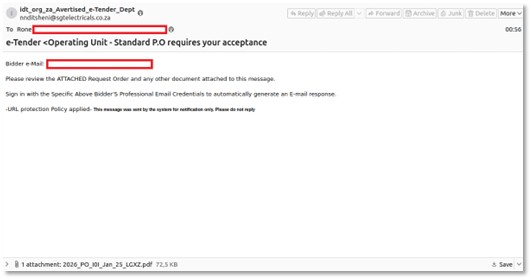
Most electronic mail scams are caught by filters as a result of they include malicious hyperlinks or viruses. This one is completely different. It begins with a professional-looking electronic mail, often a couple of “tender” or “procurement” deal. The e-mail itself is totally clear. It depends on a PDF attachment to do the soiled work.
In response to X-Labs’ investigation, shared with Hackread.com, these PDFs use technical settings like AcroForms and FlateDecode. Merely put, this permits the scammers to cover clickable buttons inside a doc that appears like a traditional workplace file. As a result of we usually belief PDFs greater than hyperlinks in an electronic mail, the attackers are banking on that.
A well-coordinated rip-off
As soon as a consumer clicks the hyperlink contained in the PDF, they’re despatched to a second doc. This second file is hosted on Vercel Blob storage, a authentic cloud service. Kumar notes within the weblog submit that by utilizing a “trusted cloud infrastructure,” the scammers handle to bypass safety software program that often blocks unknown or suspicious web sites.
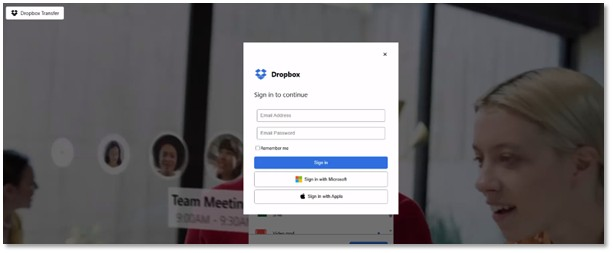
This cloud-hosted file lastly leads victims to a pretend Dropbox login web page, which is designed to look precisely like the actual factor. Nevertheless, behind the scenes, a script is working to steal your electronic mail, password, and your precise IP handle. It even logs your location, together with your metropolis and nation, and the kind of system you’re utilizing.
The place the Knowledge Goes
So, what occurs to your password? The analysis reveals that the stolen knowledge is distributed on to a personal channel on Telegram.
“The script is designed to seize consumer credentials,” Kumar explains, earlier than sending them to a “hardcoded” Telegram bot managed by the hackers. To maintain the sufferer at the hours of darkness, the pretend web site is about as much as at all times present an error message, making you assume you simply typed your password unsuitable whereas the hackers are already strolling away along with your knowledge.
Whereas Forcepoint has up to date its programs to dam these information, it’s a great reminder for the remainder of us: if a enterprise doc instantly asks for a login, it is likely to be time to double-check the sender.