Your iPhone is not essentially as invulnerable to safety threats as chances are you’ll assume. Listed below are the important thing risks to be careful for and the best way to harden your system in opposition to dangerous actors.
28 Apr 2025
•
,
6 min. learn

Chances are high excessive that many individuals assume, “it’s an iPhone, so I’m secure”. Apple’s management over its system and app ecosystem has certainly traditionally been tight, with its walled-garden method offering fewer alternatives for hackers to seek out weak spots. There are additionally numerous built-in safety features like robust encryption and containerization, the latter serving to forestall information leakage and restrict the unfold of malware. And passkey-based logins and numerous privacy-by-default settings additionally assist.
The truth that iOS apps are usually sourced from the official Apple App Retailer and should cross stringent exams to be accredited for itemizing has spared many iPhone customers some safety and privateness complications over time. Then again, it doesn’t remove the dangers fully, with all method of on a regular basis scams and different threats bombarding not simply Android, however to some extent additionally iOS customers. Whereas some are extra widespread than others, all demand consideration.
In the meantime, the EU’s latest monopoly-busting regulation referred to as the Digital Markets Act (DMA) goals to make sure a stage enjoying discipline by providing iOS customers the selection of utilizing third-party app marketplaces. The landmark transfer introduces new challenges for Apple with regards to safeguarding iOS customers from hurt and can also have implications for a lot of customers themselves, as they may must be extra aware of safety threats lurking round. There’s each purpose to imagine that dangerous actors will try and co-opt the transfer for nefarious ends.
So as to adjust to the DMA, Apple should permit:
- Builders to supply iOS apps to customers through non-App Retailer marketplaces. This might enhance the possibilities of customers downloading malicious apps. Even reliable apps will not be up to date as steadily as official App Retailer ones.
- Third-party browser engines, which can supply new alternatives for assault that Apple’s WebKit engine doesn’t (verify).
- Third-party system producers and app builders to entry numerous iOS connectivity options, like peer-to-peer Wi-Fi connectivity and system pairing. The tech large argues this implies it could be compelled to ship delicate consumer information together with notifications containing private messages, Wi-Fi community particulars or one-time codes, to those builders. They may theoretically use the data to trace customers, it warns.
The place else iOS threats are lurking
Whereas the above could “solely” impression EU residents, there are additionally different and presumably extra speedy considerations for iOS customers worldwide. These embrace:
Jailbroken units
In case you intentionally unlock your system to permit what Apple calls “unauthorized modifications”, it would violate your Software program License Settlement and will disable some built-in safety features like embrace Safe Boot and Information Execution Prevention. It should additionally imply your system now not receives automated updates. And by having the ability to obtain apps from past the App Retailer, you’ll be uncovered to malicious and/or buggy software program.
Malicious apps
Whereas Apple does job of vetting apps, it doesn’t get it proper 100% of the time. Malicious apps detected on the App Retailer not too long ago embrace:
Web site-based app downloads
You additionally must watch out for downloading iOS apps direct from web sites with supported browsers. As detailed in ESET’s newest Menace Report, Progressive Internet Apps (PWAs) permit direct set up with out requiring customers to grant specific permissions, that means downloads might fly beneath the radar. ESET found this system used to disguise banking malware as reliable cell banking apps.
Phishing/social engineering
Phishing assaults through electronic mail, textual content (or iMessage) and even voice are a standard incidence. They impersonate reliable manufacturers and trick you into handing over credentials or clicking on malicious hyperlinks/opening attachments to set off malware downloads. Apple IDs are among the many most extremely prized logins as they will present entry to all the info saved in your iCloud account and/or allow attackers to make iTunes/App Retailer purchases. Look out for:
- Pretend pop-ups that declare your system has a safety drawback
- Rip-off telephone calls and FaceTime calls impersonating Apple Help or associate organizations
- Pretend promotions providing giveaways and prize attracts
- Calendar invite spam containing phishing hyperlinks
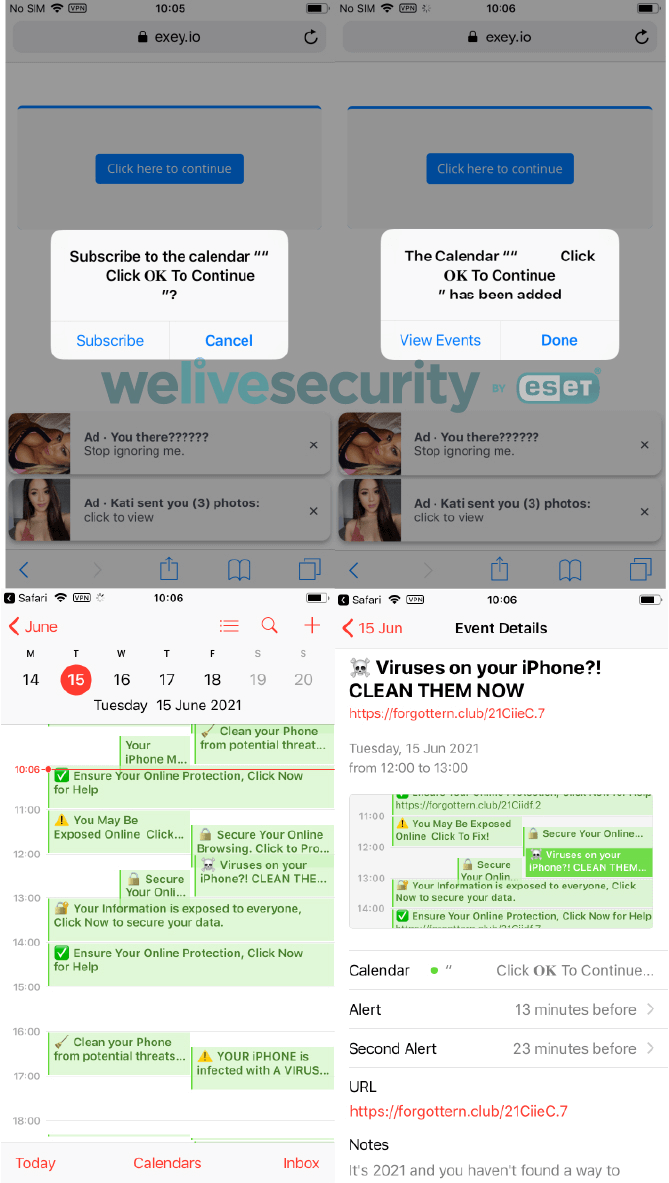
In a single extremely subtle marketing campaign, menace actors used social engineering strategies to trick customers into downloading a cell system administration (MDM) profile, giving them management over victims’ units. With this, they deployed GoldPickaxe malware designed to reap facial biometric information and use it to bypass banking logins.
Public Wi-Fi dangers
In case you join your iPhone to a public Wi-Fi hotspot, beware. It might be a faux lookalike hotspot arrange by menace actors designed to observe net site visitors, and steal delicate info you enter like banking passwords. Even when the hotspot is reliable, many don’t encrypt information in transit, that means that hackers with the best instruments might view the web sites you go to and the credentials you enter.
Right here is the place a VPN turns out to be useful, creating an encrypted tunnel between your system and the web.
Take ESET’s iOS safety guidelines to be taught simply how secure your iPhone is.
Vulnerability exploits
Though Apple devotes a lot effort and time to making sure its code is free from vulnerabilities, bugs can typically creep into manufacturing. After they do, hackers can pounce if customers haven’t up to date their system in time, for instance, by sending malicious hyperlinks in messages that set off an exploit if clicked on.
- Final yr, Apple was compelled to patch a vulnerability which might permit menace actors to steal info from a locked system through Siri voice instructions
- Typically menace actors and industrial corporations themselves analysis new (zero day) vulnerabilities to use. Though uncommon and extremely focused, assaults leveraging these are sometimes used to covertly set up spyware and adware to snoop on sufferer’s units
Staying secure from iOS threats
This may seem to be there’s malware lurking round each nook for iOS customers. That is likely to be true, up to some extent, however there’s additionally loads of issues to attenuate your publicity to threats. Listed below are just a few of the principle techniques:
- Maintain your iOS and all apps updated. It will scale back the window of alternative for menace actors to use any vulnerabilities in outdated variations to attain their targets.
- All the time use robust, distinctive passwords for all accounts, maybe utilizing ESET’s password supervisor for iOS, and swap on multi-factor authentication if provided. That is straightforward on iPhones as it is going to require a easy Face ID scan. It will be sure that, even when the dangerous guys pay money for your passwords, they gained’t be capable to entry your apps with out your face.
- Allow Face ID or Contact ID to entry your system, backed up with a powerful passcode. It will hold the iPhone secure within the occasion of loss or theft.
- Don’t jailbreak your system, for the explanations listed above. It should more than likely make your iPhone much less safe.
- Be phishing-aware. Which means treating unsolicited calls, texts, emails and social media messages with excessive warning. Don’t click on on hyperlinks or open attachments. If you really want to take action, verify with the sender individually that the message is reliable (i.e., not by responding to particulars listed within the message). Search for tell-tale indicators of social engineering together with:
- Grammatical and spelling errors
- Urgency to behave
- Particular provides, giveaways and too-good-to-be-true offers
- Sender domains that don’t match the supposed sender
- Keep away from public Wi-Fi. If you must use it, attempt to achieve this with a VPN. On the very least, don’t log in to any worthwhile accounts or enter delicate info whereas on public Wi-Fi.
- Attempt to stick with the App Retailer for any downloads, to be able to reduce the danger of downloading one thing malicious or dangerous.
- In case you imagine chances are you’ll be a goal of spyware and adware (usually utilized by oppressive governments and regimes on journalists, activists and dissidents), allow Lockdown Mode.
- Maintain an eye fixed out for the tell-tale indicators of malware an infection, which might embrace:
- Gradual efficiency
- Undesirable advert pop-ups
- Overheating
- Frequent system/app crashes
- New apps showing on the house display
- Elevated information utilization
Apple’s iPhone stays among the many most safe units on the market. However they’re not a silver bullet for all threats. Keep alert. And keep secure.











